
BLOG

BLOG
Most developers and security researchers in charge of compliance need help with the complexity and volume of standards that MASVS (Mobile Application Security Verification Standard) encompasses, including a vast array of standards that are daunting to comprehend and implement effectively.
Transforming abstract security principles into secure coding practices can be a significant hurdle, and most developers often lack the readily available resources and practical examples to integrate MASVS recommendations seamlessly into their development workflow.
To overcome this, we’ve compiled a guide with an actionable list of activities to comply with for each MASVS ID to demystify MASVS compliance.
While working towards a mission of building better, more secure mobile applications, the Open Web Application Security Project (OWASP) has spearheaded this effort with the Mobile Application Security Verification Standard (MASVS) and the Mobile Application Security Testing Guide (MASTG). These invaluable resources provide a comprehensive framework for safeguarding your mobile apps, ensuring trust, and protecting user data.
The OWASP Mobile Application Security Verification Standard (MASVS) serves as the industry's north star for mobile app security, providing a standardized framework that harmonizes security requirements across the mobile ecosystem. Created by the OWASP Foundation, MASVS offers clear, actionable security guidelines to help development and security teams build secure mobile applications.
MASVS is especially valuable because it aligns development with security best practices from the ground up, ensuring that security is integrated at every mobile app development phase. This helps teams identify and fix vulnerabilities early, minimizing the risks of future data breaches and strengthening overall app integrity.
At its core, MASVS recognizes that not all apps need the same level of security. It offers three distinct verification levels to match your application's risk profile:
MASVS offers a robust set of security requirements addressing diverse vulnerabilities, from data encryption and authentication to secure storage and code practices. However, the sheer volume and technical intricacy of these standards can present significant challenges for users navigating the vast information on the OWASP website.
