BLOG

BLOG
In 2017, Equifax, a major American credit bureau, became a cautionary tale in the importance of robust cybersecurity practices. It overlooked critical vulnerabilities in its systems, failing to address a known security flaw in its Apache Struts web app framework.
This oversight resulted in the data leak of 143 million customers, costing Equifax $1.38 billion in making breach compensations and upgrading its IT systems.
|
.png?width=680&height=1745&name=Equifax%20Data%20Breach%202017%20(1).png)
Testing for vulnerabilities in mobile applications is equally important as they interact with different devices, network infrastructure, servers, and third-party APIs.
Mobile apps are a part of the larger ecosystem and are susceptible to myriad security vulnerabilities. They include data leakage, unsafe data transmission, insecure data storage, poor encryption, malware, code tampering, and weak spots in server-side APIs.
Considering the wide scope of potential mobile app threats, regardless of your app’s size, purpose, or industry, mobile application penetration testing needs to be an integral part of your mobile app development process.
Plus, the increasing sophistication of cyberattacks and compliance regulations compel organizations to invest in mobile app penetration testing.
Throughout this article, we discuss the importance of mobile application penetration testing to discover vulnerabilities, prevent future attacks, and test the responsiveness of your security and app development teams.
Modern applications hold sensitive information for various commercial purposes, including healthcare, banking, and education. Since they interact with multiple devices and third-party APIs, they are vulnerable to attacks from cybercriminals who can gain access through login credentials, third-party open-source repositories, and other means.
.png?width=680&height=1017&name=Mobile%20application%20penetration%20testing%20is%20important%20because_%20(1).png)
Mobile security testing involves finding and fixing vulnerabilities using manual or automated testing to analyze the application, identify potential security flaws and misconfigurations in back-end services used by the app, and ensure the mobile application is not vulnerable to attacks.
In 2021, Klarna, a widely-used payment app, suffered an application flaw. On May 27, for a brief period of 30 minutes, users who logged into the Klarna app accidentally got access to other users’ accounts. This mishap, attributed to human error, resulted in the unintended exposure of sensitive personal and credit card information of several customers. - Reuters
Before we dive deep into this, it is first important to understand why mobile app pen testing is important for your business.
After all, one just cannot overlook the benefit of penetration testing.
According to IBM, the global average data breach cost in 2023 was USD 4.45 million - a figure that is significantly more than the expenses incurred in mobile application security and penetration testing.
No wonder mobile apps face a string of unique security threats that, if ignored, can have serious consequences for you, such as:
More importantly, you must analyze metrics to quantify the added value in terms of enhanced security and risk mitigation.
Mobile application penetration testing extends to a range of activities. It covers everything, from reviewing fragile codes and configuration errors to fixing poor authentication and authorization standards.
However, the process is not free from challenges.
The security weaknesses in mobile devices differ greatly from those found in websites and web app environments. They may be susceptible to input validation issues like SQL injection or cross-site scripting (XSS).
Mobile apps interact with backend servers, and there is no control over how the information gets transmitted and over what channels, putting user data at risk. This increases the scope and complexity of testing and requires the testers to deeply understand mobile architectures, network security, and encryption standards.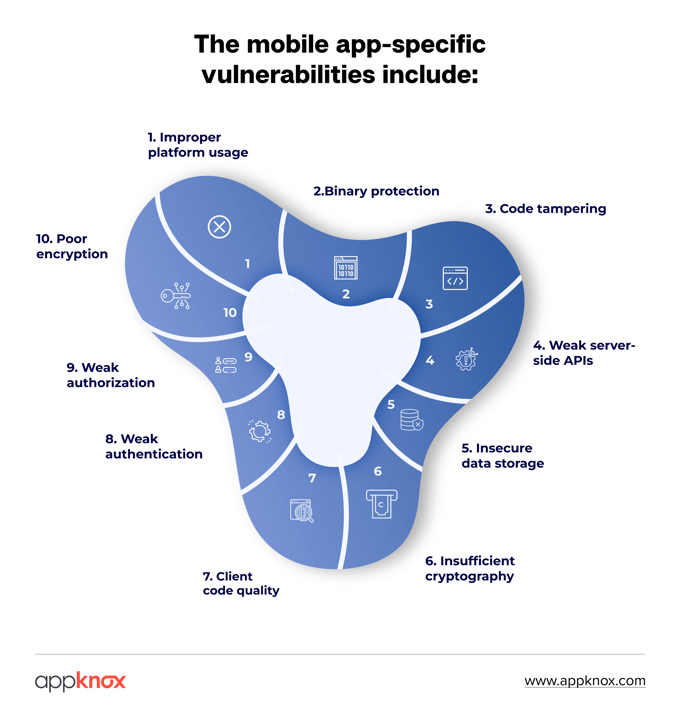
Mobile devices have unique hardware and software configurations, which complicate mobile pentesting. With the release of new mobile models and software versions, it becomes difficult for the tester to keep up with the latest vulnerabilities that may arise from fragmentation.
