BLOG

BLOG
Your mobile apps are your business's face to the world. As an app creator or business owner, credibility is everything, and security is the cornerstone upon which it stands.
Now, with the digital ecosystem being highly susceptible to breaches, even a single slip in security can shatter the trust your users have in your brand, tarnishing the hard-earned credibility of your business. This is why mobile app security is key to your business’s growth.
|

To avoid becoming the next brand associated with a security breach, staying well-informed about the fundamental principles and the most recent advancements in mobile application security is essential. Think of this blog as a comprehensive overview of everything you should take into account when delving into mobile appsec. You will uncover why mobile app security goes beyond mere protection and why it's a strategic imperative for safeguarding your reputation and earning and maintaining user trust.
Before we dive into the technical deets, let's start by asking the fundamental question:
This is as straightforward as it gets: neglect mobile app security, and you're essentially leaving your organization's digital assets unguarded, available for the taking by cyber bullies.
Today, it's not a matter of 'if' but 'when' your vulnerabilities will be exploited.
The consequences? Stolen sensitive data, financial devastation, and a tarnished reputation that's often impossible to fully recover.
Consider mobile app vulnerabilities as the unlocked doors in a building. They provide the opportunity that attackers seek. But understanding these risks is the first step to defending against them. To put it in the words of Mike Assante, a renowned cybersecurity expert: "The cost of securing a system is inversely proportional to the cost of a breach."
It's a collaborative effort, with the CISO leading the charge, the CTO, and security experts working together to fortify your organization's defenses. While these security leaders may lay the groundwork, the responsibility of 'who stands guard' responsibility extends to every team member.
Consider a scenario where a team member, unaware of security best practices, unknowingly introduces mobile app vulnerabilities during a rushed development phase. These vulnerabilities may go unnoticed within the organization until a vigilant hacker seizes the opportunity to exploit them.
In the early days of mobile app development, security was often an afterthought. Developers focused more on functionality and aesthetics, often leaving vulnerabilities wide open. This laid the groundwork for the first wave of security breaches, where hackers exploited these weaknesses with relative ease.
Learning from these past incidents, the mobile app security landscape underwent a significant transformation. Organizations began recognizing the importance of robust security measures and mobile app vulnerability assessments. Encryption, authentication, and authorization became standard practices. The adoption of secure coding and regular security audits also gained momentum.
Fast forward to the present, and the mobile app security landscape has witnessed dramatic changes. Emerging trends and challenges continually shape our approach to safeguarding our digital assets.
The current state of mobile app security is marked by a dynamic interplay of factors. The rise of remote work and the bring-your-own-device (BYOD) trend have expanded the attack surface, making device and data protection more complex. Moreover, the ever-evolving threat landscape keeps mobile app security teams on their toes.
Regulatory requirements have also left a lasting mark. Regulations like GDPR and CCPA have compelled organizations to prioritize data protection and user privacy within their mobile apps. Compliance has become not just a matter of legal adherence but a symbol of trust and accountability in the eyes of consumers.
As businesses are evolving, the very technology that fuels their progress is becoming a source of vulnerability. Thus, in their ubiquity as the catalysts of efficiency and innovation, mobile apps are also the Achilles' heel of modern business, where vulnerability and necessity intertwine.
This isn't exclusive to a single industry or sector. Look at the examples of these industries, for instance:
Imagine a scenario where a mobile banking app's security falters, and customer data is compromised. The fallout would be catastrophic.
● Financial loss
Customers could face unauthorized transactions, leading to severe financial losses. The bank itself might incur significant liabilities and legal costs.
● Reputation damage
Trust, the cornerstone of the banking industry, would be eroded. Customers would flee, and the reputation of the bank would be tarnished, making recovery a huge task.
● Regulatory scrutiny
Regulatory bodies would swoop in, imposing hefty fines and stringent audits. Compliance failures might lead to severe repercussions.
Picture this - a healthcare app security breach jeopardizes personal health information. The consequences would be dire, like
● Patient safety
Treatment plans, medication schedules, and vital health data could be tampered with, endangering lives.
● Legal consequences
Lawsuits would pile up as patients sue for privacy violations, and healthcare providers would face enormous legal liabilities.
● HIPAA violations
Healthcare app security failures could result in HIPAA non-compliance, leading to hefty fines and a damaged reputation within the healthcare community.
Suppose security measures are insufficient and your data is compromised. In that case, the enterprise could anticipate:
● Data breaches
Sensitive corporate data, intellectual property, and trade secrets could fall into the wrong hands, leading to devastating consequences for the business.
● Operational disruption
Mobile app security lapses can disrupt day-to-day business operations, causing downtime, loss of productivity, and financial repercussions.
● Reputation and market value
A significant breach could ruin investor trust, causing a sharp decline in the organization's market value and financial standing.
Consider a security failure in mobile apps used for monitoring and controlling offshore drilling operations. It could lead to:
● Environmental disaster
A security breach could result in uncontrolled drilling, leading to environmental damage, wildlife disruption, and extensive cleanup costs.
