BLOG

BLOG
As a mobile app developer, you must develop and release fully functional and safe applications. While you can manage the functionality comfortably, making the application secure and resilient to cyber-attacks is hard. So, what should you do? Well, we've got you covered.
Whether you're developing a mobile or tablet app, security must be a top priority to protect your users and their data. By understanding these common issues and their solutions, you can ensure that your app is secure on all devices. So, let's get started.

Copying and pasting code is a common practice among developers (beginners). While doing this may save the day, it can also make your code vulnerable. Who knows, maybe a hacker wrote the code intentionally, right?
Solution: Never copy code blindly without understanding each character. Also, avoid downloading frameworks or libraries that verified users don't create.
Not validating the data entered by the users can make your application an easy target for hackers. Without proper validations, hackers can enter malicious commands or harmful codes that negatively impact your app.
Solution: Validate every input field in the best way possible. Here are some things you can consider:
- Data Format
- Data Length
- Permissible Characters
- Minimum and Maximum Value, etc.
This way, the app will accept your desired data, thus improving security.
How you deal with data significantly impacts how secure your app is.
For instance, if you're storing and sending data without encryption, it's a significant security issue. Anyone can access this data and use it for unfair purposes.
Solution: Encrypt all the data that you store and transmit. This way, even if the hackers download the data, they won't be able to use it, and you can ensure security in mobile app development.
Pro tip: Never store encryption keys on the app, and use encryption protocols such as AES and SHA256 for better protection.
If your users can set any password they want in the application, they're at risk. This is because hackers try different combinations of characters to brute-force user passwords and gain access. This method works best with common and easy passwords.
Solution: Always include these points in your secure mobile app development checklist:
- Set a strong validation condition for setting a password.
- Lock the user out after a set number of wrong attempts.
- Enable 2FA for the application.
Most developers secure the application's client side without paying enough attention to the server-side security. This can compromise confidential data such as credit card information, especially if stored on the server.
Solution: Include high-grade encryption and a reliable SSL in your list of mobile app development security best practices. This way, you can significantly enhance server-side security.
Rookie developers sometimes hardcode information such as username or password in their code. While it may sound like an easy workaround, coding malpractice risks user information.
Solution: Always use high-quality coding practices and never hardcode information. Still, if you have to store some info on the app, ensure it's encrypted.
While caching helps users save time, it also puts them at risk. How? Let's say your app saves users' login info to allow them to log in instantly without entering anything. Now, if the mobile device is stolen, anyone can log in to the app and use it for unfair means.
Solution: Always use high-quality coding practices and never hardcode information. Still, if you have to store some info on the app, ensure it's encrypted.
Mobile apps usually have longer sessions than web apps. This ensures a smooth user experience and sales, especially in eCommerce.
However, if the phone gets stolen and the session doesn't expire, the thief can access the information easily, compromising app security.
Solution: Integrate reauthentication techniques. This will prompt the user to log in again to confirm identity before making the final transaction.
Pen-testing helps you determine real-time security flaws or vulnerabilities in your application. According to research by Informa Tech, 69% of the companies involved (3,000) perform penetration testing to prevent data breaches.
Unfortunately, developers sometimes skip this step and release the application due to short deadlines or mere carelessness. And this puts the users at risk.
Solution: No matter how close the deadline is, perform multiple pen tests on your application. This will help you find any security flaws that you can fix and ensure safe website and mobile app development.
As per the standard procedure, patches and updates should be pushed frequently based on user feedback. Unfortunately, this rarely happens, risking user security and the company's reputation.
Solution: When your app goes live, look for genuine customer feedback. Adhere to the input, perform patches, release the improved version, and repeat. This way, hackers won't be able to benefit from the loophole you might have left in the previous version.
Mobile app security is a measure developers take to protect a mobile application from vulnerabilities and external threats.
