
BLOG

BLOG
In the current global scenario, mobile devices' portable and user-friendly nature has multiplied their popularity in working environments. Trends like work-from-home and BYOD (Bring Your Own Device) are fuelling the growth of mobile and application usage even further. According to Bitglass, around 85% of the companies have made way for BYOD policies after the onset of the COVID-19 pandemic.
While the multidimensional features of mobile devices offer several advantages, they can have their own set of drawbacks as well. Leveraging productivity through mobile phones can also lead to critical security issues like unauthorized access and data leakage. However, the planned implementation of Mobile Device Management (MDM) across your enterprise can help you simplify the challenges associated with mobile devices.
With a suitable Mobile Device Management (MDM) application or solution, your system admins and security experts can utilize a unified console to control and manage the devices used across the organization and ensure that security stays at the top. In this blog, we will guide you through the most important aspects of Mobile Device Management and help you understand how you can implement it inside your organization to reap the maximum benefits.
Mobile Device Management, also referred to as MDM, is a type of security software that is used by an IT department to monitor, manage, and secure employee mobile devices. MDM is generally used to secure all the mobile devices that are deployed across multiple mobile service providers and across multiple mobile operating systems being used inside an organization. It is about the management of all sorts of mobile devices, including smartphones, tablets, and laptops, within the workplace.
With mobile device management, IT admins can control and distribute their planned security features and policies across employee or user mobile devices that access sensitive business information. This whole process ensures that corporate data is always secure and accessible only to those who should be able to access it.
An ideal mobile device management tool:
Mobile device management mainly depends on an endpoint software agent known as an MDM agent. It also relies on an MDM server on the cloud or inside the business premises. For starters, the IT personnel configure device management policies through the server's device management console.
The server later pushes these device management policies to the MDM agent on the mobile devices. The built-in APIs of the device's operating system communicate with the MDM agent, and those policies are applied. In addition to these management policies, applications can be deployed to the devices using the MDM server.
Along with employees, most businesses also find it promising to let employees work remotely on their own devices without losing any productivity. And this concept of BYOD (Bring Your Own Device) or work remotely is the primary reason why there is a need for safe and secure mobile device management software.
BYOD undoubtedly has its own benefits, like reduced equipment costs, increased employee satisfaction and efficiency, and decreased IT staff burden, but it also has its own set of challenges. The risk in BYOD is that the data is exposed to security threats or threats from malicious programs. And this is where the role of mobile device management begins.
