
BLOG

BLOG
Organizations are often anxious about selecting the best security assessment technique for their business. Their concern is strongly justified by the exponential rise in security breaches in the recent past.
As a result, worldwide spending on cybersecurity is expected to cross $133 billion by 2022.
In order to successfully fight against the evil intentions of hackers, it is necessary to follow the best security assessment techniques. And as the cybersecurity landscape evolves, the number of such techniques is also increasing.
Every cybersecurity expert must have faced this question prior to performing pentesting or red teaming? More often than not, organizations tend to treat penetration testing and red teaming as if they were the same thing, but they are certainly not.
Despite some fundamental similarities, both have several differences when it comes to the underlying approach and intent. Let’s take a look at some of the key differences between penetration testing and red teaming based on some of the most common cybersecurity scenarios.
Penetration testing aims at assessing a network, system, web app or any other resource so as to detect as many configuration issues and vulnerabilities as possible. Testers looking through the eyes of threat actors later exploit these vulnerabilities and find out the level of risk behind them.
Generally, pen-testers do not aim at discovering new vulnerabilities. Instead, they aim at finding and exploiting the already known but unpatched security issues. Penetration testing also ensures that the discovered vulnerabilities are not false positives. Not to mention, pen-tests do not focus on stealth or evasion or the ability of the organization’s security team to counter back, as they are already aware that the testing is being done.
Good Read: Best Penetration Testing Tools for Security Assessment
When it comes to choosing the mode of testing, experts mostly recommend manual penetration testing over automated testing as it covers a wide array of potential threats. At the end of the test, the pen-testers produce an assessment report which covers all the details about the vulnerabilities and the level of risk they pose. The report also explains how the testers exploited the systems and the loopholes that were present.
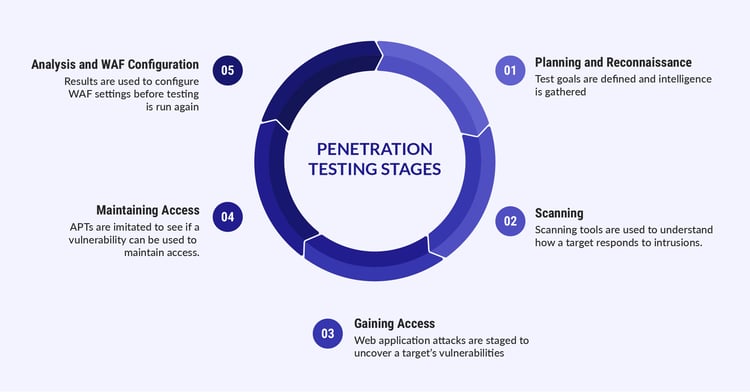
A Red Team assessment or Red Teaming, on the other hand, has certain targeted motives. Instead of finding as many vulnerabilities as possible, a red team tries to test how the organization’s security team responds as they make a move. The Red Team tries to gain access to sensitive information quietly and in any way possible, avoiding any chance of detection.
Mostly, the Red Team assessments have specific objectives and they involve a lot more people than penetration testing. Taking more time and utilizing more resources, they tend to deeply understand the level of risk security vulnerabilities might pose to the organization’s critical assets.
Employing red teaming is typically considered a very mature or sophisticated security measure. After penetration testing patches most of the serious vulnerabilities, Red Team assessments take matters to the next level. Red Teams then try to gain access to the system and test its defenses. In one way or the other, they look for any way to breach the security barriers, if possible.
Red Teamers generally carry out their actions by confronting social engineering attacks or planting hardware trojans and look for ways to further exploit these vulnerabilities. They would later compromise the apps or networks and other physical controls to cause further escalation.
After the Red Team assessment, your organization’s security team gains sufficient insights on how to remediate or fix the existing vulnerabilities and respond appropriately in the future.
Penetration testing has been the trusted security measure for a long time. However, due to time and scope related constraints, something with a more specific perspective is also required at times. Red Team assessments overcome the limitations of penetration testing and provide a full-proof way of recreating actual threat scenarios by exposing serious attack surfaces.
Sometimes it's better to completely simulate the real-world threat scenario. And that's what Red Team engagements do. They take your organization's security teams as close to a real security incident as they could. Penetration testers, on the other hand, are more inclined towards finding vulnerabilities. But, they aren't as focused on achieving specific security goals as Red Teamers are. Moreover, they don't check your organization's response or preparedness in case of an actual attack.
As talked about earlier, Red Team assessments have rather specific objectives. But, why stress on specificity so much? It's because of the reason that nowadays many organizations are more inclined towards safeguarding some specific business outcomes more than others.
Health organizations may be more concerned about their patients' health-related data. Banking institutions might care more about their customers' accounts and card related information. Red Teams safeguard all these specific business goals without any constraints. They help businesses stay on their toes when it comes to facing any adverse situation.
Employing a Red Team assessment not only helps organizations in highlighting critical vulnerabilities but also use the test information to educate the end-users regarding more safe practices and increase their security awareness. Moreover, understanding your enemy's motivations better also puts you one step ahead of them. You can disrupt your enemy's actions anytime and show them their real place.
Penetration tests have been trusted by mature organizations for a long time. They not only allow your organization to plan and strategize your critical security investments but also clear the picture on why you actually need to invest in security. Identifying and later exploiting vulnerabilities not only paints a clear picture of the underlying threats but also portrays the level of damage that can be caused if the attackers get hold of the critical user information you were trying to protect.
Avoiding detection, Red Teaming assessments also do a similar job. Moreover, they emulate real-world cyber-attacks more genuinely and dig even deeper as compared to pen-tests. Red Teamers exactly portray what a real attacker would do so as to let the organization's security team know where they stand.
Red teams initially conduct off-site reconnaissance like real hackers using whatever sources they can use. They later decide what organizational targets to focus on. The targets might include physical targets like worksites, externally exposed components like internet servers, or even the organization's own employees. Once the Red Teamers gain a foothold, they move to the later stages of their engagement and attempt to test the security on as many levels as they can.
Overall, Red Teaming can be considered as one of the most extensive and in-depth methods to determine the level of security an organization currently has in place. By deeply reflecting on the most sophisticated security loopholes, Red Team engagements pave way for a much more comprehensive security system.
In the battle between Penetration Tests and Red Team assessments, no clear winner can be identified. They are simply one of the best testing procedures in their own specific scenarios. However, you certainly need to make a choice when you have to choose between stealth and detailed exploration.
You would never choose to conduct a penetration test to assess your incident response. Similarly, you would never choose to perform Red Team assessment if you wish to explore vulnerabilities in detail. A better choice, however, will be to identify the right situation and employ the test method which best suits your needs.
What you should read next >> How to Perform Manual Pentest on Mobile Applications

Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
