
BLOG

BLOG
Security vulnerabilities could harm businesses of any size and type. According to a report published by PT Security, around 43% of the Android and 38% of the scanned iOS apps had high-risk vulnerabilities in them.
In order to successfully fight against this rising threat, businesses must take security ahead on their priority ladder. That is why the adoption of advanced security assessment techniques like VAPT [Vulnerability assessment and penetration testing] becomes necessary.
Moreover, as much as the testing process, its proper reporting has an important role to play as well. Vulnerability reports not only provide a detailed structure of the assessment but also offer meaningful insights to target the risks.
But often at times, security service providers overlook the importance of proper reporting. As a result, clients end up being dissatisfied with the entire testing process. Therefore, it becomes necessary to examine the importance of vulnerability reports.
The basic step in this direction should be knowing how to differentiate a good mobile security assessment report from others. And for this, you must know what to look for in an online mobile application security assessment report.
Before moving ahead, let’s first see why Appknox’s approach to vulnerability testing is the best in the market. Later on, we will take you through a sample Appknox mobile security assessment report so you could have a fair idea of what to look for in a standard mobile security assessment report.
Often counted among the highest-rated security testing vendors, Appknox is well known for providing top-notch mobile security services.
Our VAPT Suite ensure that security is never a concern for your business. With detailed expertise in business verticals like FMCG, Media, BFSI, Fintech and government institutions, we have provided cybersecurity solutions to more than 200 companies worldwide.
