BLOG

BLOG
The Software Development Life Cycle (SDLC) provides a systematic framework for developing and maintaining software from conception to modification, producing high-quality software that meets stakeholder and customer requirements within specified time and cost constraints.
However, traditional SDLC practices fall short of ensuring thorough application security. Why?
|
Because it lacks the “shift-left approach,” which incorporates security into the first stage of app development rather than making it an afterthought.
Tending to vulnerabilities later in development comes with a heavy price. IBM research shows that the average US data breach cost is approximately $9.44 million!

So, what’s the solution?
Integrating security into DevOps is the key to fighting increased cyber threats throughout the software development lifecycle. This approach helps identify and address vulnerabilities before they become costly later in the development cycle.
Before we discuss secure SDLC in detail, let's first understand why the SDLC approach is now history.
SDLC, short for Software Development Life Cycle, helps software development teams divide the work required to build a system into predictable and structured stages.
The SDLC methodology helps developers create secure and valuable software, devices, or systems and provides a robust foundation for various development tasks. Adhering to the SDLC methodology can enhance software integrity, project visibility, resource management, and execution tracking.
Watch this webinar to learn about incorporating the best application security early in your SDLC.
Incorporating Mobile App Security Into the Development Lifecycle Without Friction
Traditional SDLC practices do not help with quick vulnerability detection and remediation.
Over the past decade, the number of vulnerabilities has increased, as has the cost of data breaches. IBM researchers have found that data breaches with a lifecycle exceeding 200 days had the highest average cost, at $5.46 million.
Usually, when an app is being developed, after the coding stage, it is sent to security researchers for testing. In 2023, GitLab’s report stated that 50% of security professionals reported that developers fail to identify 75% of vulnerabilities in their code.
So, it is crucial to act fast to identify a breach and contain it effectively.
While SDLC provides a structured framework for managing software projects, it fails to meet modern requirements.
Halve your time-to-market with Appknox’s holistic, binary-based mobile application security analysis.
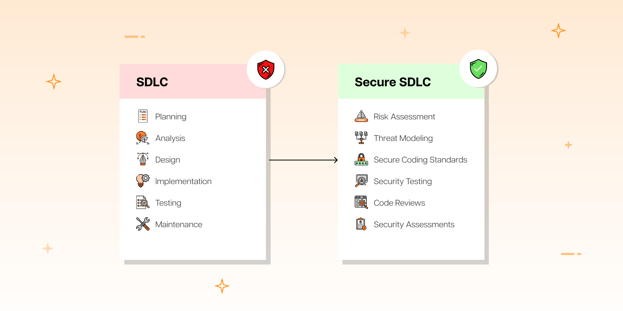
Secure Software Development Life Cycle (SSDLC) is a comprehensive framework that integrates security into every phase of the software development process.
SSDLC ensures that security is considered and implemented from the initial planning and requirements stages through design, implementation, testing, deployment, and maintenance.

Secure SSDLC involves
These practices create a proactive security posture where security concerns are continuously addressed. This improves the overall quality and security of the software and aligns with compliance requirements.
By keeping security as the primary focus, SSDLC significantly reduces the likelihood of vulnerabilities, minimizing the cost and effort required for remediation. It also fosters a culture of shared security responsibility among all stakeholders involved in the project.
Secure SDLC enhances SDLC by embedding security into each development phase.
This proactive approach includes
 Additionally, SDLC emphasizes continuous monitoring and updating of security measures even after deployment, ensuring swift remediation. This proactive approach to security aligns with compliance requirements such as OWASP, NIST, and more, leading to greater trust and satisfaction.
Additionally, SDLC emphasizes continuous monitoring and updating of security measures even after deployment, ensuring swift remediation. This proactive approach to security aligns with compliance requirements such as OWASP, NIST, and more, leading to greater trust and satisfaction.
According to a report by Standish Group, about 70% of projects fail to be completed on time and within budget due to unplanned project initiation, lack of resources, and technical challenges.

