
BLOG

BLOG
SSL Pinning is a technique we use on the client side to avoid a man-in-the-middle attack by validating the server certificates. The developers embed (or pin) a list of trustful certificates in the client application during development and use them to compare against the server certificates during runtime.
If there is a mismatch between the server and the local copy of certificates, the connection will be disrupted, and no further user data will be sent to that server. This enforcement ensures that user devices communicate only with dedicated, trustful servers.
SSL Pinning prevents a man-in-the-middle attack, which means an attacker can not intercept the traffic and modify the data. If an attacker can not intercept the traffic, the application automatically prevents many server-side vulnerabilities. Because an attacker can not perform API-level test cases, implementing SSL is very important.
The basic approach for bypassing SSL pinning is to analyze the application's binary to determine the language in which it was written. Then, choose a language-specific way to bypass the SSL pinning of that iOS application. For example, we will use the Hotspot method if an application is built using Flutter or Xamrian.
Flutter & Xamarin application does not respect system proxy, which means that if you set a proxy on your iPhone and try to capture the traffic, the application will throw an error or be unable to capture the traffic. This is why the hotspot approach performs API-level penetration testing of these types of applications.
unzip test.ipa
cd Payloads/test.app/framework
Turn on mobile data = > turn on mobile Bluetooth => connect to the MacBook => turn on Bluetooth tethering from setting in mobile device
(Try to browse some data in MacBook to confirm that Bluetooth tethering is done properly)
