
BLOG

BLOG
As technology progresses and mobile devices become ubiquitous, a huge number of people worldwide are now using smartphones. Current estimates show that 6.8 billion users rely on their phones for an array of activities, but most significantly, 88% of these are dedicated to app usage!
While the above stats show that the mobile app industry is thriving, it's also a matter of concern. Why?
As the number of mobile apps and their users increases, cyber attacks targeting mobile apps are also growing. Hackers are becoming more intelligent and finding new ways to gain unauthorized access.
Therefore, mobile app developers must take exceptional measures and basic security testing to make mobile apps more secure and resilient to hackers. One such exceptional measure is mobile app threat modeling.
Despite being decades old, mobile app threat modeling is something only some app development organizations practice. However, it's an effective process and can do wonders if combined with regular security testing.
In this blog, we'll dive deeper into the concepts of mobile threat modeling and app security testing, from what these processes are, how they help, and the best practices to enhance mobile app security. So, read in full.
Mobile app threat modeling is a process that companies use to identify vulnerabilities that an attacker could violate to help them prioritize and mitigate threats.
As Microsoft defines,
"Threat modeling is an engineering technique for identifying threats, vulnerabilities, attacks, and countermeasures that could impact an application. Threat modeling helps shape your app's design, meet your organization's security goals, and reduce risk."
While you may think threat modeling sounds similar to regular security testing, it's not. The goals point in the same direction, but the way threat modeling works is unique.
For instance, before development begins, threat modeling helps identify security requirements, pinpoint security threats, and prioritize based on their risk. Other methods, like pen testing, can only be performed when app development reaches a particular stage.
Threat modeling acts as an early warning system in application security. Rather than discovering vulnerabilities during testing or production, threat modeling addresses security issues during the design phase when changes are less expensive and disruptive.
It provides a systematic way to understand your application's security posture, prioritize security investments, and make informed decisions about security controls. Security leaders use it to demonstrate due diligence and justify security investments, while developers gain concrete guidance on implementing security measures.
Here are the common threat types that can make your apps more vulnerable:
Data leakage is a common mobile app security threat wherein hackers access confidential user/business data. This usually happens when the code lacks secure coding practices, encryption, and optimum authentication measures.
Let's say a user enters their name, address, and card information in your app. Hackers can steal and misuse the above information if your app is insecure or lacks basic mobile app security frameworks.
Malware is software or code injected into an application to disrupt an application or gain unauthorized access. Often, hackers reverse engineer popular apps, create a malicious replica of the app, and steal the data of millions of customers. This data is then used for illicit purposes and sold in the black market.
Encryption is the process of encoding data, making it unreadable for anyone who doesn't have the encryption key. This helps conceal confidential information from hackers.
However, several developers use poor encryption techniques or don't use encryption at all, especially for in-transit data. This makes the app susceptible to attacks.
Developers often use several third-party components, such as APIs, libraries, and frameworks, to make development easier. While third-party components do help, they're usually risky, especially if they're coming from unreliable sources. Such features may access confidential information and allow malicious code to run on the users' devices.
The most important aspect/step of threat modeling is identifying threats and prioritizing the potential security risks. Here's how:
Identifying threats or vulnerabilities is quite complex before the deployment, as there are too many touchpoints and vectors. However, building a cross-functional team that includes testers, developers, architects, system admins, users, etc, can help.
Once the team is ready, you can follow the threat identification models given by Microsoft:
This model allows you to break down potential threats into a threat graph. Take a look at this infographic:
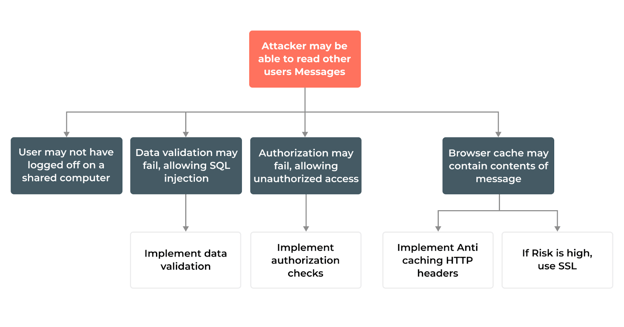
In this approach, you must create a list of who may attack an asset in your mobile application. The potential actors would fall into one of these categories:
You can use one more method besides the two threat modeling example models. And that is performing a code and configuration review. This method will also help you ensure the necessary controls are in place and work as they should.
Here's what you can consider to perform code and configuration review:
Now that you know how to identify potential threats, let's understand how to prioritize them. While there are numerous methods of threat prioritization, two of the most effective threat model examples for threat prioritization are DREAD and STRIDE.