The two main types of mobile device fragmentation are
- Operating system (OS) fragmentation - Developers have to create separate versions of their apps for different operating systems (Android, iOS, and Windows). Each OS has different versions and updates, making it difficult for the developers to ensure the mobile app works well on all devices and test the vulnerabilities for each of them.
- Hardware fragmentation - Let us take the example of the Samsung Galaxy Note 7 – which has an iris scanner that other Android devices do not have the capability to use. When the Android updates come, Samsung has to port iris scan compatibility to newer versions, and your developers need to look into security vulnerabilities for this capability.
iOS and Android are the leading mobile operating systems with different functionalities, security measures, and vulnerabilities. Covering all possible vulnerabilities in both platforms is difficult if the penetration testers are not proficient enough.
In addition, conducting iOS and Android app penetration testing is time-consuming and expensive. Check out this mobile application penetration testing checklist to learn about the best practices in developing secure apps.
Mobile apps are published on the Microsoft Store, Apple App Store, and Google Play Store. They have stringent app approval guidelines, limiting the mobile application penetration testing tools and techniques that can be used.
The review process of these app stores is unpredictable, which could delay the release of security patches and updates.
Moreover, app stores do not grant permission to businesses to review sensitive user data, such as Personally Identifiable Information (PII) or authentication tokens. This policy is a crucial safeguard for user privacy and data protection.
With laws like GDPR, OWASP, HIPAA, and CCPA, ensuring data privacy is paramount, which is why it is vital to conduct penetration tests to comply with relevant legal frameworks. However, the process is time-consuming and also requires expert intervention.
Some mobile users may also download third-party applications on their devices. These running in the background can impact the results of mobile app penetration testing.
Optimizing the ROI of mobile application penetration testing involves strategically and efficiently using resources.
This ensures every aspect of the testing process aligns with your business objectives and security needs and delivers substantial value in terms of a stronger security infrastructure.
You can adopt the following strategies to achieve the best possible security outcomes to boost your ROI:
Begin by conducting a thorough risk assessment of areas critical to your business operations and prone to severe vulnerabilities in your mobile application. This includes components that handle sensitive data or enable financial transactions.
Allocate more resources to test functionalities that form the apex of your business operations and user interactions - for example, payment gateways, data storage, and authentication protocols.
By identifying and addressing the most critical vulnerabilities first, you can significantly reduce the potential for costly security breaches. This approach helps in minimizing potential losses due to security incidents, thereby improving ROI.
Automation in penetration testing can lead to significant cost savings.
Specialized mobile application penetration testing tools help identify app vulnerabilities that may be missed during manual pentesting and provide actionable insights for remediation.
They can also perform repetitive and time-consuming tasks more quickly and accurately than humans, freeing up skilled testers to focus on more complex and high-value activities.
For example, static analysis tools (SAST) and dynamic application security testing tools (DAST) can automate and streamline routine vulnerability scanning. This reduces time and human resource costs.
In addition, incorporate security testing into the Continuous Integration (CI) pipeline to catch vulnerabilities and security issues early on in mobile app development, reducing the potential cost of a late-stage fix. This efficiency directly translates into better ROI.
Mobile apps often have unique security concerns compared to traditional web applications and custom-configured tools can better identify vulnerabilities specific to mobile platforms.
For instance, tools like MobSF work for Android and iOS mobile app testing and can also be used for malware analysis. TCpdump effectively monitors network traffic associated with the mobile app to identify potential vulnerabilities.
By customizing tools that align with the mobile app’s specific architecture and technology stack, you can maximize the testing process's effectiveness and optimize the ROI by reducing the time and resources spent on less impactful or irrelevant testing.
Personalize the pentesting approach depending on the type of mobile application (native, hybrid, or web) and all possible usage scenarios to ensure targeted results.