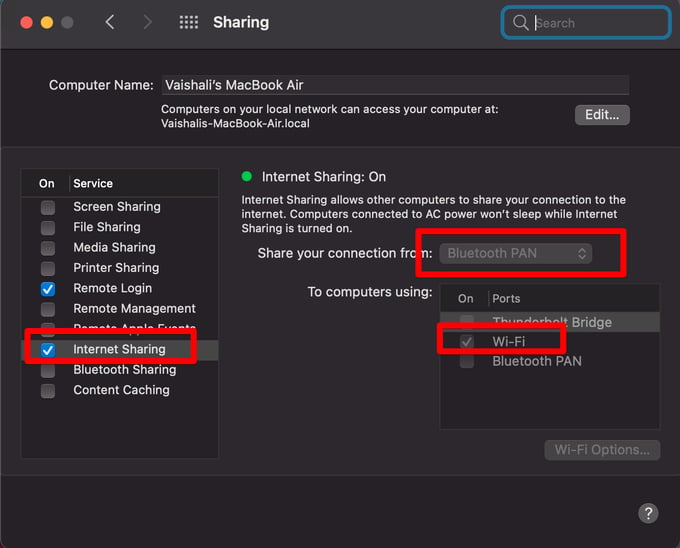
a) In MacBook navigate to System preferences => sharing => internet sharing => share your connection from => bluetooth PAN => To computer using => wifi
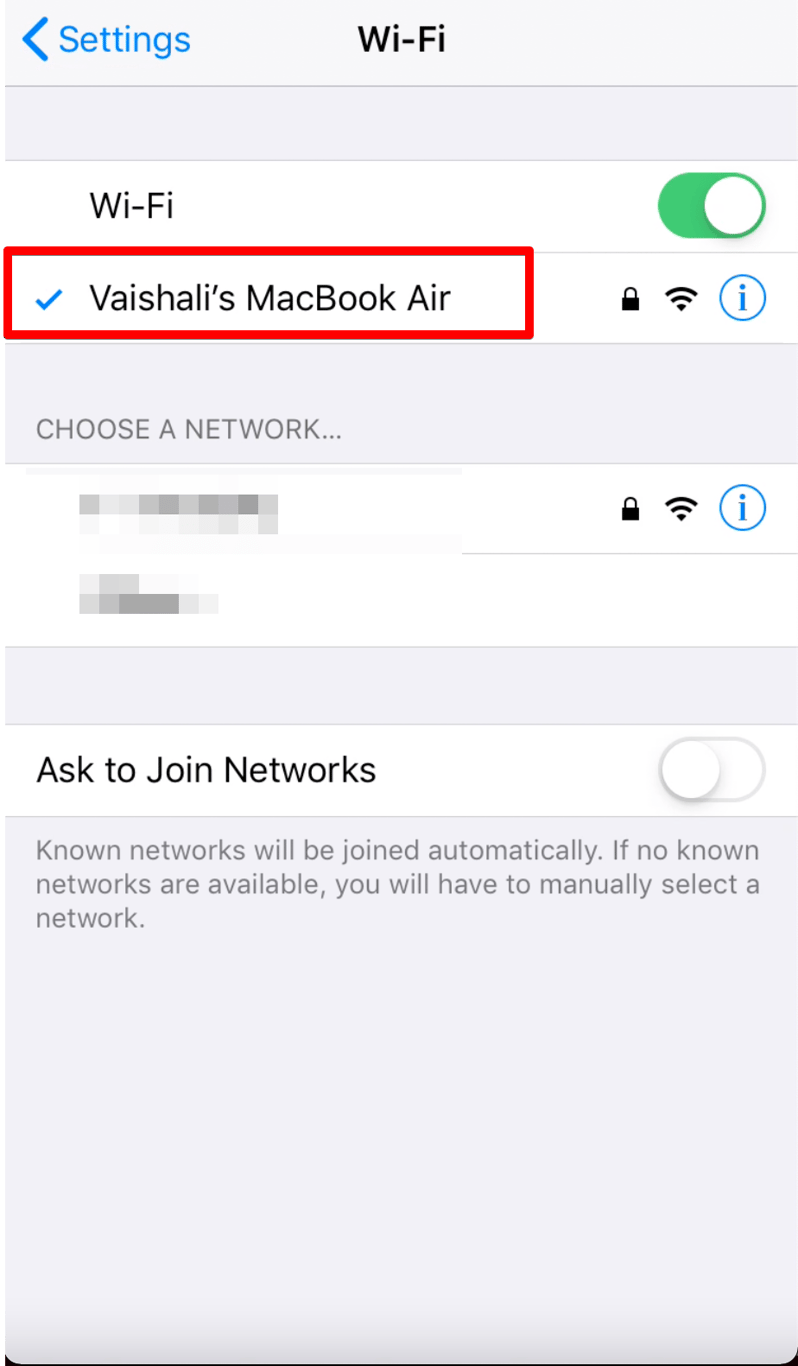
(Try to browse some data on your iPhone to confirm that this is done properly)
Create the Pf.rules file with the following data
rdr pass on bridge100 inet proto tcp from any to any -> 127.0.0.1 port 8080
Run the below two command
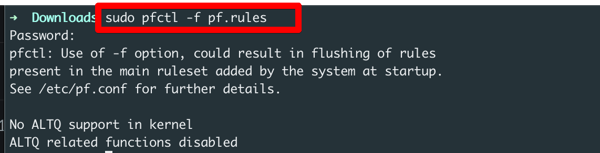
sudo pfctl -f pf.rules
sudo sysctl -w net.inet.ip.forwarding=1
![]()
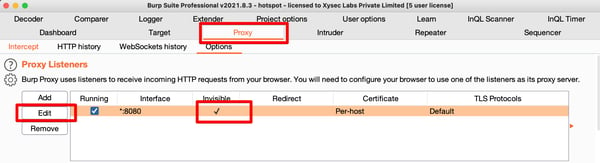
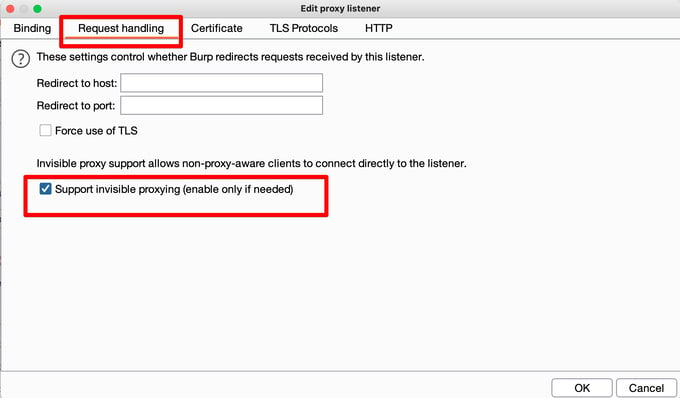
Open burp suite => proxy => Options => edit => Request handling => turn on support invisible peroxy
Some applications use a hardcoded certificate to implement SSL pinning in iOS applications. The application will check whether the certificate matches and only send the traffic to the server.
So, we'll replace the hardcoded certificate in the iOS application with our burp suite certificate and reinstall the app, and we'll be able to bypass the pinning.
Let's see how to replace the hardcoded certificate.
unzip test.IPA
cd /Payload/test.app![]()
find . | grep .cer
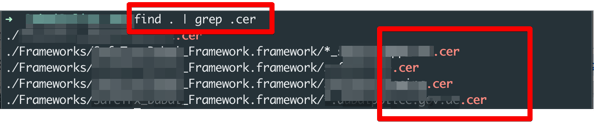
Note * certificates can be of different types also, like .pem, .cert, etc.
cp ~/Path_of_Your_burp_certificate ./Full_Path_Of_Hardcoded_Certificate![]()
Some applications use a hardcoded certificate hash to implement SSL pinning in the iOS application. Most applications built in Cordova use this technique to implement SSL pinning.
So, we can replace the hardcoded certificate hash value in the iOS application with our burp suite certificate hash and reinstall the application.
