BLOG

BLOG
Gartner Hype Cycle for 2023 assesses the levels of maturity, adoption, and societal effects associated with emerging technologies in the field of Application Security.
The 2023 report serves as a valuable resource for organizations seeking insights into the influence of security technologies on their applications. It also highlights the market leaders in the respective fields - Appknox being this year's leading vendor in mobile application security testing.
Appknox has consistently featured among notable vendors for Gartner, with a recent recognition in DevSecops tools for secure software delivery.
This blog will focus on the essential takeaways from the 2023 Gartner Hype Cycle report, specifically concerning Application Security Testing (AST) – a critical technology trend.
Let's begin by introducing the 2023 Gartner Hype Cycle for AST.
Gartner Hype Cycle is a graphical representation and methodology developed by the research and advisory firm Gartner Inc. It provides a way to track and understand the adoption and maturity of emerging technologies and trends over time. The Hype Cycle highlights the typical stages that technologies or concepts go through as they evolve from early inception to mainstream adoption and sometimes decline.
The key stages in Gartner Hype Cycle are as follows:
1. Innovation Trigger: This is the starting point of the cycle. It represents the point at which a new technology or trend is introduced or discovered, generating initial excitement and interest.
2. Peak of Inflated Expectations: As the technology gains attention and hype, expectations about its potential benefits tend to skyrocket. During this phase, media coverage and marketing hype are at their peak, and there may be an overestimation of the technology's potential impact.
3. Trough of Disillusionment: As reality sets in and the initial promises face challenges and limitations, the technology often enters a period of disillusionment. This phase is characterized by a decrease in interest and sometimes skepticism about the technology's practicality and viability.
4. Slope of Enlightenment: Some technologies find more practical and productive applications after passing through the Trough of Disillusionment. Learning from initial failures, the technology begins to mature, and organizations gain a better understanding of its true value.
5. Plateau of Productivity: In this final phase, the technology reaches a state of widespread adoption and becomes integrated into mainstream practices. Its benefits are well-understood, and it becomes a stable and reliable solution.