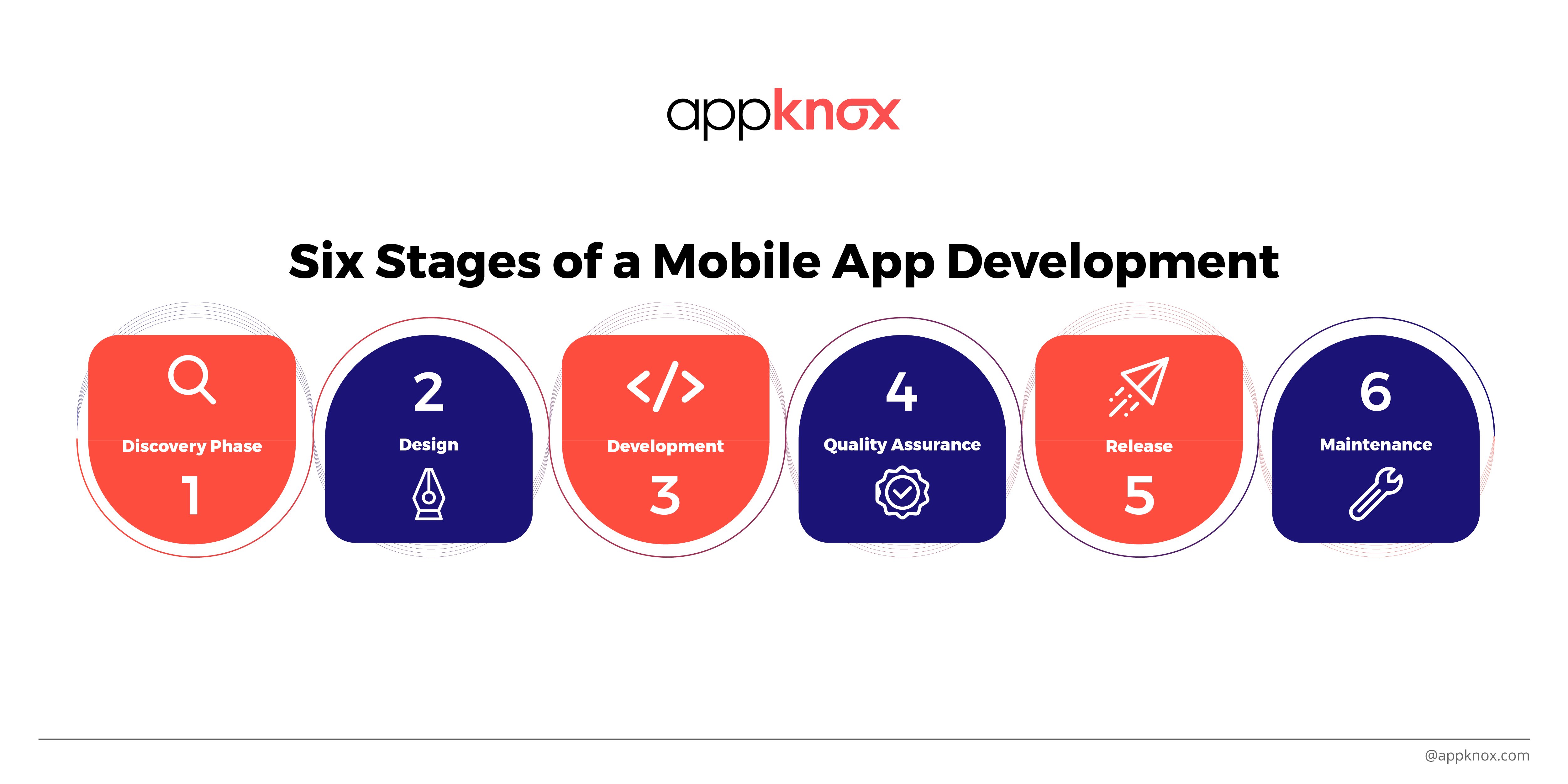
The mobile app development cycle is a set of processes that describe how a software/app is created. Here are the six stages of a mobile app development lifecycle:
To know more, visit this link.
HIPAA is an act that was enacted in 1996 to protect sensitive health and personal information. And HIPPA-compliant mobile app development is developing applications that follow its principles.
All healthcare providers, plan providers, clearinghouses, and business associates must use HIPAA-compliant applications. It's because they deal with the personal information of the patients.
While you can follow the solutions given above for securing your application, there's something more practical that you can use. What's that? Appknox.
Appknox is the world's most potent plug-and-play security platform for businesses and developers, and it helps protect mobile apps in minutes. Using Appknox, you can:
Also, Appknox focuses on mobile application security on platforms like Android, iOS, etc. It means you can test applications for multiple platforms using Appknox.
Book a demo with us today and secure your mobile application with Appknox.