Secure SDLC methodologies help streamline software development as it can:
One key benefit of SSDLC approaches is their significant contribution to enhancing product quality. By implementing structured and iterative software development processes, SSDLC promotes early defect detection, creating high-quality software products.
This detection will help you identify problems at their source and mitigate the risk of failure early on.
Secure Software Development Life Cycle (SSDLC) models encourage thorough planning that clearly defines goals and objectives before initiating a project, improving project management in software development.
This approach ensures a comprehensive understanding of the software development scope, objectives, and requirements from stakeholders and customers.
It helps improve project management for developers by:
Moreover, it helps project management for stakeholders by:
Secure SDLC is designed and meticulously developed to mitigate any risk involved in the software development process.
There are different types of testing in SSDLC:
The secure SDLC process promotes collaboration and communication between stakeholders, which drives project development success and reduces the chance of failure.
The communication methods involved in secure SDLC are

Depending on the secure SDLC model, teams can respond appropriately to changing market conditions and evolving customer requirements.
This flexibility in secure SDLC models allows for quick adaptation and implementation of changes, making the project more responsive, efficient, and aligned with customer needs. It divides the project into multiple increments, such as ‘sprints.’
.png?width=680&height=624&name=Secure%20SDLC%20Scrum%20Process%20(1).png)
Secure SDLC integrates security best practices and tools into SDLC and ensures security assurance through activities like architecture analysis, penetration testing, and code review as an integral part of internal architecture. As a result, it helps to discover security bugs as soon as possible.

While understanding secure SDLC is essential, it is also important to understand the steps involved in implementing it in your organization.
We’ve detailed action points for each implementation stage that you can replicate.
1. Adopt DevSecOps:
2. Secure design practices:
.png?width=666&height=799&name=Implementation%20Support%20of%20Security%20Design%20Patterns%20Using%20Test%20Templates%20(1).png)
3. Secure coding practices
Use this template to implement secure code best practices to push secure code in every deployment.
4. Automated security testing
5. Dependency management
6. Continuous security monitoring
7. Security training and awareness
8. Collaboration between teams
9. Compliance and governance
10. Post-deployment security
Level up your DevSecOps game with our expert-curated checklist
Grab your free SSDLC best practices checklist.
Download now!
Appknox, a leading enterprise-grade mobile app security platform, integrates seamlessly with the application development lifecycle to ensure security at every stage.
.png?width=680&height=637&name=Mind%20map%20for%20DevSecOps%20(3).png)
By integrating Appknox into the mobile app development lifecycle, developers can ensure robust security and compliance throughout the development process, from discovery to maintenance. This integration helps identify and mitigate vulnerabilities early on, reducing the risk of breaches and heightening the overall security posture of the mobile application.
So, with Appknox, you can accelerate your time-to-market by 50%.
Check out how a built-for-mobile VA tool can amplify the visibility and control of your app security framework.
Most software developers believe that the Agile module is the best SSDLC model. It focuses on adapting to changing market conditions and requirements by combining an incremental and iterative approach.
Choosing the right one from multiple secure SDLC methodologies depends on the following:
You can make your SSDLC model more flexible by:
1. Choosing agile methodology
Agile methodologies such as Scrum, kanban, or XP are based on collaboration, communication, feedback, and continuous improvement principles. They allow you to respond to changes quickly and deliver value to users.
2. Using a hybrid approach
A hybrid approach combines elements from different models.
For example, a waterfall model can define the software development project's scope, objectives, and requirements for the initial planning and analysis phases. After this, you can switch to an agile model for the design, implementation, and testing phases to iterate and refine the software based on user feedback.
3. Apply DevOps practices
You can apply DevOps practices to integrate the development and operations teams and processes. These practices includeThese practices will help you streamline the software development and deployment processes, reduce errors and bugs, and increase collaboration and feedback.