Gartner Hype Cycle is not only applicable to technological innovations but can also be used to analyze the maturity and adoption trends of various other concepts or trends, such as emerging business models, societal changes, and more. It is a valuable tool for organizations, businesses, and decision-makers to identify and understand where a technology or trend stands in terms of its lifecycle and potential impact.
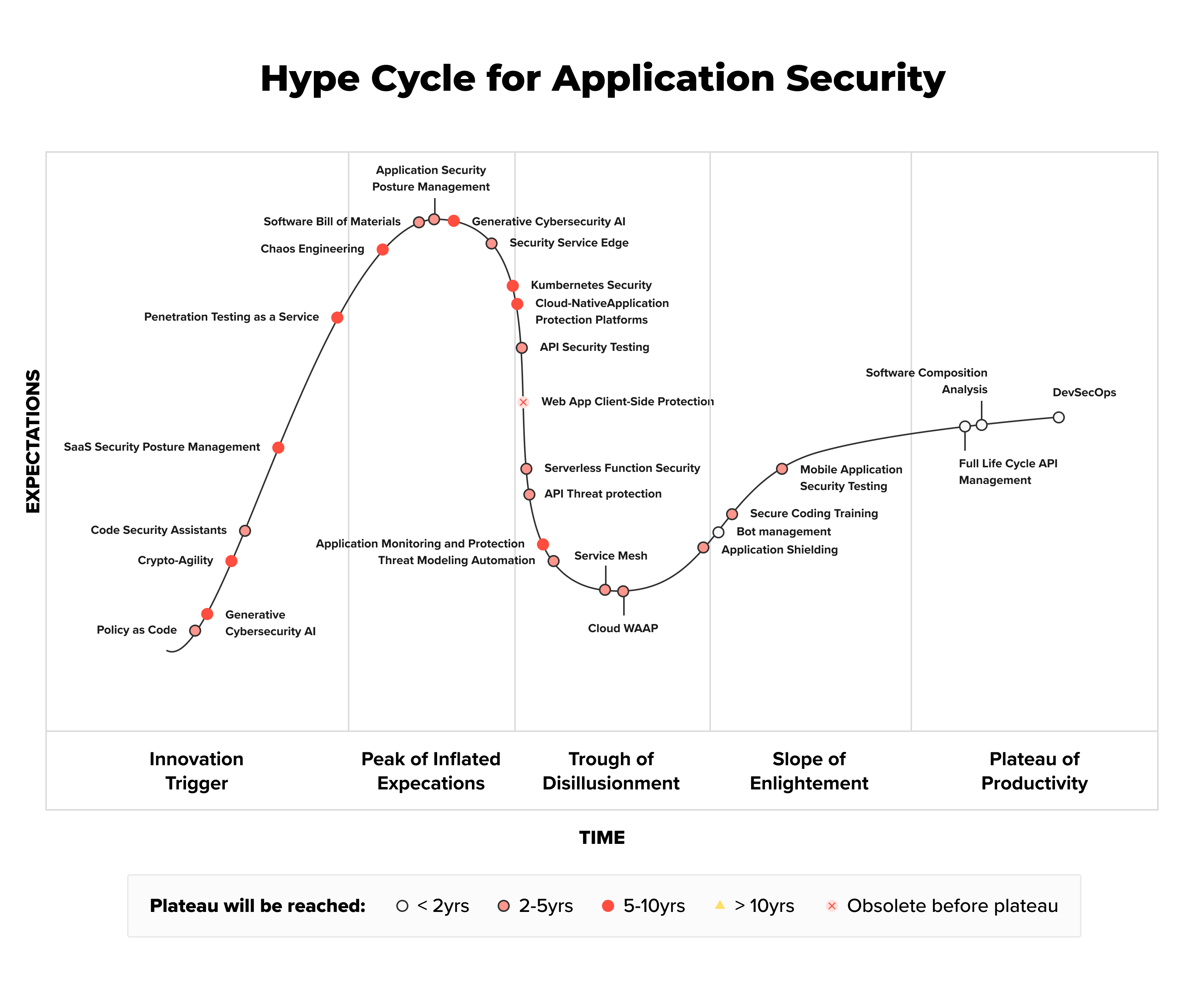
Application security, driven by the mature and widely adopted DevSecOps discipline, continues to face challenges in various organizations. However, promising innovations are emerging to tackle these issues.
For instance, application security posture management (ASPM) enables the implementation of DevSecOps policies. A recent innovation, policy as code (PaC), empowers security teams to enforce security policies and auditing controls effectively. Another notable development is the recognition of secure code training as a standalone discipline, emphasizing the importance of skill development.
As businesses transition their applications to the cloud, they require comprehensive tools that span development to runtime, covering both application and infrastructural aspects.
Cloud-native application protection platform (CNAPP) tools exemplify this by offering integrated container and infrastructure as code scanning, cloud security posture management (CSPM), and runtime workload protection. The focus on API threat protection addresses the architectural aspect of modern applications, which heavily rely on APIs.
The increasing prevalence of software supply chain attacks highlights the need for software supply chain security (SSCS). This evolving discipline encompasses various concepts, including securing development environments, software composition analysis (SCA), and software bills of materials (SBOMs).
Appknox Recommended Reading: Benefits of SBOM in Software Supply Chain Security
Generative AI poses a dual role in application security. While it facilitates attacks by malicious actors, it also aids organizations in enhancing security through innovations like secure code assistants and generative cybersecurity AI. These technologies automate tasks such as identifying and remedying application vulnerabilities.
Securing not just homegrown applications but also third-party and SaaS applications is becoming a pressing concern. To address this, SaaS security posture management (SSPM) solutions offer robust security posture and identity controls. As the application security landscape evolves, these innovations play a vital role in safeguarding digital assets from potential threats.