● Safety risks
The safety of on-site personnel is jeopardized, and accidents could occur due to compromised control systems.
● Operational and financial impact
Downtime, equipment damage, and the costs of mitigating the breach would severely impact ONGC's operations and financial health.
Your organization's most valuable asset is not the physical infrastructure or the intellectual property locked away in vaults. It's the data – the lifeblood of your operations, the key to your customer trust, and the target of insatiable cyber threats. You need to implement stringent mobile app security measures to protect your business from data and application vulnerabilities.
One of these would be data encryption.
Where data is gold, encryption acts as the Fort Knox – an impenetrable fortress protecting your digital treasures. It's not just a precaution; it's an absolute necessity. Data encryption ensures that even if your mobile app's security is compromised, the data within remains a jigsaw puzzle for unauthorized access. It's the digital equivalent of sealing your data in an unbreakable safe.
Another one might sound like a saying, “Trust but verify." Authentication and authorization are the gatekeepers of your digital space. Robust authentication ensures only authorized users access your mobile app, while fine-grained authorization controls who can access what.
However, how can you guarantee comprehensive app security coverage beyond these fundamental practices? Let's delve into the five essential pillars that leave no room for security gaps and help you fulfill all security requisites.
Sure, you are protecting valuable data by securing your mobile app ecosystem. But you need to weigh in the other benefits too, because, in business, a singular benefit isn’t enough to invest in a service.
So, how else can mobile AppSec help you? Let’s have a look.
Meeting the set standards and complying with the applicable laws and regulations help businesses stay away from
● Security breaches,
● Data losses,
● Potential cyber risks,
● Lawsuits, and
● Financial trouble.
Compliance is so much more than an item on your to-do list; it helps your business stay ahead of hackers and maintain a solid relationship with your customers and regulators.
Early awareness and detection of potential risks help developers build a robust and secure app foundation which motivates the company to go for continuous innovation. This gives the business a competitive edge in a crowded market as it can roll out new features and app versions, eventually attracting new prospects.
Paying heed to mobile app security in your development phase lets you resolve security issues early, enabling you to cut down on unwanted disruption in operations. Besides, you don’t need to worry about spending extra bucks on recovering from cyber attacks or fixing the loose ends of your security framework.
So, to sum up, mobile app security is much more than mitigating the immediate threats. Investing in app security has a ripple effect as it positively impacts your business’s operations, reputation, and relationships with your customers and stakeholders.
A holistic security strategy against mobile app vulnerabilities is imperative for the complete protection of your business growth. While it comprises numerous intricate elements, here's a concise checklist of five pillars to kick-start your efforts.
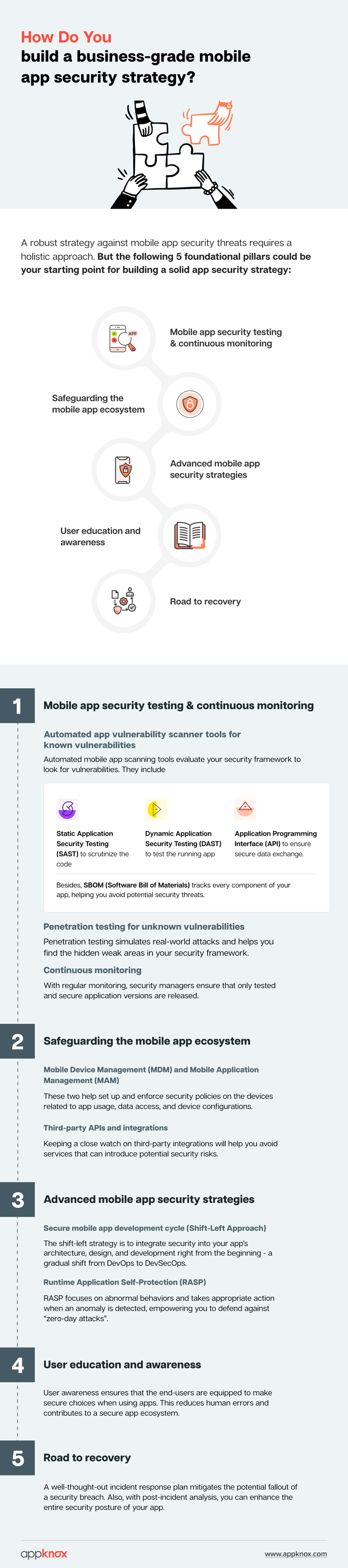
A. Automated app vulnerability scanner tools for known vulnerabilities
Automated mobile app scanning tools play a pivotal role in maintaining robust business security. They assess your security posture, especially for known vulnerabilities. This includes Static Application Security Testing (SAST) to scrutinize the code, Dynamic Application Security Testing (DAST) to test the running app, and API testing to ensure secure data exchange.
Additionally, Software Bill of Materials (SBOM) is an indispensable security solution that tracks every component within your mobile apps. It empowers you to stay ahead of potential exploits, maintaining a secured mobile application.