Let's see how to replace the hardcoded certificate's hash value.
unzip test.IPA
cd /Payload/test.app/www/pinning/pinning.json
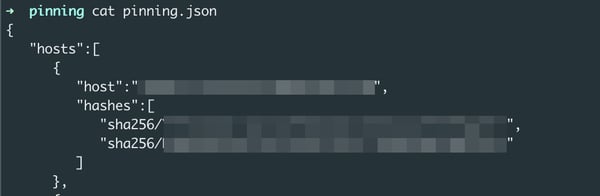
openssl x509 -inform DER -in cacert.cer -out cacert.crt
![]()
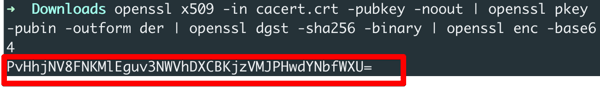
openssl x509 -in cacert.crt -pubkey -noout | openssl pkey -pubin -outform der | openssl dgst -sha256 -binary | openssl enc -base64
scp /Path_Of_Downloaded_deb_file root@your_iphon_ip:/private (Folder where you want to copy the package)
ssh root@iphone_ip
dpkg -i ssl.deb
Some application traffic can not be captured directly via the burp suite. In such cases, MITM comes into the picture. Instead of capturing the traffic via the burp suite, we can use MITM to capture traffic and then send it to the burp suite using MITM.
You can also use MITM with the objection, Frida script, etc. It works many times, in one of my projects I tried a lot to bypass SSL pinning but nothing worked. Then, in the end, with one Frida script and MITM, I captured the traffic.
ii) Download the MITM certificate in the iPhone
a) Connect the iPhone and Macbook via USB and Enter the below command
mitmproxy
b) Enter the below command in the iPhone browser
Mitm.it (Download the iOS certificate)
iii) Install the MITM certificate on the iPhone
In iPhone navigate to Setting => Install Profile => Setting => Trust certificates => Certificate Trust Settings => Enable mitmproxy
iv) Enter the below command to start the mitmproxy in the Browser.
mitmweb (mitm get open in the browser automatically)
v) Setup MITMProxy for forwarding traffic from the MITM to the burp suite.
a) Enter the below command
mitmweb
b) Go to the option. Click on "Edit Options" and on "set this configuration"
c) Search for mode and add the following line there
upstream: http://127.0.0.1:8888
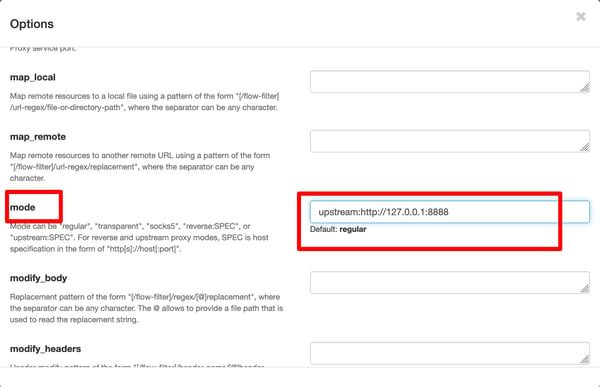
d) Search for ssl_insecure and enable it
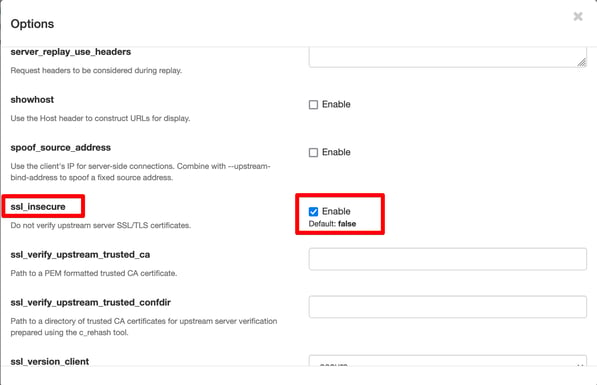
e) Set upstream proxy in burp suite.