In this year's Application Security Hype Cycle by Gartner, there are seven transformational innovations. Among these, three have garnered significant hype and are now being adopted by organizations benefiting from their implementation and striving to adapt them to their specific contexts.
Security Service Edge (SSE): SSE is responsible for securing user access to web services, cloud services, and private applications. It offers adaptive access control, data security, and enhanced visibility.
Application Security Posture Management (ASPM) Tools: ASPM tools help manage application risk by collecting, analyzing, and prioritizing security issues. They enable the enforcement of security policies and facilitate the remediation of identified vulnerabilities.
Software Supply Chain Security (SSCS): SSCS refers to the set of processes and tools used to curate, create, and consume software in ways that mitigate attacks against software and prevent it from becoming an attack vector.
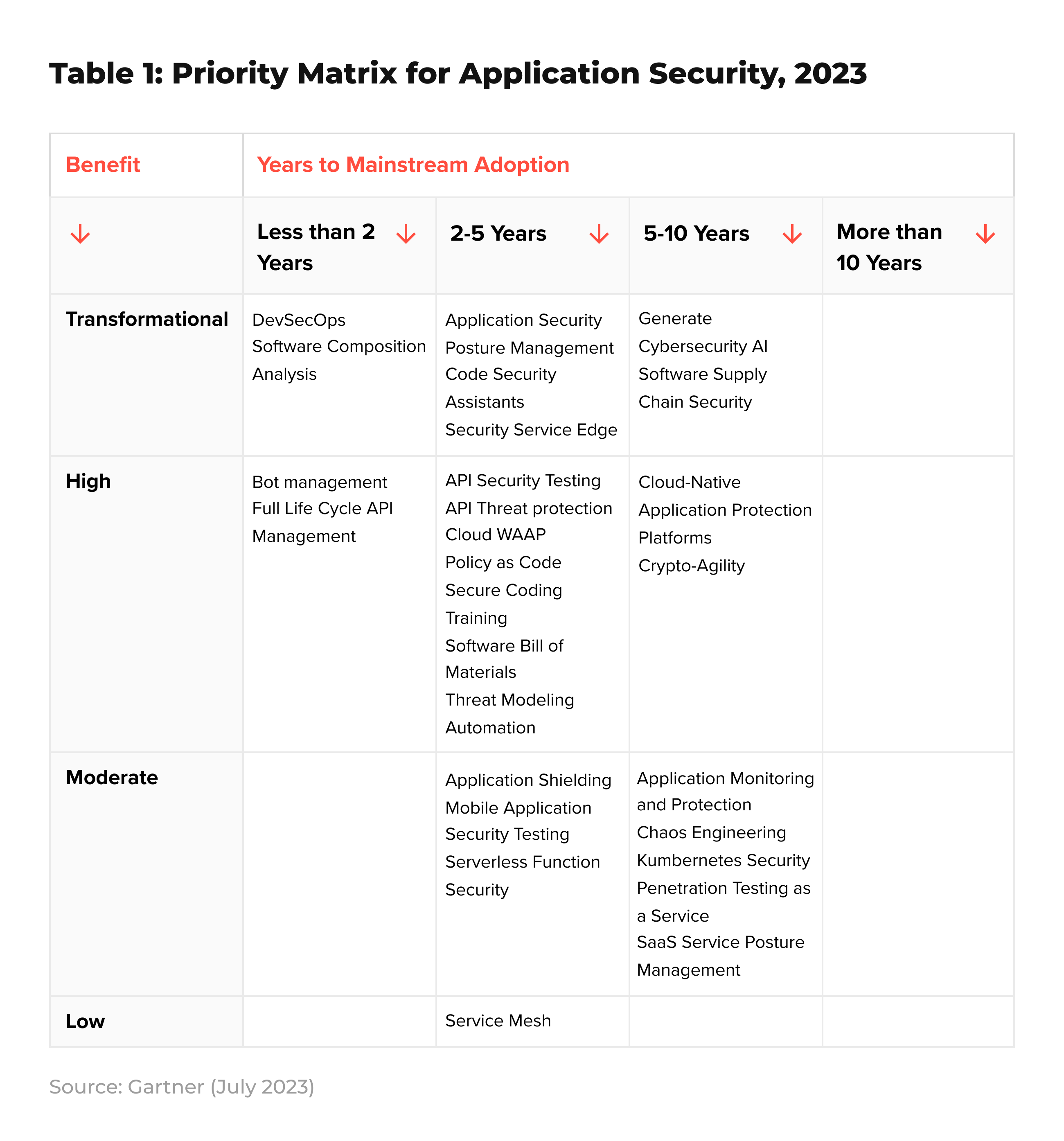
Two recently emerged innovations are rapidly evolving:
Code Security Assistants: These utilize artificial intelligence to aid developers in identifying and resolving security vulnerabilities present in their code.