Penetration testing is the digital stress test, simulating real-world attacks to uncover the hidden weak links in your security chain. Pentesters specifically target unknown vulnerabilities, making it a crucial component in your mobile app security strategy.
Additional solutions, such as store monitoring, help security managers ensure that only tested and secured versions of applications go online.
MDM and MAM are responsible for ensuring that mobile devices used within your organization are secure. They help set up and enforce security policies on these devices, such as password requirements, data encryption, and remote wipe capabilities. These tools also help in enforcing policies related to app usage, data access, and device configurations.
B. Third-party APIs and integrations
Many mobile applications integrate with third-party services or APIs to expand their functionality and offer additional features. These integrations can introduce potential risks, such as security vulnerabilities, data breaches, or privacy concerns, especially if the third-party service is not trustworthy or adequately secured.
A. Secure mobile app development lifecycle (shift-left approach)
In traditional development approaches, security might be considered an afterthought, but now, it's a fundamental component right from the beginning. This means that security measures are not added on as a patch but are built into the app's architecture, design, and development stages. This is the shift-left movement from DevOps to DevSecOps.
B. Runtime Application Self-Protection (RASP)
RASP can detect and respond to security threats in real time, preventing attacks from causing harm before they even begin. It offers a level of protection that is impossible with traditional security measures that may only identify threats afterward. RASP understands the behavior of the application it protects. It can differentiate between normal operations and suspicious activities, allowing it to take appropriate action when an anomaly is detected.
It can defend against previously unknown or "zero-day" attacks because it focuses on abnormal behavior rather than relying on known attack signatures.
User education and awareness are about ensuring that end-users are informed and equipped to make secure choices when using mobile apps. For instance, users are often targeted by phishing attempts, where malicious actors try to trick them into revealing sensitive information like passwords or personal data. Educating users on recognizing and avoiding phishing attempts helps prevent data breaches and unauthorized access.
Overall, it reduces the risk of human errors and promotes a culture of security, ultimately contributing to a safer mobile app ecosystem.
A. Crafting a mobile app security incident response plan
A well-crafted incident response plan is your shield against the potential fallout of a security breach. This plan should be tested and refined through simulations to ensure that your organization can effectively mitigate the impact of a security breach when it occurs.
B. Learning from mobile app security breaches
Post-incident analysis is not just a routine but a strategic necessity, offering crucial insights to elevate your security posture. Post-incident analysis aims to pinpoint the vulnerabilities and weaknesses in your mobile app security infrastructure that allowed the breach to occur. This goes beyond the immediate breach and extends to the overall security strategy.
Within the mobile app security niche, you'll find a wealth of case studies on real-world breaches. These cases, whether involving a major data breach at a financial institution or the exploitation of a vulnerability in a popular social media app, offer tangible examples of security measures faltering. Explore some of these recent data breaches in our blog.
The ROI conundrum in mobile app security often presents a challenge for organizations. How can you achieve the highest level of protection for your digital assets without breaking the bank?
Here, the fundamental principle is clear - you should invest wisely rather than extravagantly. You can consider the following:
A fundamental starting point is understanding the potential costs of a security breach.
● According to IBM's 2021 Cost of a Data Breach Report, the global average data breach cost was $4.24 million.
● Violations of data protection regulations, like GDPR, can result in fines of up to €20 million or 4% of global annual turnover, whichever is higher.
With these figures in mind, let's do some calculations:
Suppose your organization has a yearly revenue of $100 million. A data breach that leads to regulatory penalties could result in a fine of $4 million. This alone would represent a 4% loss of annual revenue, not to mention the costs associated with the breach itself, the loss of business, and the legal expenses.
Building security solutions in-house can seem cost-effective but often involves significant hidden expenses. For instance, developing and maintaining proprietary security software may require a team of specialized experts, ongoing training, and constant updates to keep up with evolving threats.
In contrast, buying established security solutions can prove more efficient even with initial licensing costs. For instance, a security software license might cost $100,000 per year, while the equivalent in-house team's salaries, benefits, and ongoing training could easily exceed $500,000 annually.
Consider the scalability of your chosen security solutions. Mobile app security requirements change over time, and what works today may not suffice in the future. For instance, investing in scalable cloud-based security solutions ensures you can adapt without extensive additional costs.
As a business owner, you know the investment in time and resources that goes into building your mobile apps. Yet, it all hangs in the balance when the security of your creations is overlooked.
So, it is safer and wiser to invest in a more proactive approach to your mobile app security threats than a reactive one when the damage would already have been done.
Whether you're running a startup or steering the ship of a Fortune 500 business, prioritizing and investing in mobile app security remains crucial. To ensure that every dollar invested in your mobile app security finds its best worth, we offer not just security but clarity.
Connect with our security experts today and understand how we can help you scale your mobile app security.
.jpg?width=50&height=50&name=10606600_10204086667262761_7381430219125488912_n%20(1).jpg)
Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
