
BLOG

BLOG
Securing a mobile application can be highly challenging and if a breach is made, it can be disastrous. There are many reports, especially by Gartner, that showcase how vulnerable a mobile application is.
Gartner released a new report which says that more than 75 percent of mobile applications will fail basic security tests. Gartner said that in 2015, the majority of mobile applications - whether in the Android, iOS or Windows Phone ecosystems - will not have basic business-acceptable security protocols in place. Part of the issue with mobile application security is that employees download apps that access enterprise assets or perform business functions, but the security of the apps is not adequate to protect against attacks or meet the security requirements set out by company policy.
A report by Ovum Research predicts that a growing number of cloud-based business and security services will rely upon mobile devices, making them targets for hackers.
While there are numerous reasons behind mobile applications failing to achieve even the basic level of security, the research shows that 75 percent of mobile security breaches through 2017 will be caused by mobile application misconfigurations, “rather than the outcome of deeply technical attacks on mobile devices.”
Diving deeper into this problem one can realize that the challenge is not really the technicality involved, which is just part of the problem. The bigger challenge is the attitude shift needed so that brands and businesses can realize that security is not something to be taken lightly. Most organizations follow a reactive attitude towards security issues. The real challenge is to change this attitude to a more proactive one.
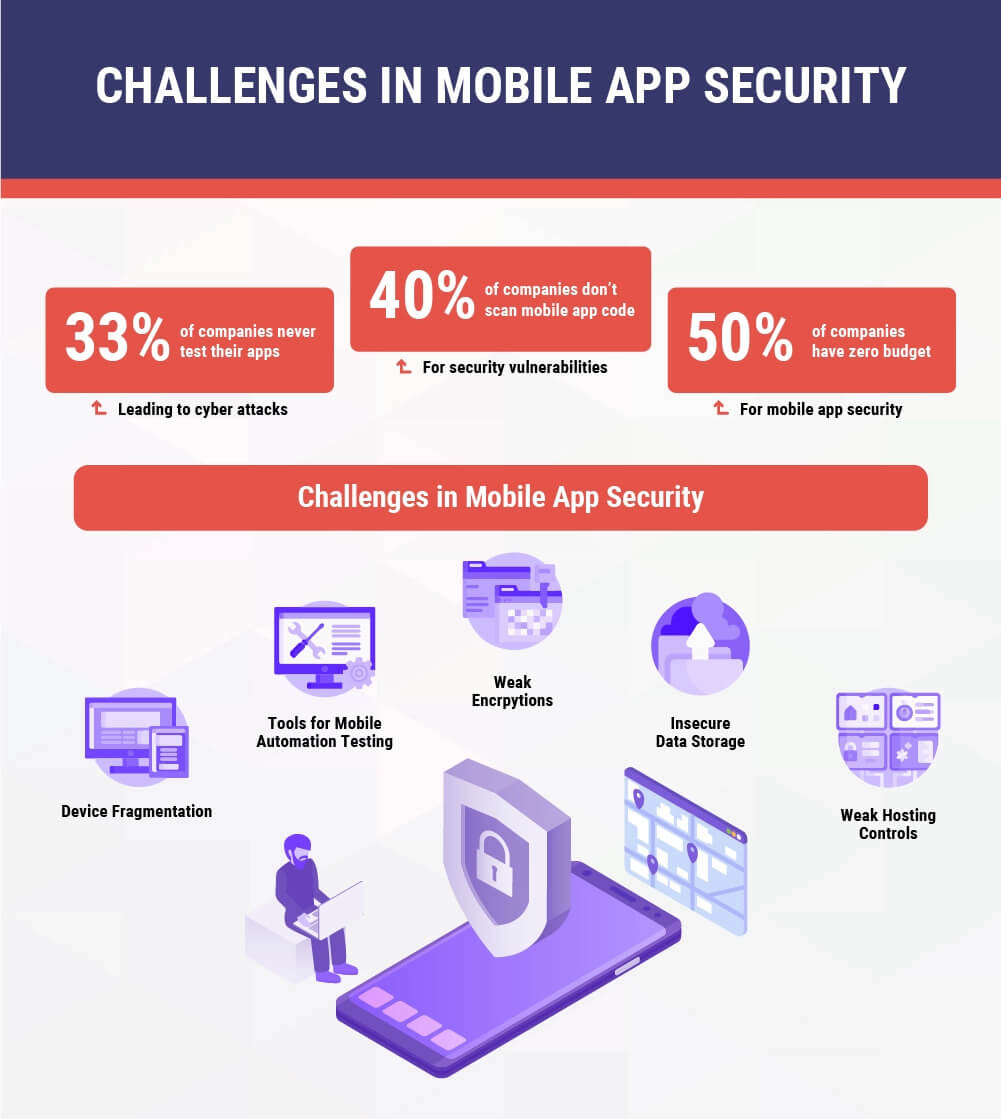
It is extremely important for businesses and organizations to make sure that mobile strategy is deployed effectively so that the developers are able to think through the solutions of unintended attacks on applications’ security. Since putting the data security of an enterprise at risk can result in the reduction of brand value, it is essential to understand the challenges associated with mobile application security. Here are a few of them:
Mobile application testing basically involves a number of mobile devices that revolve around with several capabilities, features, and limitations. Performance testing can become quite a difficult task because of the identification of vulnerabilities in security specific to the devices. The testing team is prone to become a bottleneck in the release process if its test releases are not as fast as that produced by the development team.