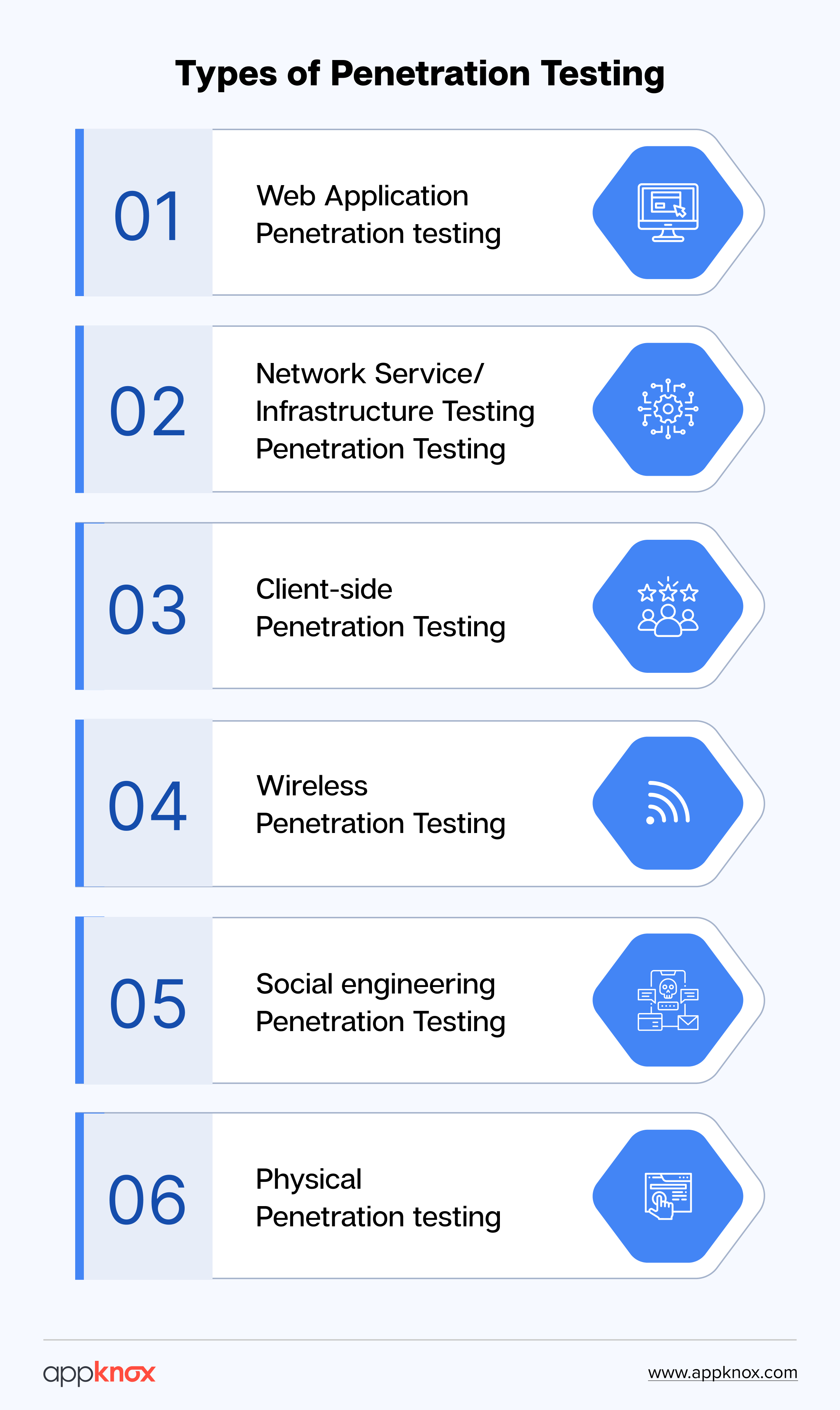
The mobile application penetration testing methodology stages are:
- Discovery
- Assessment and analysis
- Exploitation
- Reporting
Also, consider how users plan to interact with the app and roll out different testing scenarios, each mimicking real-world usage, including potential use cases and misuse.
By aligning testing strategies with the specific type and use case of the app, you can prevent overspending on unnecessary tests and improve compliance, both of which positively affect ROI.
Implementing a targeted mobile application security and penetration testing approach helps identify new vulnerabilities that may emerge over time - even after the app is updated.
Additionally, use version control systems to ensure every update or patch is followed by a round of testing. This ongoing investment in security maintains the app’s integrity and reputation, which is crucial for long-term ROI.
The true power of penetration testing lies in the tests and the metrics that demonstrate the impact. These metrics convert raw data into actionable insights, equipping organizations with the guidance they need to build a robust cybersecurity posture.
You can start by assessing the effectiveness and ROI of mobile application pentesting through the following metrics:
This involves tracking the total number of vulnerabilities identified during mobile pentesting and categorizing them based on severity. Ensure maximum potential vulnerabilities have been uncovered during the pen test.
Time to remediation measures how long it takes to discover, identify, and address the identified vulnerabilities and, in turn, evaluates the efficiency of the penetration testing process. A shorter time to remediation minimizes their negative impact and is indicative of a responsive security team.
A security incident is an event that potentially jeopardizes the confidentiality, integrity, or availability of an information system or the information that the system processes, stores, or transmits.
It could include unauthorized access, malicious software infection, denial of service attacks, and unauthorized changes to system hardware, software, or data.
‘Reduction in security incidents’ indicates the effectiveness of penetration testing and compares the number of security incidents before and after application penetration testing.