Our services ensure that your product and business stay on top with a faster time to market. We believe in automation of security, thus giving teams enough time to do more thorough manual pen testing and pinpoint remaining issues if any. By plugging more than 500,000 threats to date, we have saved millions of dollars for businesses across the globe.
Similar to other business highlights, our mobile security assessment reports stand out in comparison to others as well. We focus on accuracy and reliability and our reports enable our users to achieve similar results as well.
Our aim is to provide clear and simplified results in our reports. By doing this, we not only show the right path to our clients but also save their useful resources.
Here we have outlined a list of some of the key features we include in our mobile security assessment reports and why they are so important.
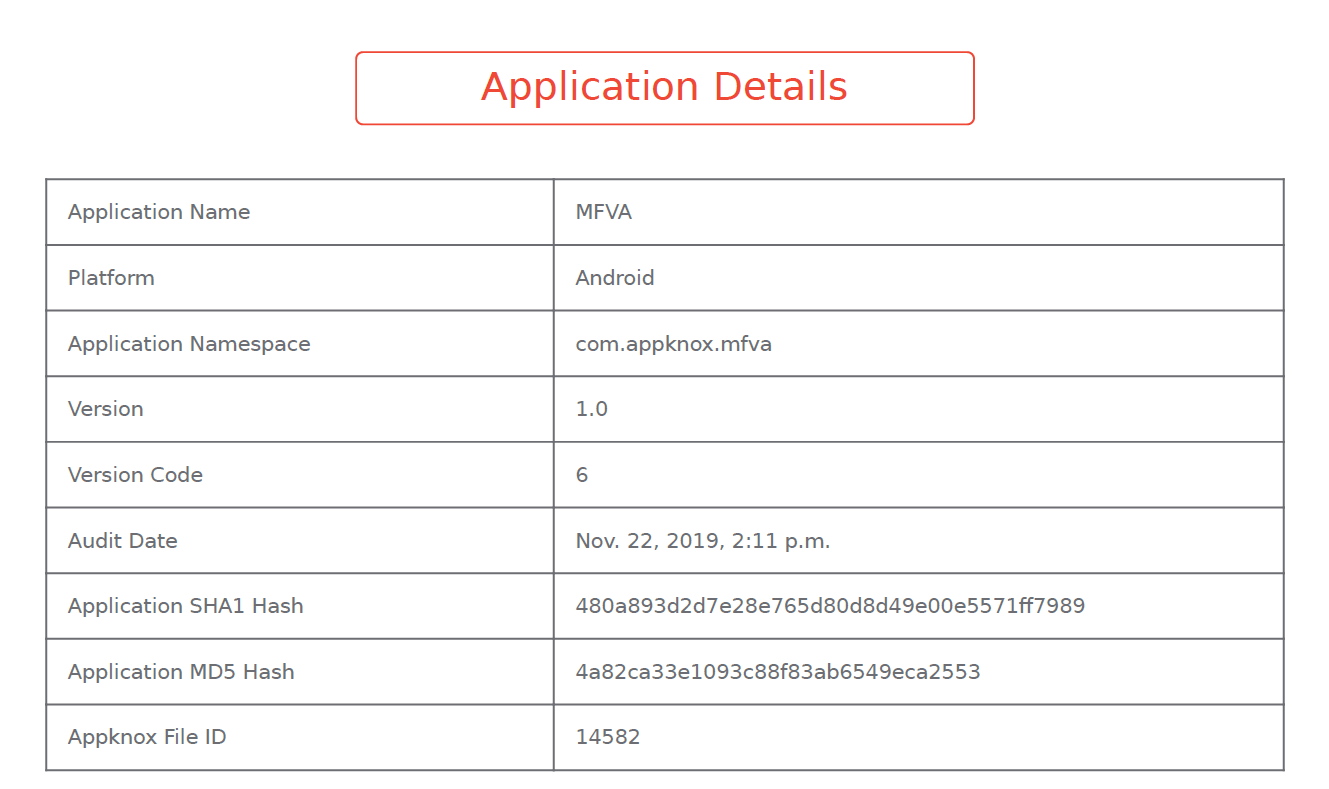
In order to ensure easy tracking and for future reference, our vulnerability report always comes with application details. So, every time an app gets tested, a concise summary containing the app’s name, platform, version, and unique id is recorded. The basic idea behind this part of the report is that it helps users in keeping track of individual tests.
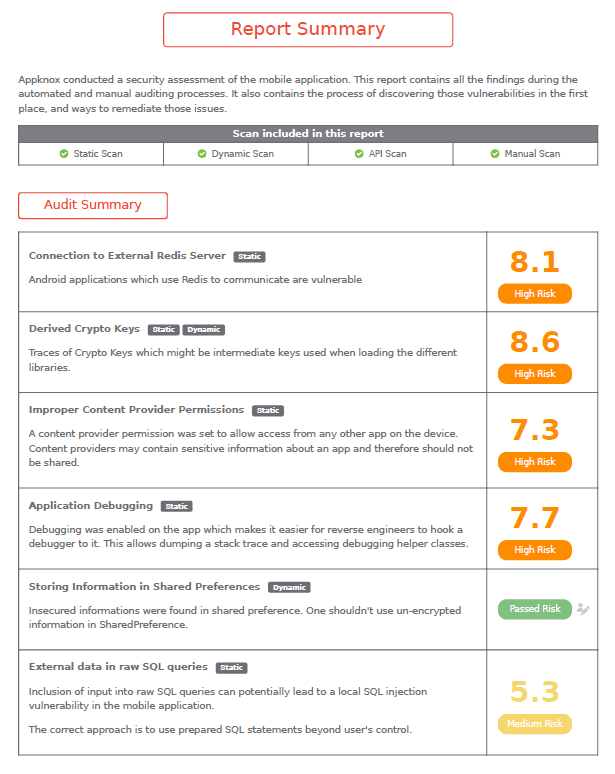
Once the detailed static, dynamic, API security testing, and other manual scans are completed, an executive report summary is presented. Here, users can see a detailed overview of the tests and the corresponding CVSS (Common Vulnerability Scoring System) scores. This universally accepted and standardized method rates vulnerabilities on the basis of damage they can cause or the urgency of response.
The purpose of this summary is to present a simple overview of the risks found during the test. Without going into the technical details, business leaders can gain some important insights from this audit summary.