Set the IP address and port no in the burp suite that you have set for the upstream in mode option.
f) Start browsing the application from the iPhone and observe that the traffic will be captured in the burp suite.
a) Install Frida Server:
From iPhone open Cydia => Source => Edit => Add => https://build.frida.re => search =>frida =>Install
By default the Frida server is running up on the iPhone, you don't need to start a Frida server every time.
b) Install objection in MacBook
sudo pip3 install objection
Note* While using objection make sure the application is opened in the device, otherwise objection wouldn't work.
c) Enter the below command to connect the application to the objection and explore the application.
objection --gadget package_name explore
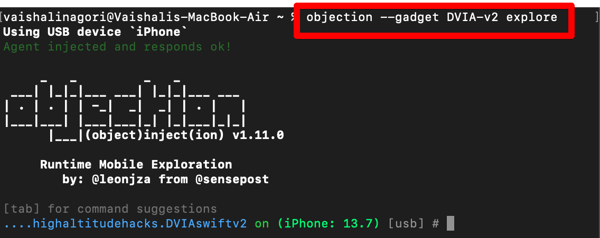
d) Run the below command to bypass SSL pinning
ios sslpinning disable
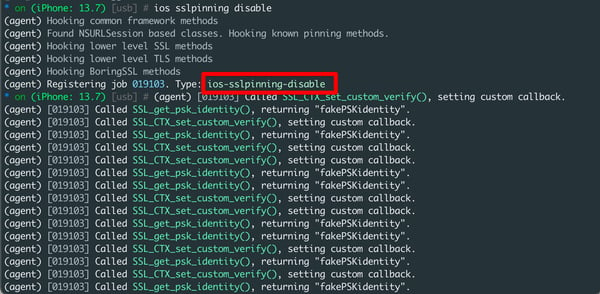
e) Start browsing the application from the iPhone and observe that the traffic will be captured in the burp suite.
i) Enter the below command to bypass SSL pinning
frida -U -f package_name -l ssl.js --no-pause
U => To use a connected USB device as a target
F => To indicates the package name
L => To load the script
ssl.js =>
(Download the script from Codeshare according to your iOS version)
--no-pause => To force Frida to "not to pause" app execution after injecting the script.
ii) Start browsing the application from the iPhone and observe that the traffic will be captured in the burp suite.
Some applications define the pinning rules in the Info.Plist file and set the boolean value. We can modify these boolean values from true to false and bypass the SSL pinning.
i) Go to the binary of the IPA file and open Info.plist file.
ii) Data is present and key-value pair and now search for the keywords like <key>TSKEnforcePinning</key>,<key>NSRequiresCertificateTransparency</key> etc.
iii) Change the value of these from true to false and reinstall the application.
iv) Start browsing the application from the iPhone and observe that the traffic will be captured in the burp suite.
The amount of private and sensitive information handled by mobile apps these days makes them a lucrative target of threat actors. In the case of iOS applications, attackers would generally begin by bypassing the SSL/TLS protection layer and gaining more information about the apps' functionality and structure. That is why in-depth penetration testing becomes a must, and knowing the several techniques used by attackers to bypass SSL pinning can be a very proactive start in this direction.
Based on the insights gained, you can always add additional security measures to your app and stay ahead of attackers.
Yes, bypassing SSL pinning in mobile apps can expose apps to considerable risks. Some of them are:
Yes, SSL pinning can be bypassed on non-rooted devices, but it's tricky. Attackers often use dynamic instrumentation tools (e.g., Frida or Xposed) to manipulate the app's behavior at runtime and bypass. These tools can intercept SSL certificates and bypass pinning checks without modifying the device.
Frida is one of the most popular tools. It allows attackers to inject scripts and bypass SSL pinning checks without modifying the app’s code. Another widely used tool is Objection, which is built on Frida. It makes it easier to automate SSL pinning bypass with minimal effort.
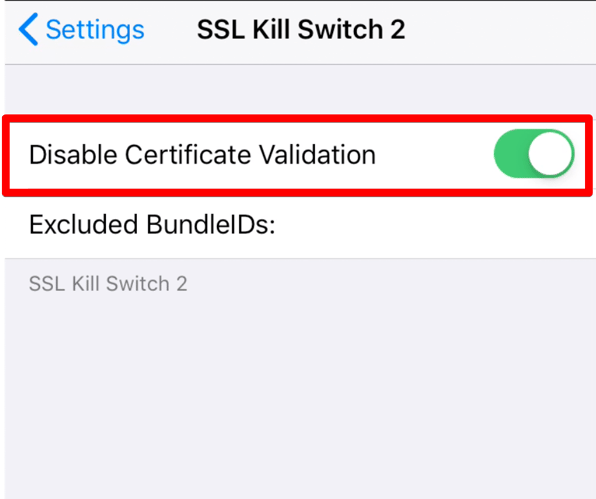
SSL Kill Switch is a framework designed to disable SSL pinning in iOS apps by patching security functions.
Follow the below best practices to enhance mobile app security against SSL pinning bypass attacks.
First, implement strong obfuscation techniques to make it harder for attackers to reverse-engineer the app’s code. Use certificate transparency and public key pinning instead of hardcoding certificates, ensuring real-time validation. Regularly rotate certificates and keys to reduce the risk of misuse.
Then, integrate runtime security tools that detect debugging or tampering attempts. Finally, security audits and penetration testing should be conducted to identify and address vulnerabilities before attackers can exploit them.