DREAD is a classification framework that helps determine and compare the amount of risk a threat poses. DREAD is also an acronym:
Risk Score = DREAD (Damage + Reproducibility + Exploitability + Affected Users + Discoverability)
A risk score is a number between 0 (zero risk) to 10 (total destruction or compromise)
STRIDE is a goal-based approach where you consider the attacker's goals. Just like DREAD, STRIDE is an acronym that outlines six types of threats and security controls to deal with the same. Here's what STRIDE stands for (potential threat vectors):
While the steps involved in mobile app threat modeling vary from organization to organization, they can be categorized into these three high-level steps:
In this step, you must understand how the app works and interacts with other entities. Here's what this step involves:
This step involves identifying and categorizing the potential threats using the frameworks listed above: DREAD and STRIDE.
Doing this will help you understand the potential vulnerabilities, how they'll be exploited, and the damage they might inflict.
Now, you need to find countermeasures to mitigate the vulnerabilities you've identified in the previous step. Based on the risk they pose, you can:
You can refer to OWASP's official website to learn about these steps in detail.
Here's how you can make the most of mobile app threat modeling:
You need to determine the scope of the analysis with your stakeholders, then break down the analysis's depth with the respective teams.
Create a diagram or any other easy-to-understand visual element that displays the major components of the app that you're threat modeling.
Accurately identify all software assets, threat agents, and mobile app security controls and create a diagram/model. After that, you can identify potential threats by leveraging methods like STRIDE.
To determine the potential threats accurately, ask the following questions:
Consider what path the threat agents will follow and track the same. A potential attack could happen if the threat agent reaches the asset without routing through security control. If the threat agent passes through security control, check if the control can stop the threat agent.
You must update your threat model as new mobile app security risks appear yearly. Not updating will make threat modeling ineffective to new threats, which defies the whole purpose.
Mobile app security testing evaluates or assesses the application security via SAST or DAST scans.
Using security testing, developers can identify potential vulnerabilities in their apps and effectively mitigate them, resulting in a more secure and resilient mobile app.
Vulnerability testing (VA) is a method that helps identify vulnerabilities in an application. Usually, developers run their app through an automated vulnerability assessment solution that scans it for vulnerabilities and reports the same.
Vulnerability assessment is of two types:
Often led by an ethical hacker or a certified security professional, a penetration test is a simulated attack performed on the app to find potential vulnerabilities. The security professional approaches/interacts with the app like an actual hacker and uses automated pen testing tools to find exploitable weaknesses and prevent any actual attacks.
While the actual steps in mobile app security testing might vary, here's what security testing typically entails:
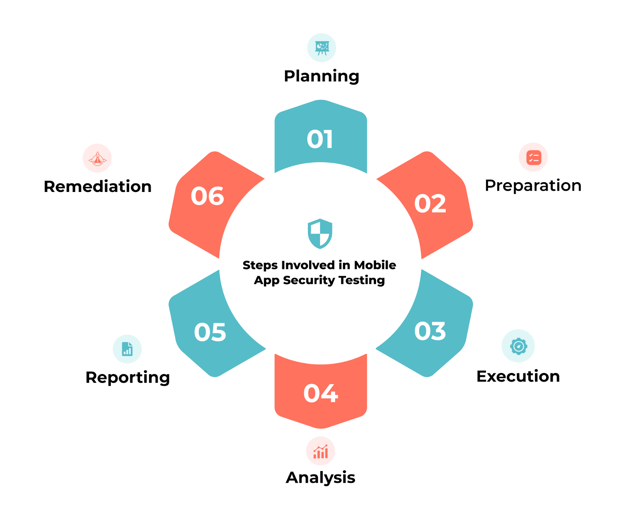
Here's how you can make the most of mobile app security testing:
In addition to manual testing, you should also leverage automation testing, i.e., the use of automated tools. Take Appknox, for example.
With Appknox, you can perform automated vulnerability assessments, including SAST, DAST, API security testing, SBOM, and more, with better accuracy without spending much time and effort. This way, you can save time and perform tests more frequently, making your app more resilient.
Security testing, especially mobile app penetration testing, is a skill-based task that requires a dedicated expert if you seek the best results. So, build a team of qualified experts to improve the effectiveness of security testing.
Open-source or 3rd party components make development easy, but they're equally risky. So, when conducting security tests or looking for mobile app security risks, scrutinize 3rd party components as well.
Developers must consider different ways an attacker might abuse or exploit a feature or app. This way, developers can implement the required security controls before anything happens.
Most companies opt for DAST and penetration testing while ignoring SAST. However, pen testing and DAST happen way ahead in the SDLC, making bug fixing a hassle (as bugs found later are more complicated to fix).
Including SAST early in the SDLC can help you detect code issues in real-time, saving you a lot of time and hassle.
Here's a list of best practices you must follow to minimize mobile app security risks:
The source code is usually available on the client's device. And if the device is hacked, the hackers can access your source code and steal business logic.
So, you should focus on securing the source code. And for this, you can opt for methods such as code obfuscation. It makes the code meaningless and extremely hard for the hacker to understand.