Fewer security incidents demonstrate that the testing has successfully identified and mitigated potential vulnerabilities and that the mobile app infrastructure is strong.
Similarly, monitor whether vulnerabilities that have been addressed reoccur. A low repeat incident rate suggests that your approach is effective in fixing issues and preventing their recurrence.
Cost savings indicate the financial impact of averting security incidents that could have resulted from the vulnerabilities found. It helps justify mobile application penetration testing costs and evaluate ROI.
This metric calculates the financial impact of averting security incidents that could have resulted from the vulnerabilities found. It helps justify mobile application penetration testing costs and evaluate ROI.
To estimate cost savings from averted data breaches, consider the key expenses:
- Customer churn
- Regulatory fines
- Data breach remediation
- Business reputational damage
Measure the extent to which your mobile app adheres to industry security standards post-testing. This is important for apps dealing with sensitive data in regions like the UK, Europe, the US, and Canada, where compliance is not just a best practice but a legal requirement.
With the digital ecosystem growing by the minute, the number of potential vulnerabilities by default is on the rise, too. When customers share their sensitive information on your mobile app, they do so assuming it is 100% safe.
You are responsible for ensuring your mobile app security is tested regularly and fixing any loopholes immediately.
With the help of Appknox, the process is far too easy, giving you peace of mind.
Appknox is a mobile app security solution specializing in identifying and resolving vulnerabilities found in mobile apps. It helps organizations protect their mobile applications against potential cyber threats through manual and automated testing processes.
We recently helped the largest airline company in Southeast Asia eliminate automated attacks on their mobile apps and save them $500,000 in a year.
To know more, read the case study here.
Our Appknox security experts recommend adopting a security-first approach throughout the ideation, design, development, go-live, and run and support activities. They will
➢ Identify the tech stack,
➢ Analyze the threat landscape,
➢ Set up breakpoints on critical functionalities,
➢ Perform exploits for advanced threat detection and test responses.
Moreover, our team will return to you within 3-5 days with a comprehensive list of vulnerabilities that could pose a danger to your business, touching upon the severity of vulnerabilities, business impact, and proof of concept.
Mobile app penetration testing is not only important in assessing and improving your app’s security, but it also offers a significant ROI.
The process begins with collecting information about the app and spotting loopholes, security gaps, and weak links that could be a gold mine for cyber attackers.
These vulnerabilities are then tested, mirroring what an attacker would do and taking advantage of the vulnerabilities to gain access or inflict harm.
Finally, actively hunting down and fixing security issues tests the responsiveness of your IT/DevSec team and leads to the development of robust strategies to mitigate security risks.
This proactive security investment ultimately translates into long-term cost savings, as it significantly reduces the likelihood and impact of security breaches, which can be financially and reputationally costly.
Remember, you get the best results by combining manual testing by security experts with automated penetration testing tools like Appknox.
To see how Appknox helps deploy secure apps faster with automated mobile app penetration testing while optimizing ROI, sign up for a free Appknox trial.
#1. How is mobile app penetration different from conventional network penetration testing?
While mobile app penetration testing focuses on mobile-specific risks associated with app store regulations, operating systems, and mobile hardware, network penetration testing evaluates the security of a computer network by identifying potential vulnerabilities, such as insecure network configurations, unpatched software, and weak passwords.
#2. Does penetration testing guarantee the complete security of a mobile app?
Mobile penetration testing significantly boosts the app’s security by identifying vulnerabilities that must be addressed immediately. Continuous testing and other security practices, such as code reviews and audits, can significantly increase the chance of keeping the mobile app secure.
#3. How often should mobile application penetration testing be conducted?
Mobile application penetration testing should be an ongoing process rather than a one-time event. Ideally, testing should be conducted:
#4. What is the cost of mobile app penetration testing?
The cost of mobile app penetration testing can vary widely as it depends on
Generally, prices can range from a few thousand dollars for basic automated testing to higher amounts for comprehensive manual testing by seasoned experts.
It's important to consider that while upfront costs might seem substantial, the ROI in terms of protecting against data breaches and maintaining user trust can far outweigh these initial expenses.
#5. What is the purpose of mobile app penetration testing?
The primary purpose of mobile app penetration testing is to identify and fix security vulnerabilities within mobile applications. This form of testing simulates the actions of cyber attackers who might exploit weaknesses in the app's security. It reveals potential security gaps, data breach points, and other risks, allowing developers and security teams to address these issues proactively.
#6. How to choose a mobile application penetration testing service provider?
Choose a mobile application penetration testing service provider that offers testing services tailored to your specific app and its environment rather than a one-size-fits-all approach.
Post the penetration test, the provider should give detailed reporting that not only identifies vulnerabilities but also provides actionable recommendations for remediation.
.jpg?width=50&height=50&name=10606600_10204086667262761_7381430219125488912_n%20(1).jpg)
Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