Implementing MASVS through a structured checklist approach breaks down an overwhelming security framework into manageable, actionable steps. While ad-hoc security implementations often leave gaps, a systematic checklist ensures comprehensive coverage and consistent security practices across mobile applications.
A well-designed MASVS checklist serves as both a roadmap and a quality gate. It enables development teams to integrate security naturally into their workflow rather than treating it as a last-minute compliance exercise. This proactive approach typically reduces vulnerability remediation costs and security-related rework by 60-70%.
For security leaders, the checklist approach provides clear metrics for security maturity and compliance tracking. It creates an auditable trail of security decisions and implementations, proving invaluable during security assessments and stakeholder discussions.
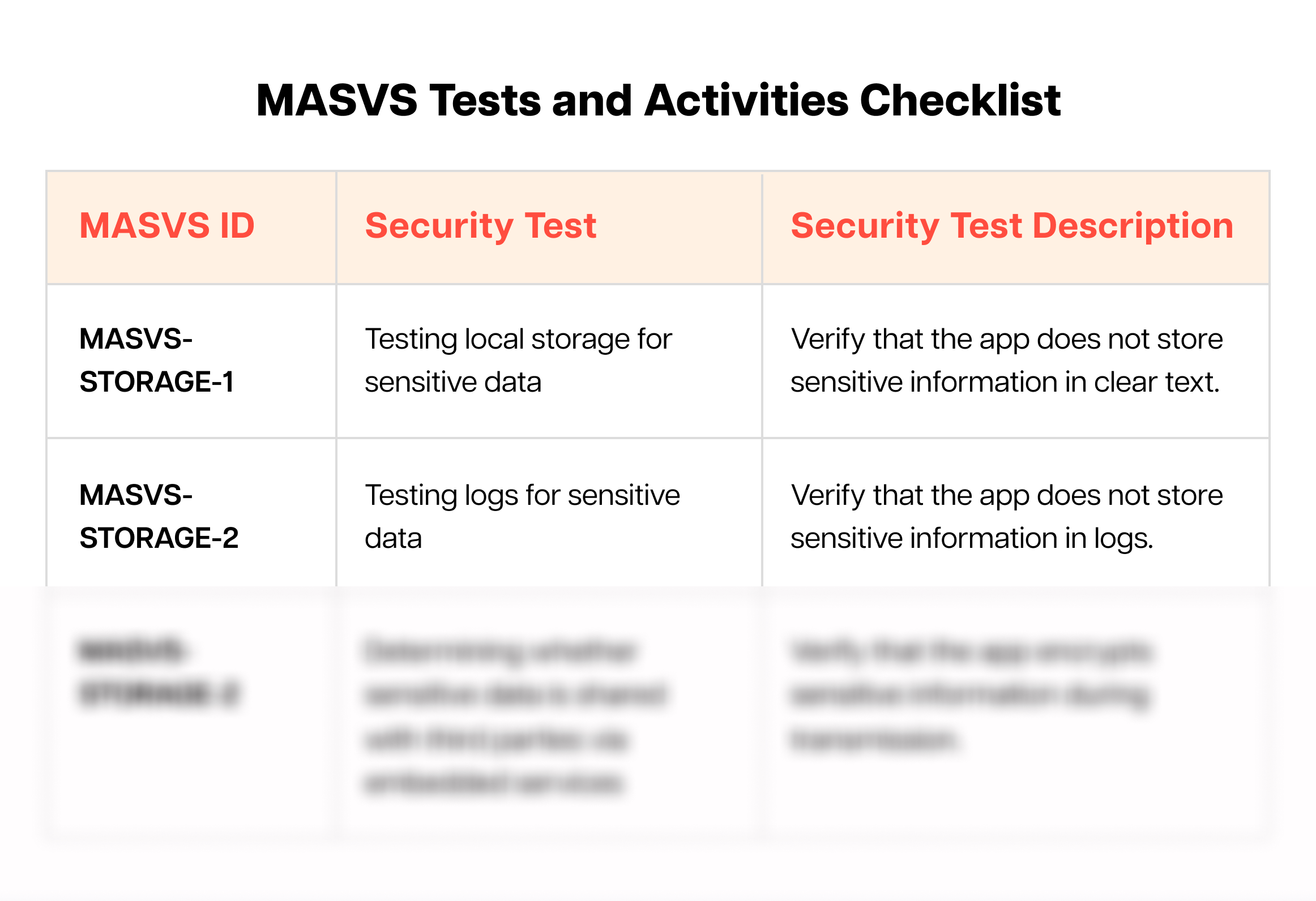
The following actionable OWASP MASVS checklist prioritizes the standards based on risk, impact, and ease of implementation. It will help you focus your efforts on the most critical areas first, maximizing their impact.
Each standard in the checklist can be broken down into actionable activities, providing a roadmap for implementation. This clarity empowers you to take concrete steps toward compliance and bridge the gap between theory and practice.
For those wanting to jump to the list of standards that the vulnerabilities in your applications violate, feel free to check it out here. For the rest, here’s the mobile application security testing checklist.
Integrating the MASVS checklist into the development process can streamline security efforts and improve mobile app resilience. Here’s a step-by-step approach to implement it effectively:
This may seem a bit overwhelming, and honestly, it is.
That's why we started building Appknox. Think of it as the technical reason why Appknox exists.
At Appknox, we’re committed to simplifying mobile application security in tangible ways. One way is to help security custodians within organizations automate compliance regulation and focus more on core competencies like developing applications faster and more efficiently.
To do so, Appknox has a dashboard built into the product that gives you a comprehensive report of which vulnerability compromises which compliance, including MASVS and MASTG, thus saving you the effort of mapping vulnerabilities back to compliance standards. This is an extension to the automated vulnerability assessment, including SAST, DAST, and API testing.
