
BLOG

BLOG
Previously we spoke about Vulnerability Scanning and its common misconceptions. Today we are going to talk about the top cyber security vulnerabilities that are exploited by cybercriminals.
Before we proceed ahead, first let's get to know what the term 'Cybersecurity Vulnerability' means?
In Information security, a vulnerability is a weakness which can be exploited by a Threat Actor, such as an attacker, to perform unauthorized actions within a system.
Vulnerabilities are the intersection of three elements:
- a system susceptibility or flaw,
- attacker access to the flaw, and
- attacker capability to exploit the flaw.
To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. In this frame, vulnerability is also known as the attack surface.
NOTE: Often a security risk can be incorrectly classified as a vulnerability. Usage of the term vulnerability along the same lines with that of risk can lead to confusion. A security risk is the potential of a significant impact resulting from a vulnerability exploitation. Then there are vulnerabilities without risk: for instance when the affected asset has no value.
A vulnerability with one or more known instances of working and fully implemented attacks is classified as an exploitable vulnerability—a vulnerability for which an exploit exists. (Source)
A new report from Recorded Future found out that cybercriminals exploit kits and phishing campaigns favored Microsoft products in 2017, with 7 of the top 10 cyber security vulnerabilities exploited by phishing attacks and exploit kits utilizing Microsoft products.
The research highlighted the challenges that defenders face to make remediation decisions around these vulnerabilities without having access to all the facts.
Official vulnerability databases and even scanning tools cannot arm organizations with one key metric: the overlap between the vulnerabilities in the systems you use and the ones that are being actively exploited by threat actors.
The cyber threat analysis identified a shift in the preferences of cybercriminals from Adobe to Microsoft consumer product exploits. These sources were analyzed from January 1, 2017 to December 31, 2017 and they identified that Adobe is still a popular but declining avenue of attack, with the remaining three vulnerabilities tied to the aging Flash Player.
The reason of the change was due to the evolving criminal use of exploited vulnerabilities. Overall, exploit kits are declining as criminal efforts have adapted. This comes as cryptocurrency mining malware popularity rose in the past year. Previously we mentioned how this trend would continue ahead as 2018 is touted to be year of cryptojacking. We saw glimpses of it when the popular electric car company, Tesla got attacked by Cryptojackers where the attackers performed cryptojacking to use Tesla’s cloud compute resources to perform crypto mining.
Profiting from cryptocurrency mining has its advantages, including less time spent on collecting victim ransomware payments and the avoidance of rising Bitcoin transaction fees.
1) Microsoft products provided seven of the top 10 vulnerability exploits adopted by exploit kits and phishing campaigns. This is in stark contrast to Record Future's previous rankings (2015, 2016) which saw consistent targeting of Adobe Flash exploits.
2) For the first time, three vulnerabilities remained on the list. For example, the top exploited vulnerability from 2016, CVE-2016-0189 in Microsoft’s Internet Explorer, remained a popular in-road for criminals. Dark web conversations highlighted a lack of new and effective browser exploits.
3) In 2017, exploit kits saw a 62 percent decline in development. Only a few exploit kits, including AKBuilder, Disdain, and Terror saw significant activity. Multiple factors, including more specific victim targeting, shifts to more secure browsers, and a rise in cryptocurrency mining malware likely led to the decline.
4) Dark web forums and marketplaces continued to offer high and low-quality exploit kit options, with prices ranging from $80 per day for services, to $25,000 for full source-code access.
5) Exploit builders for top-ranked Microsoft Office vulnerability CVE-2017-0199 ranged from $400 to $800 in 2017.
The goal of this annual cybersecurity vulnerability list is to provide an account of the most widely adopted vulnerability exploits.
Previously, their measurement was focused exclusively on exploit kits, as the criminal market demands continual adoption of exploits for unpatched vulnerabilities. This year, they included phishing attacks and vulnerability co-occurrences to provide a more comprehensive look at criminal attack vectors.