Generative Cybersecurity AI: This innovation streamlines and accelerates various cybersecurity tasks, such as reporting and code remediation, through the application of AI technologies.
Several innovations have been excluded from this year's Hype Cycle. Some, like web application firewall appliances, have already achieved full maturity. Others, such as enterprise app stores, DevOps test data management, externalized authorization management (EAM), privacy by design, and digital product analytics, are still in the process of maturing and are featured in different Hype Cycles.
Nevertheless, due to the revised scope of the Hype Cycle for Application Security and the introduction of new innovations this year, they have been omitted from this particular Hype Cycle.
Mobile applications play a crucial role in a company's digital transformation. It is imperative to ensure that these apps are free from vulnerabilities that could be exploited, as this is vital for facilitating the transformative journey. Mobile Application Security Testing (AST) largely employs techniques similar to traditional AST but is tailored for the mobile device environment and its agile development processes.
Mobile Application Security Testing (AST) is utilized by various stakeholders within an organization, depending on its structure. This includes security and application development teams; in some cases, it may also be directly employed by line-of-business departments.
While security testing is crucial for any organization delivering mobile applications, industries subject to regulations and high-security requirements, such as financial services, healthcare, and online retail, have a greater sense of urgency to embrace mobile AST.
Key Drivers:
Key Obstacles:
|
In the 2023 Gartner Hype Cycle report, Appknox has been recognized as a leading vendor for mobile Application Security Testing (AST). With our range of Automated Vulnerability Assessment products and Penetration Testing offerings, Appknox is highly esteemed as a reliable provider of security solutions by the Fortune 500, earning trust from both Gartner Peer Insights and G2. |
Appknox offers one of the most advanced plug-and-play mobile application security testing solutions embedded with innovative vulnerability assessment and penetration testing tools which help security experts and developers build the safest mobile applications.
Experience the power of our industry-leading Vulnerability Assessment (VA) tools, expertly enhanced by our skilled pentesters. Discover and address security vulnerabilities and software defects at the earliest stages of development. With our advanced security test cases, rest assured that your application software is resilient, trustworthy, and meets all necessary compliance standards.
Eager to get started? Book our free trial to understand why Gartner recommends Appknox and enhance your journey in the mobile app security curve.
Alongside the possibilities and potential risks, each technological breakthrough is often surrounded by a wave of hype.
Throughout the various stages of the hype cycle, making informed decisions can enable the effective adoption of the technology when it aligns with your unique use case and business needs. Given the ever-evolving threat landscape, informed decision-making becomes even more critical for mobile application security.
Gartner also suggests the following best practices for mobile app owners:
Unlock the power of best practices for your applications with Appknox security experts - consult today!
The five phases of the Gartner Hype Cycle are as follows:
The key uses of the Gartner Hype Cycle are:
The Gartner Hype Cycle is critical for mobile application security testing (AST) as it provides valuable insights and guidance for organizations looking to adopt and implement effective security measures for their mobile apps. Here's how the Hype Cycle is essential for mobile application security testing:
.jpg?width=50&height=50&name=10606600_10204086667262761_7381430219125488912_n%20(1).jpg)
Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
