BLOG

BLOG
MiTM or Man-in-the-middle attack is one of the most common cyberattacks that online users must be aware of. Anyone who’s actively connected to the internet for both work and entertainment purposes is at risk of being a victim of a MiTM attack.
Fortunately, you can prevent the above from happening. This blog is here to help. Below, we’ll discuss MiTM attacks, their types, how they work, and how to prevent becoming a victim.
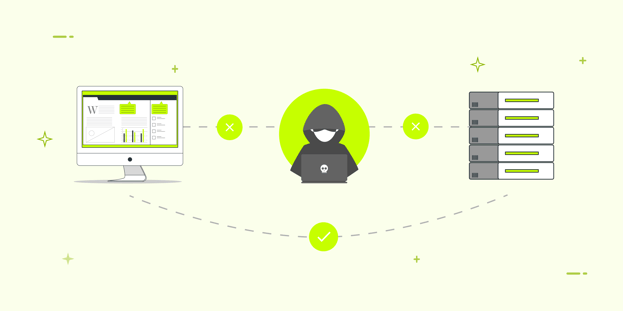
Man-in-the-middle (MiTM) attack is a type of cyber-attack wherein the cybercriminal (man-in-the-middle) intercept the communication between two parties (the user and the web server). The motive here is to gain unauthorized access to confidential information and use the same for financial gains or other illicit actions.
As the cybercriminal acts as one of the parties involved in the transaction or information transfer, this attack becomes hard to detect and thus poses a huge risk.
Let’s understand how a MiTM attack works with an example.
Imagine there are two individuals, Jack and Bob. And then there’s an attacker. Bob and Jack are exchanging information via email or other channels.
The attacker gains access to the channel via some tool and intercepts, listens, or reads the conversation without Bob and Jack knowing. The attacker adds or removes essential information, i.e., alters it, leading to damage. And that’s how a typical MiTM attack works.
Here are the most common types of MiTM attacks:
Think of IP spoofing as identity theft. Here, cybercriminals change or tweak the source of the IP address of the email, device, or website to mask it. This makes the users believe they’re interacting with a genuine source. And because of this, they continue to send and receive data which ends up with the cyber criminals.
HTTP is a security protocol that gives a sense of safety to the users. However, it isn’t as secure as the HTTPS protocol, which uses SSL to encrypt HTTP requests and responses and sign them digitally.
During an HTTPS spoofing attack, the attackers redirect the browser session from a secure HTTPS website to a not-so-secure HTTP-based webpage without the user’s consent. The attackers can then access and steal confidential information without informing users.
In this type of MITM attack, the attackers tweak the domain names of genuine websites to redirect the users to fake websites. The users are in the illusion of landing on a safe webpage while they land on a suspicious website meant to capture login credentials and other confidential data.
Emails are one of the most common channels attackers choose for hacking. Recent statistics convey that 92% of the malware is sent via email.
Here the criminals try to access the emails registered with banks and other NBFCs (non-banking financial companies). This allows them to monitor the transactions the users are making.
Also, cybercriminals can spoof the bank’s official email and send instructions to customers leading them to transfer the money to the criminals.
Secure Sockets Layer or SSL is a protocol that encrypts the connection between the web servers and your browser. During SSL hijacking, cybercriminals might use a computer and access the secure server to decipher and intercept the data traveling to and from the user’s computer and server.
This type of man-in-the-middle attack happens when you connect to public WI-FI networks that aren’t usually password protected. Hackers take advantage of this and use open WIFI networks to access and steal the data of all the users on the network.
Aka ARP (Address Resolution Protocol) cache poisoning is a popular MiTM attack wherein cybercriminals on the same subnet as their victims try to eavesdrop on the traffic between them.
This attack happens when cybercriminals steal information such as passwords and user IDs stored in the browsers’ cookies during a browsing session. Sometimes the access is temporary, but in several cases, the hackers gain permanent access to users’ paid online memberships.
Here’s how:
The first step toward preventing MiTM attacks is to be aware of the risks around you and avoid them.
For instance, users must know that websites that display “HTTP” in the URL bar can be risky. Users should avoid such websites and visit the ones that display HTTPS in the URL bar. You’ll also see a padlock icon in the URL bar, indicating the website is secure.
In addition, users should not connect to unsecured public WI-FI connections as they’re under the radar of cybercriminals.
Cybercriminals or marketing agency send phishing emails from genuine-looking email addresses to fool the users. The motive is to get the user to click on the link in the email. And when the user does click on the link, they’re prompted to enter payment or other details, post which the data is hacked.
However, nowadays many marketing agency are using attractive email templates so users can click and users becoming a victim of this scam. For starters, make sure that you open only the emails that come from verified sources. Very carefully examine all emails you open, and do not click any link until you’re sure.
If you extensively use the internet and browse different websites, consider using a virtual private network.
A reliable VPN provider, such as ExpressVPN, encrypts your internet connection and all your online transactions. Also, using a VPN makes your IP address hard to track. This way, you can remain anonymous when browsing online.
Organizations must integrate a corporate VPN and make it mandatory for employees to log in. This will be useful if the employees are working remotely.
Both individuals and organizations must integrate internet security products such as anti-malware solutions. As MiTM attacks require malware for execution, integrating an anti-malware solution can help prevent such efforts.
Internet literacy can substantially reduce the occurrence of cyberattacks. Organizations must make their employees aware of the potential risks and educate them so they can implement the security best practices to prevent severe consequences. The same goes for any other individual who uses the internet frequently.
Around 2,200 cyber-attacks happen daily, which amounts to 1 cyber attack every 39 seconds. By the time you finish reading this blog, several users will have become victims of cyber attacks such as MiTM and more.
So, wait no more and implement the security best practices above to prevent MiTM attacks and safeguard your data and assets effectively.
Here are some signs that you can look for to detect MiTM attacks:
Here’s how cybercriminals usually execute a MiTM attack:
Let’s say there’s an exchange of information or data between two parties. The cybercriminal, using specific tools, hacks into the system and acts as the middleman between the two parties, and tries to intercept information before it reaches the destination. A standard spoofing method is WI-FI eavesdropping, wherein hackers take advantage of innocent individuals on the same network and intercept and steal their information.
Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