The annual list of the top cyber security vulnerabilities and associated malware can be found below:
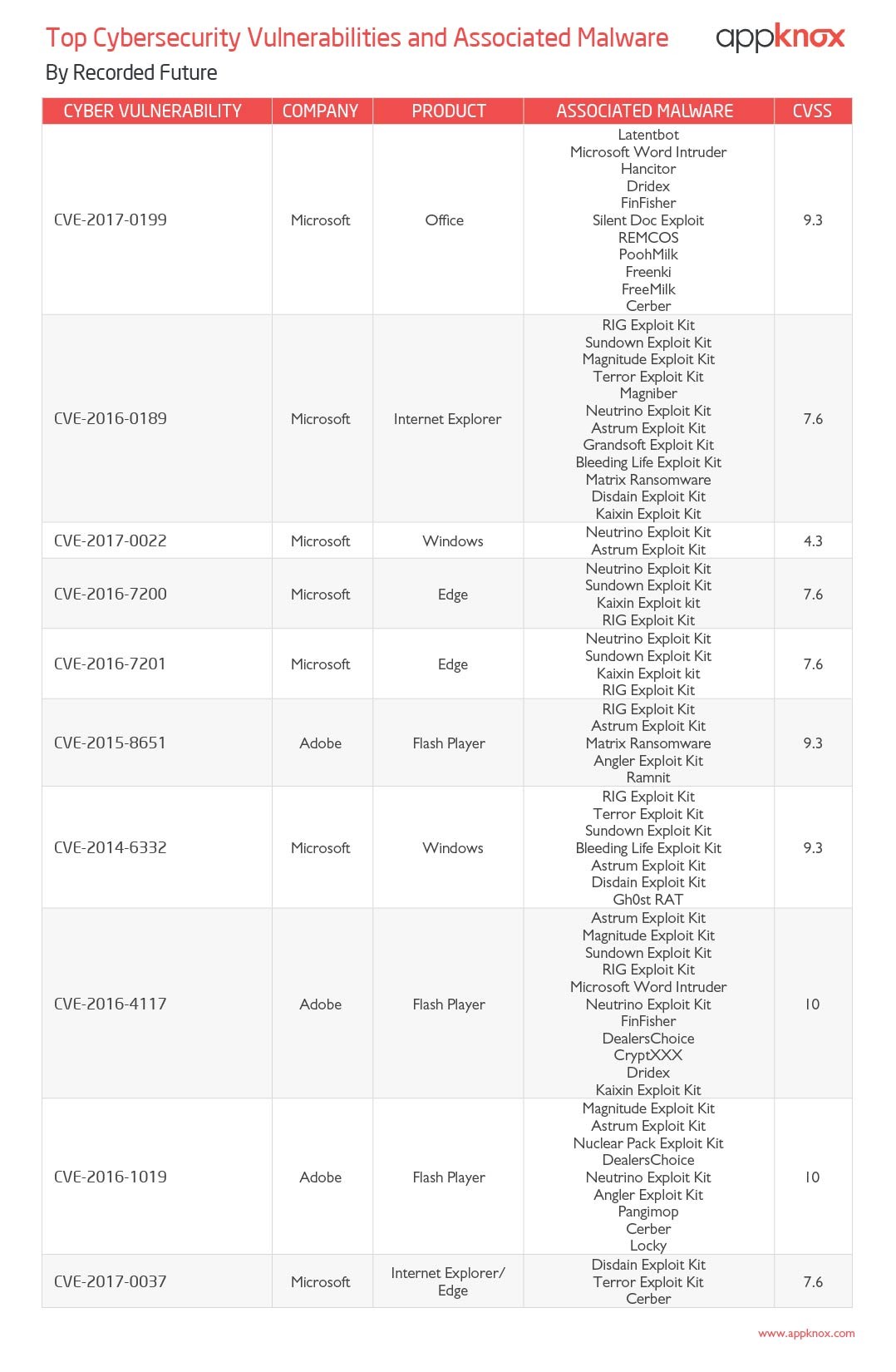
NOTE: For the uninitiated, here what the terms CVE and CVSS means -
1) CVE stands for Common Vulnerabilities and Exposures. It's a list of entries—each containing an identification number, a description, and at least one public reference—for publicly known cyber security vulnerabilities.
2) CVSS stands for Common Vulnerability Scoring System. It provides a way to capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity. The numerical score can then be translated into a qualitative representation (such as low, medium, high, and critical) to help organizations properly assess and prioritize their vulnerability management processes.
Lastly, the report recommended the following actions to be undertaken by organizations and end users:
1) Prioritize patching of all the vulnerabilities identified in this report.
2) Remove the affected software if it doesn’t impact key business processes.
3) Consider Google Chrome as a primary browser.
4) Be aware that Facebook and other social media sites use Flash technology and users frequently enable Flash to run on these sites.
5) Utilize browser ad-blockers to prevent exploitation via malvertising.
6) Frequently backup systems, particularly those with shared files, which are regular ransomware targets.
7) Deliver user training to encourage skepticism of emails requesting additional information or prompting clicks on any links or attachments. Companies will not generally ask customers for personal or financial data, but when in doubt, contact the company directly by phone and confirm if they actually need the information.
.jpg?width=50&height=50&name=10606600_10204086667262761_7381430219125488912_n%20(1).jpg)
Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
