
BLOG

BLOG
Positioning security dynamics within an organization presents its own set of challenges. Security and mainly digital data and privacy, have become the central theme of digital transformation plans.
According to BeyondTrust, Internet of Things (IoT) devices will be the primary target for hackers in the upcoming years, even more so than they are at the moment.
Even our emails are not as secure as the most common method for cybercrime is spreading malware via spam emails and phishing emails. And so, here we are, talking about the best organizational dynamics for information security.
Organizational Dynamics is the process to strengthening of the organization's resources and enhancing employee performance. It can also be taken as a measure to describe how an organization promotes organizational learning, strategic and team management, and even better business practices.
Here, when associated with Information Security, the whole concept of Organizational Dynamics for Information Security refers to strengthening the organization's capacity. This strengthening will eventually result in prevention against the severest of cyber crimes. The process is done by the implementation of some of the Information Security Organization Designs.
Information Security Organization Designs are structures made to establish the implementations required to strengthen the information security of an organization. There are many design layouts for Organizational dynamics for Information Security.
The background against which such Information Security Organization Designs must be designed and managed and being a protective measure from the advancing threat technology. It mainly depends upon the global digital business transformation. This dependence refers to the fact that any increment in the rate of change and the complexity of digital technology will eventually lead to amending the whole design. Resulting in the emergence of new roles such as security champions, vanguard security architects, and even digital risk officers to form a security team.
The continuity and the upcoming new security challenges at every step have forced security leaders to explore and implement new ways of protecting digital information. Standard staff augmentation solutions such as Managed security services and contracting have been implemented, but the requirement was for more advanced and elaborate methods of protection.
When designing an Information Security Organization Design, there are many factors to be taken into consideration.
Analyze the required security capabilities and broadly define the skills, making high-level process flows and even RACI charts.
For a quick introduction, RACI, an acronym for four activities namely Responsible, Accountable, Consulted, and Informed, is used to clarify and define roles and responsibilities in cross-functional projects and processes. Use both these process data and charts to design the optimum location structure.
Be sure to design a tactic having a sufficient level of separation between the oversite (policy management and assurance) and operations (security tool administration). This separation becomes one of the significant drivers for moving the reporting line of the CISO out of the Information Technology Organization.
Never go for an all-out operation. Design your tactics properly, select the proper measures required, and then, make the best suitable design.
It is not necessary to resolve the perfect design in your first attempt. There will be many failures and many errors in the process. The best approach will be to craft a new plan and implement it in a realistic environment.
The most common mistakes done while developing a security design. Every organization has different systems and different requirements, so, a security design that works best for one organization will not necessarily work for others in the same way. And so, it will be best to design a new security design from scratch.
Many factors impact a security design for an organization.
There are three types of Information Security Models, based upon the nature of the organization.
In this type of security model, the two variations are the one in which the CISO reports to the CIO (grey reporting line) and the other one in which CISO reports outside of CIO organization (such as the chief risk officer) (orange reporting line).
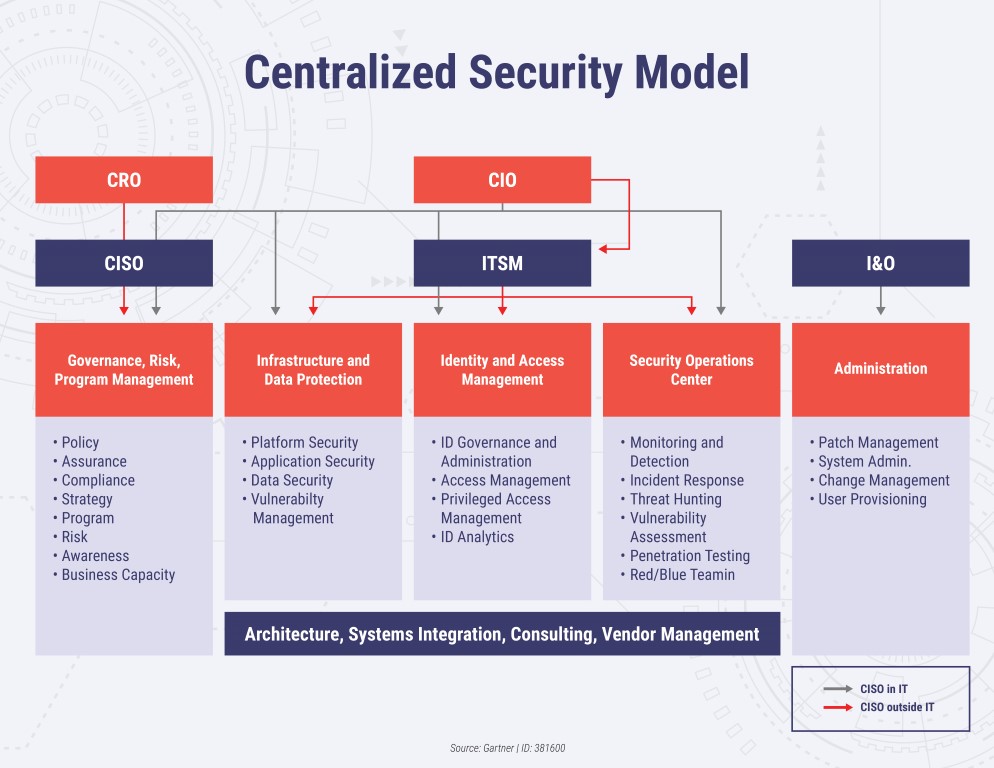
It is a decentralized architecture. The separation of policy management and operations resulted in separate teams for security governance, security strategies, management, services, and even local security.