Appknox also has downloadable reports in various formats, including Excel sheets, where you can filter out vulnerabilities that violate one or more compliances. 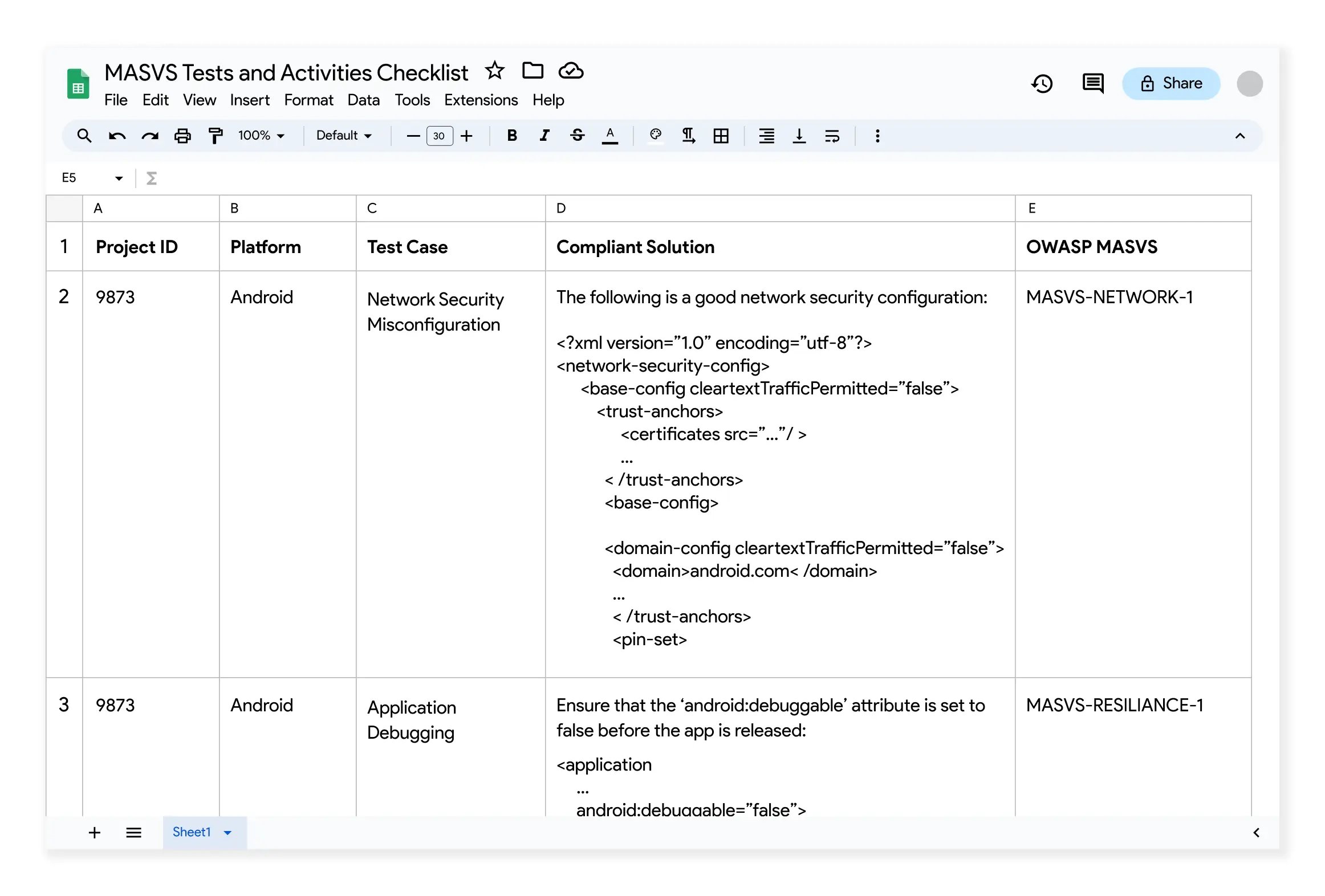
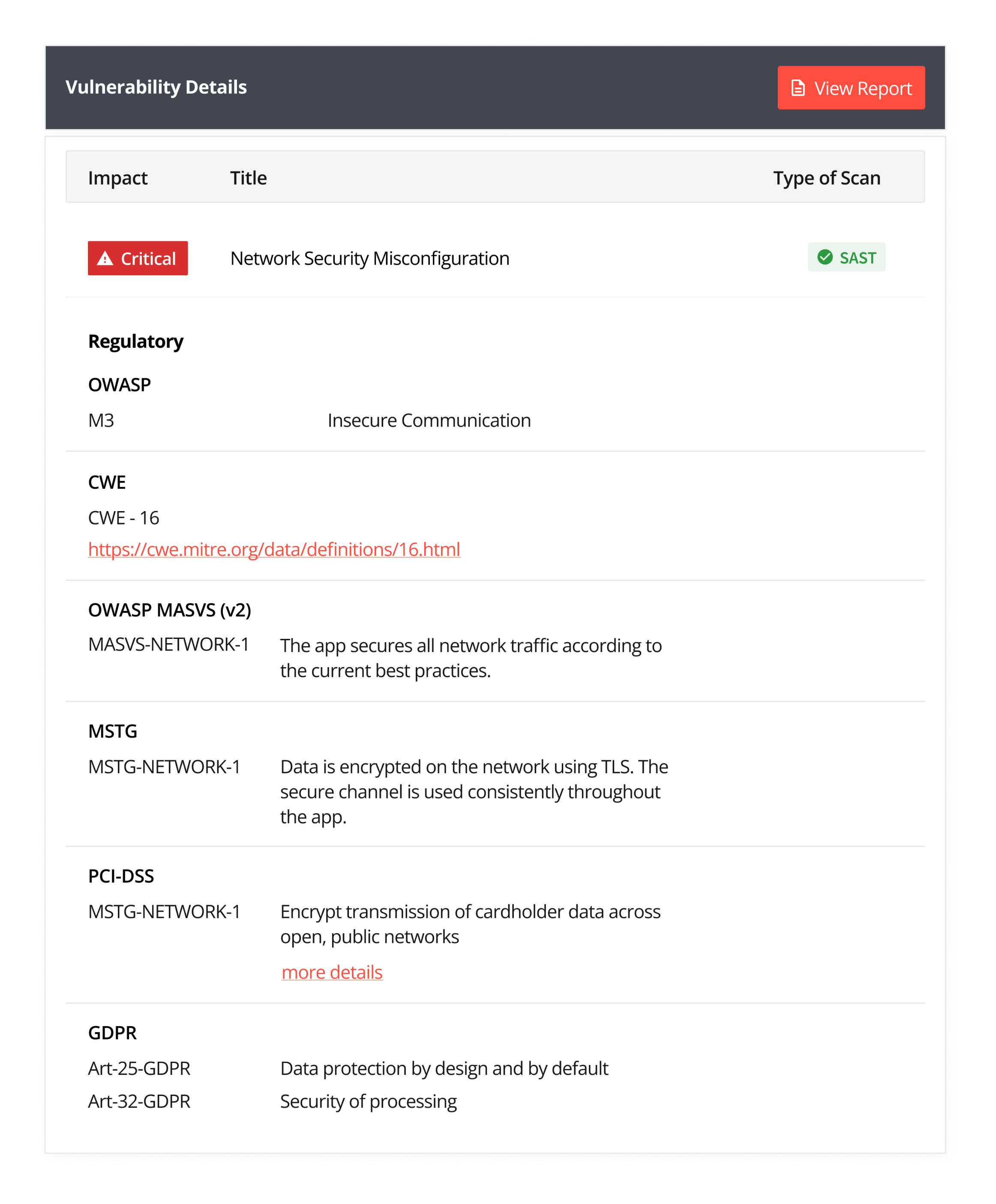
Appknox’s binary-based security tool revolutionizes application safeguarding and ensures meticulous analysis. It pinpoints vulnerabilities with unparalleled precision, enabling comprehensive remediation strategies and improving applications' security posture.
If you’re ready to get your vulnerability assessment automated, speak to us and see how we can help you spend your time on meaningful tasks like building applications efficiently.
Schedule a demo with a security consultant now!

