
BLOG

BLOG
JSON Web Token or JWT is a secure open standard way, which securely helps in transmitting all the information between two respective parties. JWT can be signed with the help of any secret key with a proper algorithm. When systems exchange confidential data, the JSON secure app is used, which helps in identifying the user without any private credentials. JWT is currently the latest technology used by app development services, which helps in securing the APIs.
API is the application programming interface, which helps in communication between two applications. API is used in the iPhone applications, which can be designed by the iPhone app Development Company. When you use an application and you get a response from it, it is due to this software programming interface. Now, there is a need to secure APIs, which can be done with the help of JWT. The app development services help you to secure the API with the help of JWT.

API is a software protocol that helps interaction between the client and the server. API is known to be a profound entity. App development services are securing API with the help of JWT. It is capable of accepting and also responding to the protected requests by the users and its clients. These API must be well equipped to ensure safety and check the authenticity of the data, which the client tries to access.
The procedure of certifying the identity of clients, accessing the resources on the server is API authentication. API authentication is a must for the iPhone application, which the iPhone app Development Company can design for you. It actually authenticates and certifies the users, who are accessing the server for information.
API is authenticated with the help of app development services in your mobile applications. API management and authentication help your mobile applications to work securely. JSON web tokens build an app, which has encoded confidential data, to provide security.
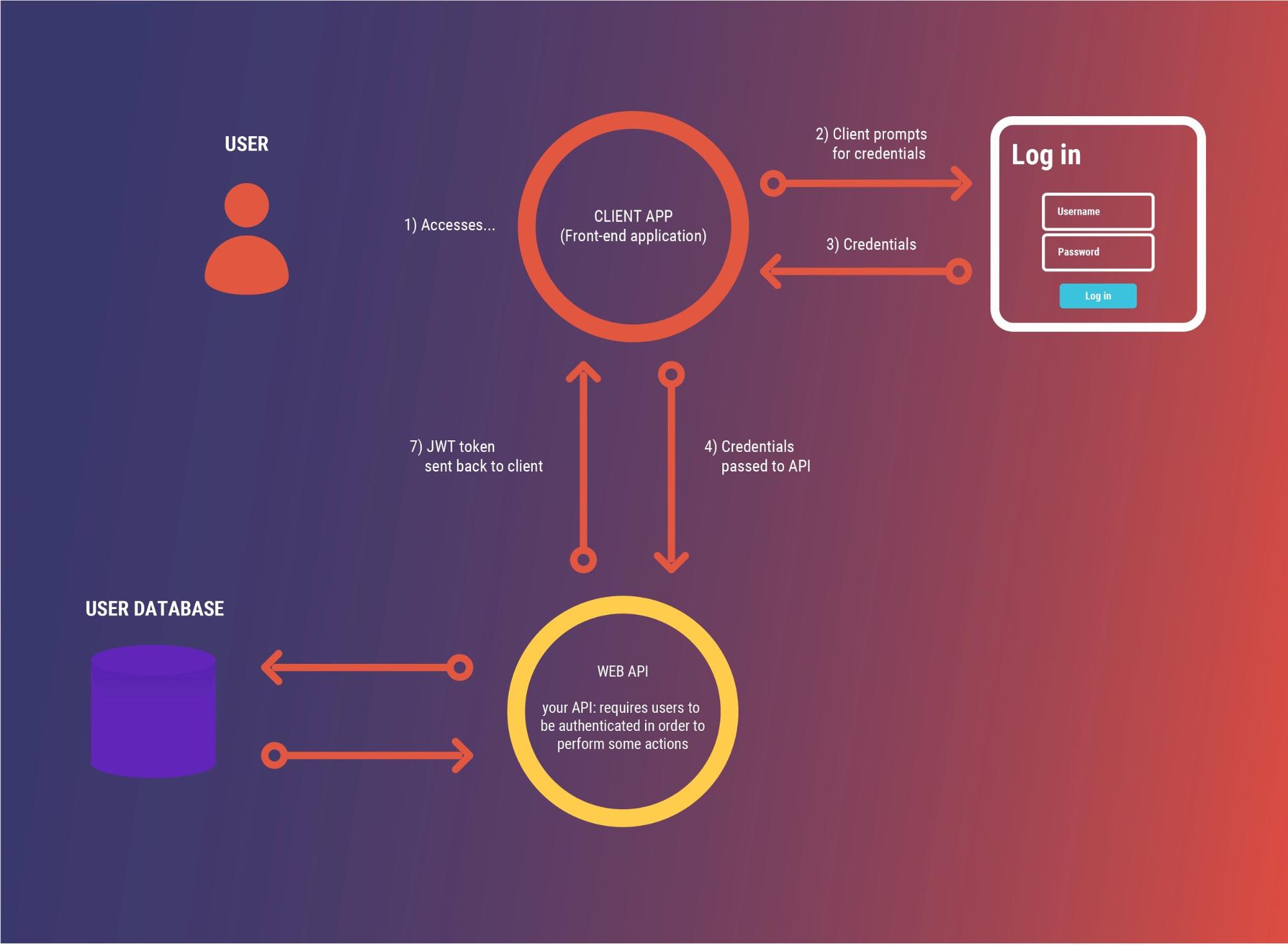

Applications are now facing threats and hacking. The API can be secured with the help of JWT tokens. The application and confidential data remain secured. Adding JWT token security to your API will provide full protection. App development services secure your API with JWT security, which is affordable and the best security method. JWT is the best technology for heavy load web applications. It is the best technology, providing a secured API.