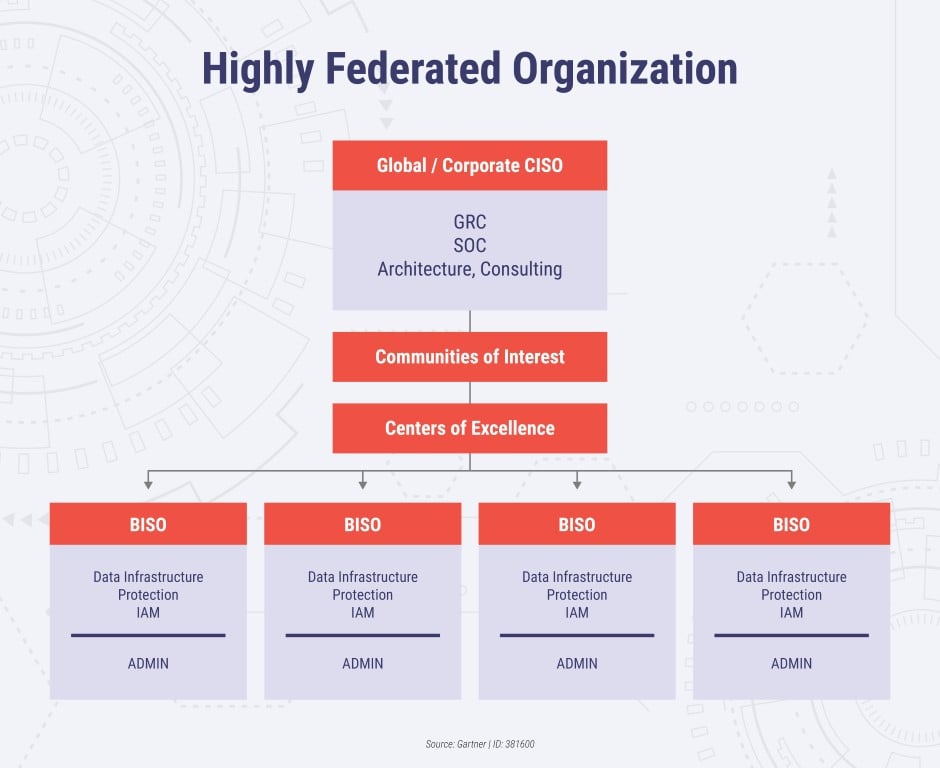
The communities of interest and centers of Excellence act as channels for information transfer between various decentralized teams and hence enables communication on a specific security topic (if required).
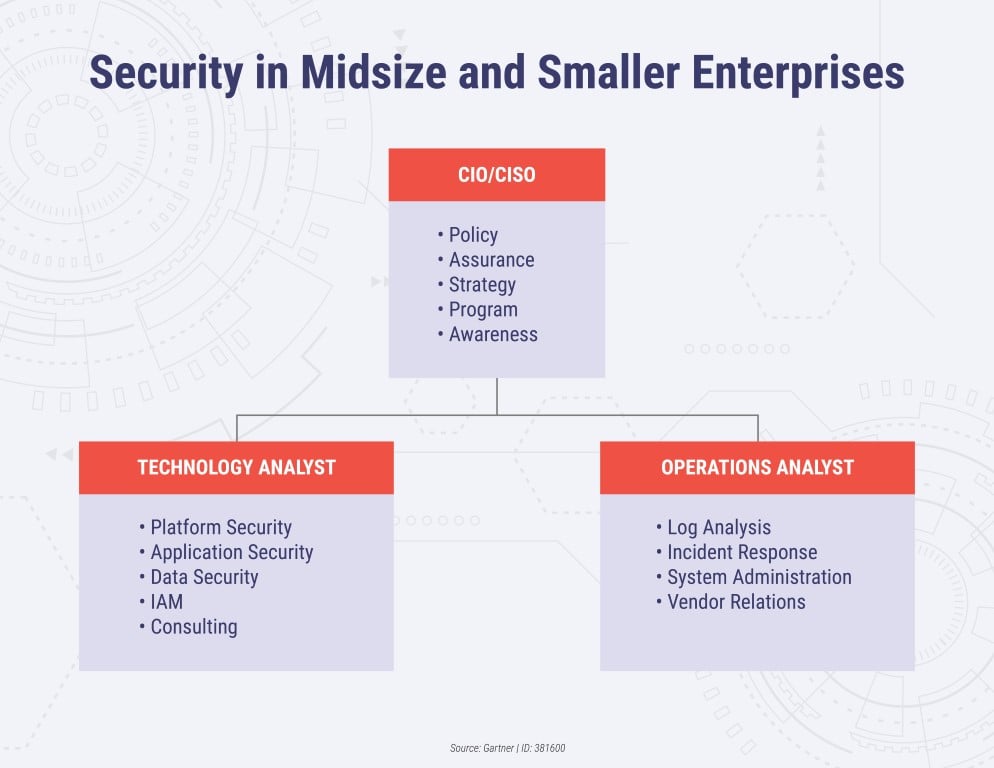
Mostly used in a small organization of a strength of about 500 to 300 users. Thus, it only requires two or three groups to maintain the whole system. Here, the CIO is responsible for policy management. Organizations with less than 50 employees usually depend solely upon the CIO, which also fulfills the role of CISO, acting as vCISO (Virtual CISO).
As Gartner mentions - There is no such thing as a perfect, universally appropriate model for security organizations. And rightly so! Risk management and security leaders in every organization must develop their own model, taking into consideration the basic principles, practical realities, and the challenges of digital transformation.
.jpg?width=50&height=50&name=10606600_10204086667262761_7381430219125488912_n%20(1).jpg)