This may further lead to the creation of low-quality applications. We are already aware of the fact that a large number of apps are produced in iOS, Android, or Windows environments. Moreover, there is always a different set of vulnerabilities for a different version of each operating system (OS). Individual testing of each version of the app is time-consuming and demands the application tester to be informed about the pre-existing loopholes.
Data can readily be accepted from all kinds of sources by a mobile application. On the flip side, an absence of sufficient encryption can motivate attackers to modify inputs that include cookies and other environment variables. Furthermore, if the decisions on authentication and authorization are made on the values given by these inputs, then the security of the apps may become prone to cyber-attacks.
In an incident that occurred recently, Starbucks users were targeted by hackers to siphon a worrisome amount of money from their respective Starbucks mobile apps. In a shocking revelation later, Starbucks accepted the fact that usernames, email addresses, and passwords were being stored by the app in cleartext. This resulted in the hacking of the usernames and passwords by anyone who connected the target phone to a computer system.
Fragmentation requires considerable knowledge about the use of automation testing. Since cross-platform minds were not used for designing traditional testing tools like QuickTest Professional (QTP) or Selenium, hence different automation tools are used for mobile apps and web applications altogether. Even after the emergence of a number of test automation and testing tools for Android and iOS, the availability of full-fledged standard tools for security testing is still scarce. Taking a closer look at the ecosystem of automation testing, you will find that Appium, Robotium, and Ranorex are the common tools in this field available to this day.
It is a tendency of the businesses to expose server-side systems to outside networks, which were initially inaccessible while building their first mobile applications. The major take here is the fact that there ought to be some security measures on the host servers in order to prevent unauthorized users from getting access to your data.
This basically involves your own data along with the data from third-party systems that your app might be accessing. It is extremely important for the back-end servers to be completely secure against any kind of malicious attacks. Verification of APIs is necessary and deployment of proper security methods is important in order to make sure that access is provided to authorized personnel only.
Going by the system of popular apps, it has been found that the customers basically just enter their passwords while activating the payment portion of the app and use it again and again in order to make an unlimited purchase. This activity provides the ease of using their already stored password and user name without re-entering them in the database.
In all such cases, it is important to make sure that the encryption of usernames, email addresses, and passwords is subsequently done. For instance, a mechanical flaw in the data security system of Skype resulted in a vicious attack by the hackers that further led them to open the Skype app and dial arbitrary mobile phone numbers that used a simple link within the contents of a given email.
Under such circumstances, it becomes important for developers to design apps in a secure manner in order to make sure that critical information such as credit card numbers, contact information, password, etc. is not stored directly on the device. And if they do, every aspect of security is maintained.
Appknox actually helps make lives easier for brands. Appknox helps developers and businesses make their mobile applications more secure by detecting vulnerabilities in their apps and suggesting ways in which they can fix them. The best part is that we do not need access to the code which is prized possession for any company. In short, we help provide peace of mind to major brands and businesses as far as their mobile security is concerned.
.jpg?width=50&height=50&name=10606600_10204086667262761_7381430219125488912_n%20(1).jpg)
Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
