
BLOG

BLOG
With the huge growth in mobile computing over the last decade, it has become a major target for hackers looking for ways to steal information. Even Google isn't immune to these types of attacks.
An important piece of keeping your apps and other online resources secure is to do penetration testing on them. If you're not performing pentesting, there could be vulnerabilities that you don't know about - and that hackers could end up exploiting.
Let's look at what pentesting is and how it helps keep you safe.
Penetration testing, or pentesting, is a simulated attack on your mobile app, web server, firewall, or other online resources. "White hat" or ethical hackers carry out these attacks and report everything they find back to you so your IT staff can shore up any vulnerabilities.
Pentesting can happen with the full knowledge of the target's security staff, allowing them to work together with the testers. This allows them to see the attack in real-time and work through different possible scenarios as they go.
In other cases, penetration tests happen without the knowledge of the target's security staff. The tester treats the attack the same way a hacker would - they only have the information they can find on their own. This type of testing lets the security team react as if it were a real attack.
There are 5 stages to a penetration test, including:
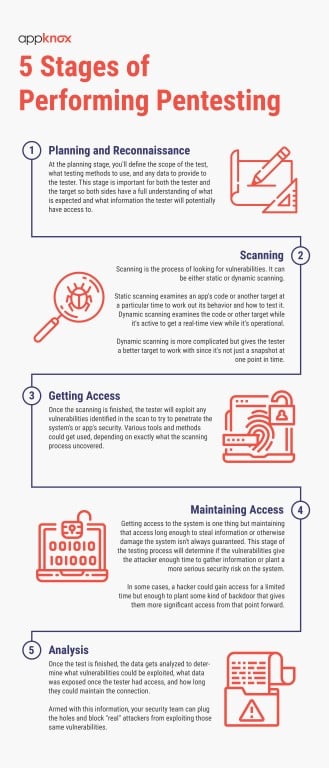
At the planning stage, you'll define the scope of the test, what testing methods to use, and any data to provide to the tester. This stage is important for both the tester and the target so both sides have a full understanding of what is expected and what information the tester will potentially have access to.
Scanning is the process of looking for vulnerabilities. It can be either static or dynamic scanning.
Static scanning examines an app's code or another target at a particular time to work out its behavior and how to test it. Dynamic scanning examines the code or other target while it's active to get a real-time view while it's operational.
Dynamic scanning is more complicated but gives the tester a better target to work with since it's not just a snapshot at one point in time.
Once the scanning is finished, the tester will exploit any vulnerabilities identified in the scan to try to penetrate the system's or app's security. Various tools and methods could get used, depending on exactly what the scanning process uncovered.
Getting access to the system is one thing but maintaining that access long enough to steal information or otherwise damage the system isn't always guaranteed. This stage of the testing process will determine if the vulnerabilities give the attacker enough time to gather information or plant a more serious security risk on the system.
In some cases, a hacker could gain access for a limited time but enough to plant some kind of backdoor that gives them more significant access from that point forward.
Once the test is finished, the data gets analyzed to determine what vulnerabilities could be exploited, what data was exposed once the tester had access, and how long they could maintain the connection.
Armed with this information, your security team can plug the holes and block "real" attackers from exploiting those same vulnerabilities.
Before starting the pentesting process, there is need of some rules of engagement that both the attackers and the target agree upon.
There are 3 types of penetration tests - black box, white box, and gray box. A black box attack is where the tester approaches the test from the same perspective as a hacker would. They start from scratch, don't have any information about the target, and have to identify all the necessary details themself.
In a white box attack, the tester gets all the information they need about the target so they have a starting point for planning their attack. A gray box attack falls between the two, with the attacker getting some information but not everything.
The scope of the test outlines what the tester is expected to test and, more importantly, what they should not try to access.
The tester should have contact information for the client, even for a black-box test. Penetration tests can sometimes lead to problems like a denial of service (DoS) issues that can knock the app or server offline.
If something beyond the scope of the test happens as a side-effect, the tester needs to be able to reach out to someone and let them know as quickly as possible.
If the test is being announced, the target's security team should know the date and time, the IP addresses of the tester, and any other relevant information. They need to be able to identify the tester versus an actual attack if one were to happen during the test.
If the test is unannounced, the tester should know what to do if the test is blocked successfully. Do they keep trying to get around the security measures or do they stop at that point?
If a pentest is successful, the testers could have access to sensitive data. Rules need to be set for how that data will be handled. This is particularly important if you're in an industry with regulated laws about how data is stored such as HIPAA rules for the healthcare industry.
The final piece of the rules of engagement is reporting the results of the penetration test. The tester should provide regular updates during the test but once it's finished, they need to report any vulnerabilities found, give a detailed timeline of the attack, and any other relevant information.
This gives the target's security team the details they need to go back and review the attack from their end and determine how their systems were exploited.
If you're interested in performing pentesting for your mobile apps, Appknox conducted a webinar on how to pentest on mobile apps using [FREE & OPEN SOURCE TOOLS]. Click on the link to view the key takeaways from the mobile security webinar.
We're a community of ethical hackers dedicated to the highest level of mobile app security. To see an example of how proactive security measures can help identify threats that may have gone unnoticed, request a copy of our gaming app case study. Or request a demo of Appknox to see how it can help secure your apps.
Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