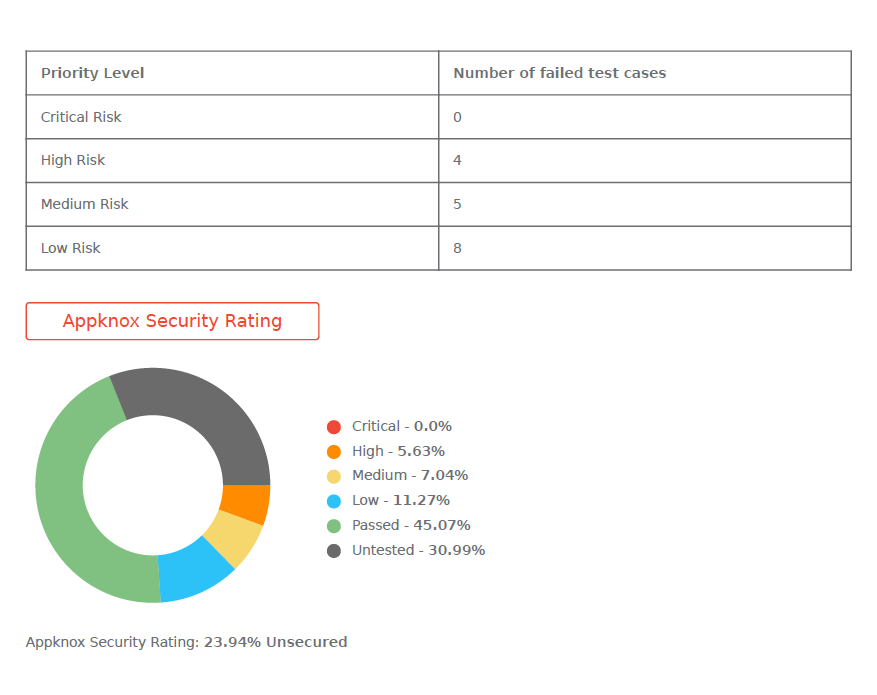
Visual elements like graphs with security ratings make communication even crisper. Based on priority levels, the failed test cases are outlined. The summary also mentions whether the security issue was found during static analysis, dynamic analysis, API testing, or manual testing.
After rating the risk, it becomes important to explain the risk and also its implications. So, after the audit summary, Appknox’s vulnerability assessment report provides a detailed overview of each security issue.
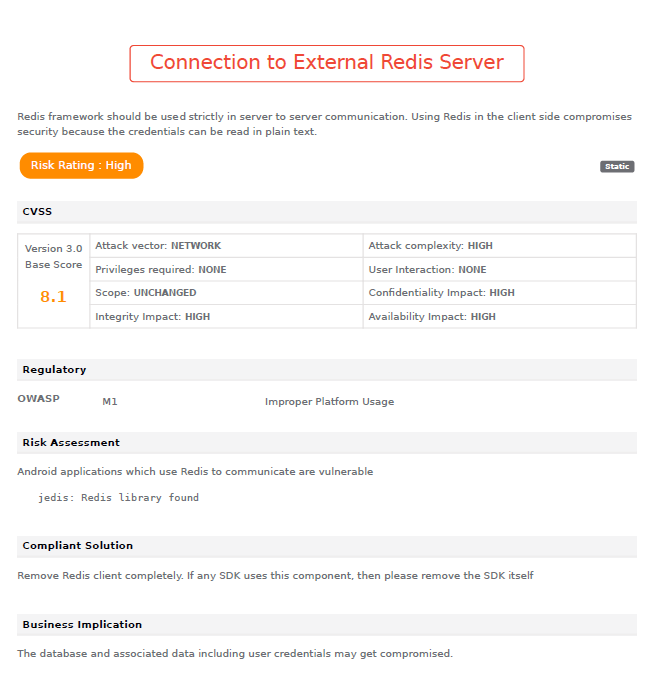
In the detailed report the major components are:
This section of the report not only covers the technical details but the impact on the business is also analyzed. So, it speaks to everyone - security teams and business leaders as well. Moreover, it also presents remedies specific to the client’s unique business context.
Vulnerability testing is not the only reason why clients eye security service providers. They often seek other supporting factors and a perfectly structured vulnerability assessment report is one of them. It is necessary to compile all the essential highlights, hidden causes, and mitigation strategies. This not only completes the cycle of security testing but also helps in laying out plans for the future.