In addition to securing your code, you must encrypt all the data.
While you should always refrain from storing crucial data on the client's device, if you do so, make sure to encrypt it.
The same goes for the data traversing to and from the server. This way, hackers won't be able to decipher even if they access the app.
During development, you must ensure that your app data is isolated from other apps on the user's device. This will prevent any other apps from accessing confidential information and thus reduce instances of data leaks.
Make sure the data is secure when it's being transmitted. Developers can implement code that checks the validity of certificates and offers access to valid users only.
Also, secure protocols such as TLS and GTTPS SSL should be implemented for added security.
One of the most critical security best practices is to monitor and maintain the app regularly. Monitoring helps developers take the required steps should anything mysterious happen and avoid escalation.
Maintaining the app involves updating it and applying security patches to fight new vulnerabilities as they arise, which keeps the app secure for longer.
With the rise of the use cases, mobile apps are becoming more complex, making it hard to implement adequate mobile app security frameworks.
In addition to app complexity, threats or vulnerabilities are also rising. Hackers are finding new methods to gain access or perform data breaches.
However, developers can get the upper hand by staying ahead of the latest security trends by:
By staying up-to-date and informed about the latest developments in the industry, developers can implement the necessary measures and ensure better security.
Where threat modeling is performed during the design phase of the SDLC and helps fix design flaws that lead to security issues, security testing helps deal with bugs (that cause a security threat) before the app goes into production. Ideally, this combination helps perform an end-to-end test on the mobile app and make it as secure as possible.
However, while combining mobile app threat modeling and security testing does help boost security, it should be an ongoing process.
With the rapidly evolving mobile app landscape, risks are growing too. So, developers must be vigilant and make the necessary changes/updates to enhance security as and when required.
Threat modeling for mobile applications is a structured approach to identifying and evaluating potential security risks in mobile apps. It examines how an application handles, stores, and transmits data, then identifies ways attackers might compromise these processes.
Threat modeling creates a security blueprint for your application by mapping components, data flows, and trust boundaries and then methodically identifying vulnerabilities. This includes examining device permissions, local storage, and interaction with platform APIs for mobile apps.
Threat modeling and security testing serve different purposes and occur at different times. Threat modeling is a proactive, design-phase activity that identifies potential threats before writing code.
Security testing verifies whether specific vulnerabilities exist in the implemented code. For example, threat modeling might identify that sensitive data could be exposed in device logs, while security testing would verify whether this exposure exists in the app.
You can leverage threat modeling to uncover potential threats or vulnerabilities in your mobile app or system. To do threat modeling, you must identify potential threats, analyze their impact, and determine how likely that threat can occur. This way, you can find and mitigate issues based on priority and make your app more secure.
To create a threat model, you need to identify the assets (app, data) that need protection and what they need protection from, i.e., potential threats. After that, you can analyze the impact of those threats, determine their likelihood of occurrence, and deal with them effectively.
While the higher level threat modeling involves three steps (decomposing the app, identifying and prioritizing the threats, and mitigation), you can break the process further for ease of implementation:
Developers should begin threat modeling during the design phase before coding starts. Make it a required part of design reviews and create mobile-specific templates to streamline the process. Track security requirements from threat modeling in your issue-tracking system alongside other development tasks. Schedule regular reviews for new features or significant changes and collaborate with security and development teams throughout the process.
Start by mapping your application's architecture and data flows through detailed diagrams. Follow a structured process: identify assets, document entry points, and trust boundaries, enumerate threats, and prioritize risks based on impact and likelihood. Include both security experts and developers in threat modeling sessions. Keep models updated when features change and maintain clear links between identified threats and implemented security controls.
Implement threat modeling early in the development lifecycle. By breaking down the mobile app architecture—data flows, entry points, insecure APIs, and third-party dependencies, you can understand where attackers are most likely to exploit weaknesses.
Frameworks like STRIDE help categorize threats, while DREAD or similar risk-rating models help prioritize them based on potential impact and likelihood.
OWASP mobile security checks should be embedded into the development and release workflow. MAP OWASP MASVS and MSTG controls to different stages of the SDLC.
Run static analysis during development, dynamic testing during QA, and penetration testing before major releases.
Automating these checks within CI/CD pipelines helps catch issues early, while periodic manual testing validates complex attack scenarios.
Clear ownership, consistent testing cadence, and remediation tracking are key to ensuring OWASP checks translate into measurable security improvements.
Point-in-time security testing shows what’s broken today, while trend analysis reveals how security posture is evolving.
Dashboards that track vulnerabilities across builds and releases help you identify recurring issues, measure risk reduction, and prevent regressions.
Appknox’s CISO Dashboard turns fragmented test results into living intelligence that leaders can use for trend analysis. With real-time feeds from CI/CD, compliance tracking, and remediation progress all in one place, security leaders can:
