
BLOG

BLOG
As per Statista, mobile apps are estimated to generate over $935 billion in revenue in 2024, which includes:
This means businesses must prioritize mobile app testing and security posture to safeguard users' personal and financial information from security breaches.
For successful mobile app testing, your team must test the app through numerous operating system versions, network bandwidths, screen resolutions, and devices—to ensure the app performs seamlessly across devices.
However, manual penetration testing is time-consuming. So, it has limited scalability due to the wide range of platforms and devices to test. This is where mobile app testing tools, with automation, speed up the security testing process, enabling the early detection of frauds and errors.
If you’re looking for the best mobile application security testing tools for your mobile application to help you secure user data, preserve the app’s integrity, and identify and analyze vulnerabilities in applications used with your mobile platforms during or post-development, you are in the right place! This blog will share the best mobile app security testing tools, their key features, and pros and cons to help you decide the best fit for your business.
|
Let’s first understand how cracks might develop in your apps, making your data and users vulnerable to cyber thefts and attacks.
Apps collaborating with suppliers and resellers are often coded using third-party software libraries and software development kits (SDKs). These may contain malicious code that infects your app and leaks sensitive information to the fraudster.
It compromises user privacy and company data, enables unauthorized access to data and denial of service, and may take over the app altogether.
Weak or misconfigured authentication mechanisms and password policies, insecure credential transmission, and improper session management may provide unauthorized access to hardcoded credentials.
The impact of authentication vulnerabilities includes access to all data and functionalities of the compromised accounts. If the attacker bypasses the authentication of a high-privilege account, such as a system administrator, they could even take control of the application and gain access to internal infrastructure and information.
Even access to a low-privilege account can grant the attacker access to commercially sensitive business data or allow access to additional pages, providing a further attack surface.
Third-party malicious actors can eavesdrop on network communication, access clipboards, or use trojans to access unsecured PII, which includes names, addresses, financial details such as credit card numbers, email addresses, IP addresses, health information, religion, sexuality, etc.
Injection attacks, such as SQL, command, and CSS attacks, allow external data to enter the network without sufficient validation, making the app extremely vulnerable to data breaches.
To prevent such app vulnerabilities, it is essential to use secure coding practices, review code, and continuously test throughout the app development lifecycle.
Mobile application security assessment is a proactive approach to identifying security-critical vulnerabilities and weaknesses in mobile apps. As organizations continuously release new apps and update current ones, MAST has become the bedrock of enterprise security.
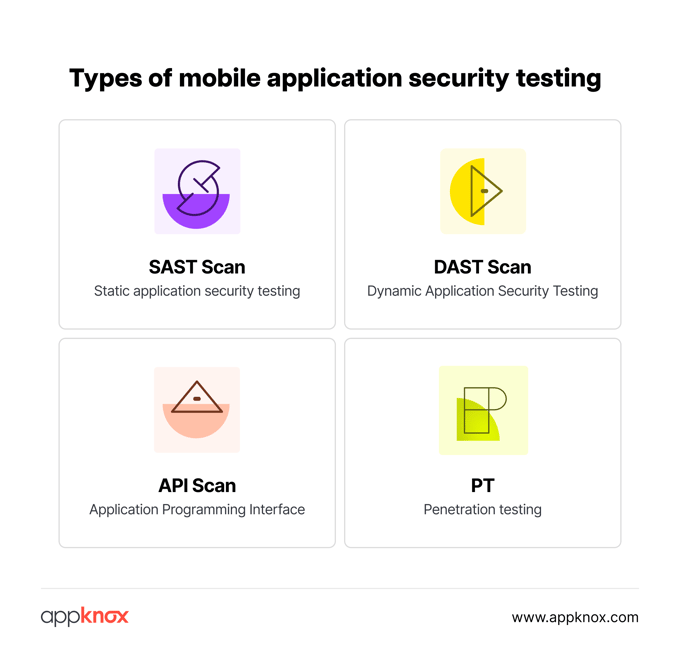
The SAST process evaluates the app’s source code, bytecode, or binary code without executing the program. This method effectively detects security vulnerabilities like code injection, insecure authentication methods, and other source code vulnerabilities before the app is released to the public—when these errors are the cheapest to fix.
In the software development lifecycle (SDLC), static application security testing is integrated into the Continuous Integration/Continuous Development (CI/CD) pipeline, allowing developers to code, test, edit, and test the static code to ensure the software is free of vulnerabilities.
The benefits of SAST testing include:
DAST is a black box app security testing simulator that simulates external attacks to detect weaknesses and vulnerabilities in the app’s architecture.
The dynamic application security testing analysis detects conditions indicative of a security vulnerability while in its running stage, which means it comes into play in the SDLC even in the initial development stage. You can observe how the app behaves in the HTTP environment and try to simulate attacks from an attacker’s perspective.
This type of testing focuses on the application's dynamic or run-time characteristics, including encryption, memory, permissions, performance, and back-end code injection.
The benefits of DAST include:
API security is no longer the sole responsibility of cloud service providers. You must use mobile app security testing tools to perform deep scanning and threat analysis to ensure your app ecosystem remains impenetrable or unexploitable.
Mobile app API security includes:
APIs are the easiest entry points for hackers, and any unpatched vulnerability can lead to data leaks and malware assaults. So, API security testing involves conducting multiple scanning processes to test an application's server side for exploitable flaws and vulnerabilities.
Penetration testing for mobile apps to detect security vulnerabilities ingrained in the app’s infrastructure. These attacks are performed both internally and externally to identify potential vulnerabilities.
The mobile pentesting process involves five steps:
Preparation: Preparation includes defining the scope of security testing, the organization’s goals, and identifying the applicable security controls and sensitive data.
Intelligence gathering: Intelligence gathering analyzes the app's environmental and architectural context to gain a deeper understanding.
Mapping the application: This step involves manually exploring the app or automated scanning to understand the app, its entry points, the data it holds, and its vulnerabilities. The security tester can rank vulnerabilities based on the damage their exploitation can cause and create test cases for test execution.
Exploitation: To determine whether the vulnerabilities are real and true positive, the security tester tries to penetrate the app by exploiting previously identified vulnerabilities.
Reporting: In this phase, the security tester reports details regarding the vulnerabilities exploitation process, classifies the type of vulnerabilities, and documents the risk if an attacker would be able to exploit the target and which data the tester was able to gain illegitimate access to.
The market is flooded with several mobile app security testing tools. So how do you decide on the one that is right for you? Here are some points that you must evaluate:
Start with an in-depth evaluation of the tool’s features and compatibility with iOS and Android. Look for essential features and functionalities like SAST, DAST, penetration, and API testing capabilities.
In addition, the tool should support both native and hybrid apps. It should also be able to identify security issues with
Vulnerability scanning identifies the commonly known vulnerabilities and loopholes by cross-checking a comprehensive database within software dependencies. These matches are reported to the development team or DevSec. Look for a vulnerability scanning tool that integrates vulnerability scans in a CI pipeline.
While static analysis helps you identify vulnerabilities in the code during the early stages, dynamic analysis identifies vulnerabilities that occur during runtime.
A comprehensive mobile app security testing tool should have a dynamic application security testing tool and a static analysis security testing tool, along with vulnerability assessment and compliance testing.
Code scanning in the security testing tools analyzes the app’s source code for potential vulnerabilities, coding mistakes, adherence to SQL, cross-site scripting (XSS), and improper input validation.
Penetration testing helps identify common vulnerabilities like weak authentication, insecure API endpoints, and privilege escalation that may not be easily detected through automated testing tools. It incorporates human expertise to breach the app’s defenses and identify areas that malicious attacks may exploit in the app.
While automated testing/ vulnerability scanning might generate false positives, penetration testing provides a more precise understanding of the location of the loopholes.
Risk assessment can mitigate potential risks associated with insider threats in the event of a cyberattack.
Posture assessment evaluates the current state of the app’s security to reveal information compromised during an attack, its potential impact on business operations, estimated recovery time, and preventative measures.
Risk and posture assessment complement each other and share the goals of
Choose a security testing tool for your mobile app that easily integrates with your CI/CD pipeline and tech stack to ensure that security checks are consistent across every code change and build.
Automation allows you to catch vulnerabilities early, reducing the risk of introducing new security issues and accelerating the delivery of mobile apps.
The right vulnerability scanner must have an easy-to-use interface and clear user instructions. A tool that lacks this feature will reduce the security team’s efficiency despite its advanced features.
Large enterprises with enterprise-grade apps need a scalable security testing tool that can handle high test loads without a high false-positive rate.
A good mobile application security testing tool must have robust reporting abilities to generate multiple reports and identify gaps in an application’s security framework.
The ideal security testing tool must comply with the best industry regulations and practices and generate detailed reports to identify issues for various compliances, such as OWASP, NIST, and HIPAA. It must also flag the severity of the issue and potential consequences and outline action-oriented remediation measures.
The pricing of a mobile app testing tool directly influences your company’s budget and resources. Since pricing depends on factors like features, capabilities, and licensing options, the pricing model must align with the project's specific needs.
Based on the above criteria, we have prepared a list of five top mobile app security testing tools with a brief overview, features, pros and cons, and pricing to help you make the right decision.
Appknox is a mobile-first binary code vulnerability assessment and penetration testing tool. With powerful capabilities, it covers 140+ automated SAST, DAST, and API vulnerability test cases for mobile applications.
What sets Appknox apart from other mobile app security testing tools is that it is a fully automated DAST with testing performed on real devices instead of emulators. With just one click, you can get detailed reports with CVSS scores.
Recognized by Gartner, Appknox empowers security teams to configure and efficiently run manual pen tests, consolidate vulnerabilities, and scan the mobile app's binary in less than 60 minutes.
Astra Security provides a comprehensive hacker-style penetration test with automated and manual pentesting. Astra’s offerings include a continuous scanner, vulnerability management, and a personal security assistant bot. The intuitive dashboard empowers DevSec teams to monitor real-time vulnerability tests and operations.
Veracode’s mobile app testing security solution is tailored to incorporate app security into the development process, enabling developers to address security concerns on the go to address your AppSec requirements.
NowSecure provides automated mobile app security testing for Android and iOS and can test any mobile app language or framework. Its Portfolio Health Dashboard offers a holistic view of your mobile AppSec program and shows actionable security risk analytics.
Platforms supported: Android and iOS
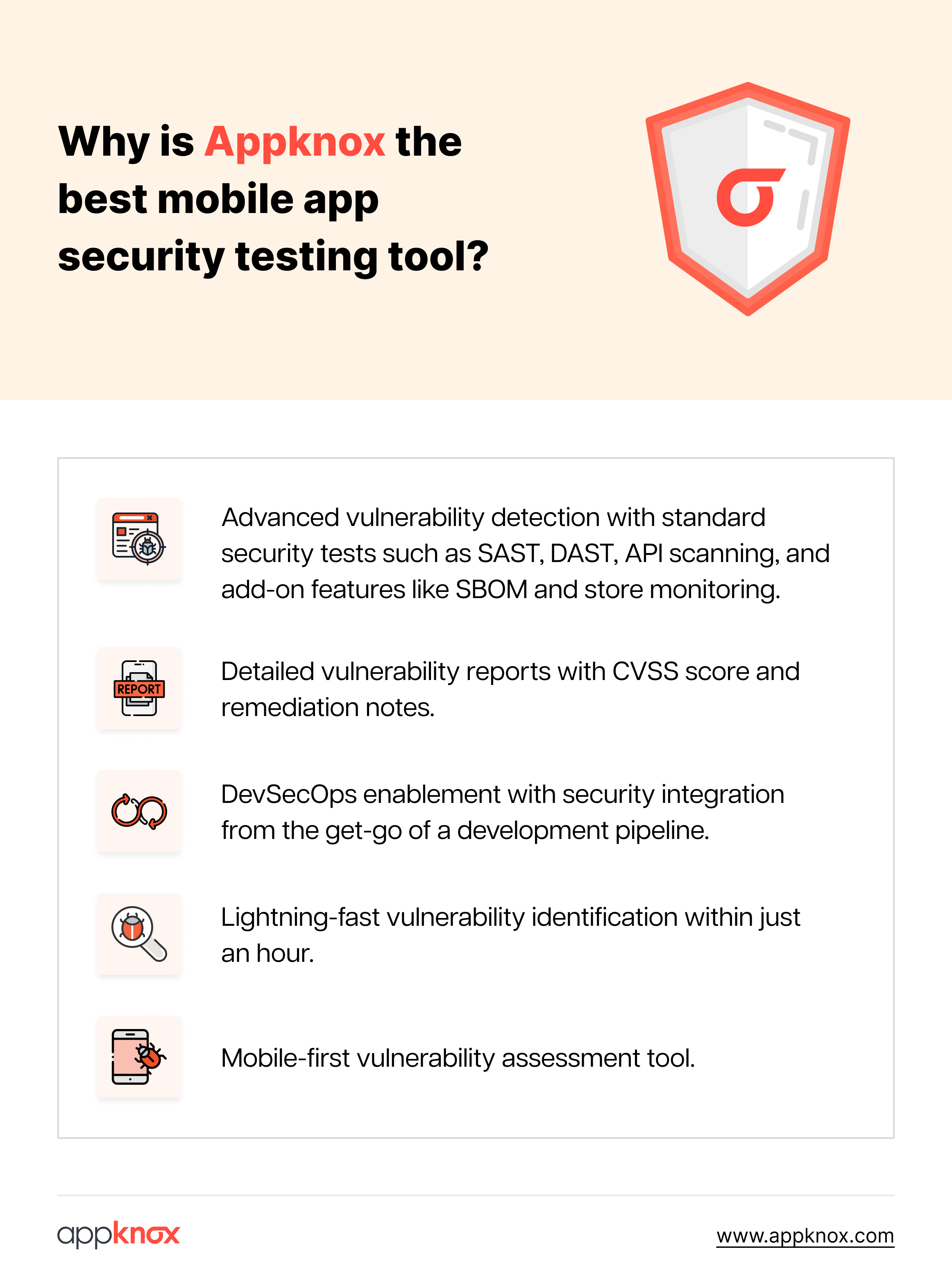
As our top recommended app security testing tool, Appknox provides numerous advantages over other tools, such as:
The best approach is to prioritize security needs. For example, do you want to improve the DevSec process or meet various compliance requirements?
Appknox is a mobile app security testing tool worth considering due to its robust vulnerability scanning capability and near-zero false positives. As a mobile app security testing tool, Appknox takes care of all security needs from code to compliance.
To learn more about the Appknox platform, request a free trial.

Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
