
BLOG

BLOG
The Open Web Application Security Project (OWASP) has officially released the latest OWASP Top 10 2017 list of top ten most critical web application security risks. This is the first update since 2013. The Open Web Application Security Project (OWASP) is a 501c3 not-for-profit worldwide charitable organization focused on improving the security of application software and consists of numerous security experts from around the world.
OWASP is known to update this list every three to four years. The OWASP Top 10 list is considered a benchmark in the application security community. The list not only contains the latest vulnerabilities, threats and attacks but also tactics on how to detect and resolve them. The OWASP Top 10 list is created by analyzing the occurrence rates and severity levels of each threat.
We've extensively covered about each of the OWASP Top 10 threats in the 2013 edition, and we'll continue to do that for the new OWASP Top 10 2017 edition as well. Here's what is new this year:
The 2017 list contains the following as the Top 10 threats:
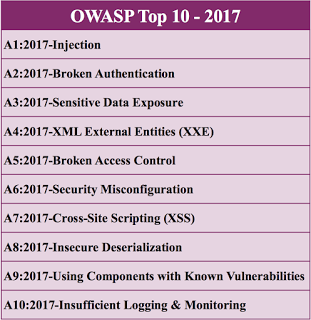
There are some new issues here which are primarily modern era issues. It's important for developers, businesses and security companies like us to make headway for them.
Some of these issues need more explanation:
| Label | Issue Name | What's New |
| A3:2017 | Sensitive Data Exposure | Sensitive Data Exposure is now firmly about privacy and Personally Identifiable Information (PII) breaches and not stack traces or headers |
| A4:2017 | XML External Entities (XEE) | This is a new data supported item. Developers and testing tools need to learn how to find and test for XXE. DevOps need to understand how to fix it. |
| A6:2017 | Security Misconfiguration | Now encompasses cloud security issues as well, like open buckets. |
| A8:2017 | Insecure Deserialization | This is a critical issue that was asked for by the community. Need to understand what Java and PHP (and other serialization) looks like so it can be fixed. |
| A10:2017 | Insufficient Logging and Monitoring | Again this was selected by the community. The common belief is that this is missing control rather than a weakness. The fact that organizations still take more than half a year to detect a breach, this is needed to get it fixed. |
The new and revised list is based on over 40 data submissions from firms that specialize in application security and an industry survey that was completed by over 500 individuals. Here's how the change appears compared to the Top 10 list from 2013:
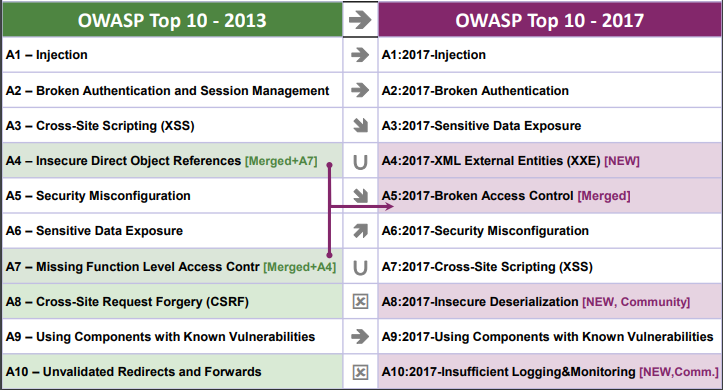
Let's dive a little deeper into what are the new threats that made it to the OWASP Top 10 2017 list:
XML External Entities - According to OWASP, an XML External Entity attack is a type of attack against an application that parses XML input. This attack occurs when a weakly configured XML parser processes an XML input that contains a reference to an external entity. This is a critical issue and can lead to loss of confidential information, denial of service, server-side request forgery, and other system-level impacts.
Insecure Deserialization - According to OWASP, “Serialization is the process of turning some object into a data format that can be restored later. People often serialize objects in order to save them to storage or to send as part of communications. Deserialization is the reverse of that process – taking data structured from some format, and rebuilding it into an object.” Based on the definition above, an insecure deserialization can lead to remote code execution. Even if remote code execution doesn't happen, this can lead to other flaws like replay attacks, injections attacks, etc.
Insufficient Logging and Monitoring - According to OWASP, insufficient logging and monitoring can allow attackers to deepen their attack on systems, be more persistent, pivot to more system, extract and destroy data.
To defend against the Top 10, OWASP believes that action needs to be taken at all levels: developers need to establish and use repeatable processes and security controls, security testers need to establish continuous application security testing, application managers need to take charge of the full application lifecycle from an IT perspective, and the organization as a whole needs to have an application security program in place.
“A great deal of feedback was received during the creation of the OWASP Top 10 – 2017, more than for any other equivalent OWASP effort. This shows how much passion the community has for the OWASP Top 10, and thus how critical it is for OWASP to get the Top 10 right for the majority of use cases,” the OWASP team wrote.
Source: OWASP
.jpg?width=50&height=50&name=10606600_10204086667262761_7381430219125488912_n%20(1).jpg)
Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