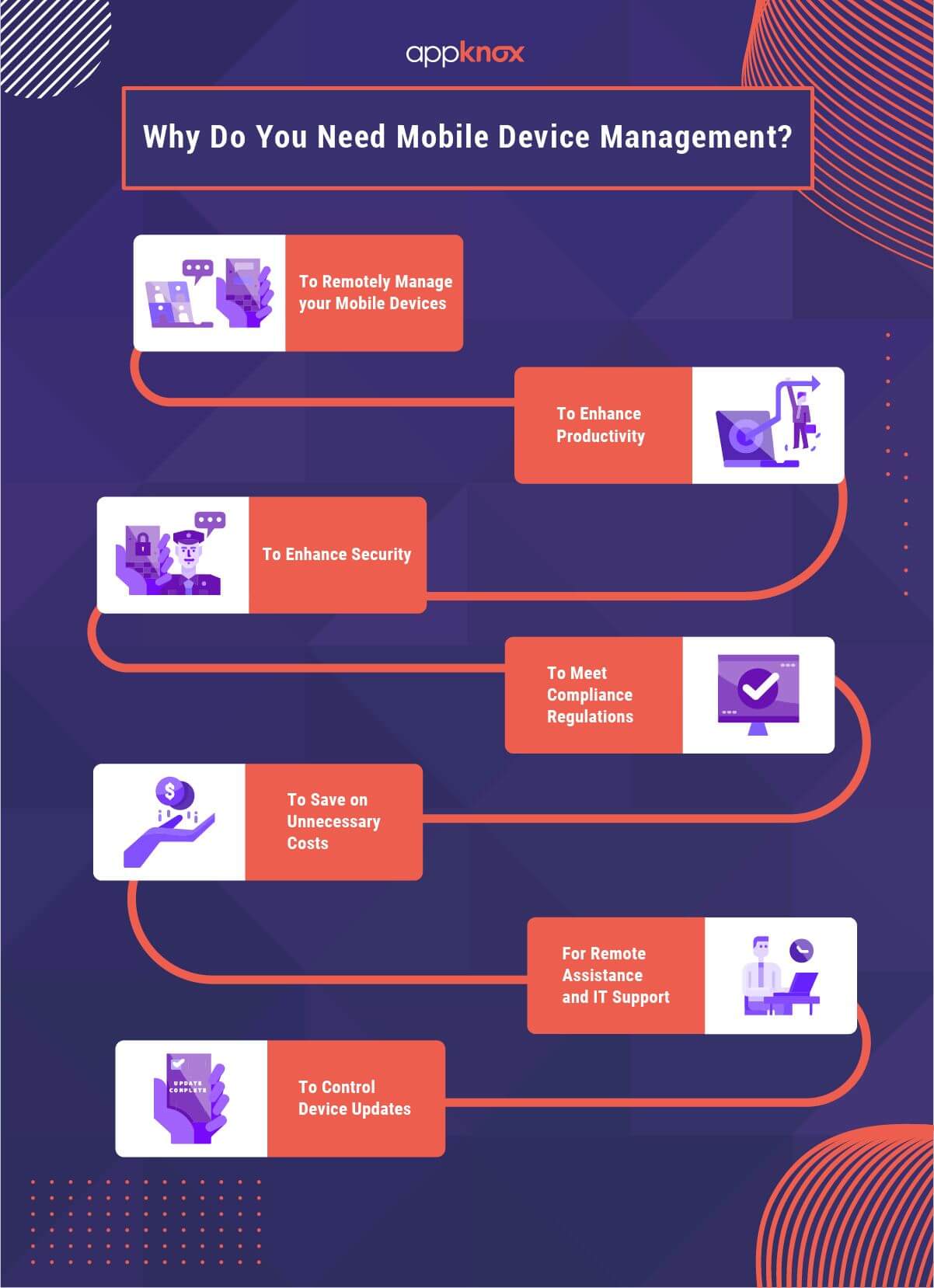
A mobile device management platform becomes a must when your organization plans to monitor the mobile device usage of employees closely. There are numerous other benefits of having mobile device management software for your business, which we will discuss here:
With the help of an efficient MDM tool, you can remotely manage the mobile devices of your workforce and assess all the processes and tasks 24/7 to establish control and protection. These tools also ensure that your data is securely transmitted and that too across the required destinations only.
It’s interesting to notice that, apart from all the other obvious benefits, mobile device management software also helps boost the productivity of your employees. With the help of an efficient MDM tool, users can swiftly access their corporate networks and access the resources to drive the business forward in no time. Moreover, with the help of digital forms, user information is collected and processed even faster to save time and manpower.
MDM software ensures that the employees are taking the required security steps while they are working on the company and personal devices and that they are properly coordinating with the established security provisions. Devices can also be configured to secure business and personal data and disable stolen or lost devices. You can also restrict access to sensitive data and configure sharing options.
With the advent of modern regulatory compliances like the GDPR and HIPAA, it has become essential for businesses to keep an eye on their security checkpoints. These regulatory compliances require that activities of unauthorized devices must be kept under check so that they cannot compromise the security of your business. MDM tools ensure that all these requirements are met by strengthening the network integrity and monitoring all the actions to ensure that legal and regulatory standards are met.
Mobile device management tools help you identify unused and missing devices and help your organization limit the number of device purchases. With the advent of BYOD (Bring Your Own Device), companies' expenditures are also being reduced massively as employees bring their own devices and use them seamlessly with the help of MDM tools. A combination of these simple ways is helping businesses cut huge volumes of operating costs.
Modern MDM tools let your IT support teams view users' screens remotely and extend real-time support. Moreover, field staff can use the tool to request access to information and get help remotely from on-premises staff.
Another important benefit of mobile device management is that business managers can control device updates across the organization and conduct them automatically instead of relying on manual updates. This helps not only with data protection but also with remaining compliant with the established regulations.
Through the built-in APIs, mobile operating system developers and device manufacturers can control what a mobile device management software can or cannot do on the device. As vendors realize its potential, they configure their devices to observe similar functionalities with MDMs. Some of the standard features of mobile device management include:
An MDM solution should include a set of mechanisms to enable the tracking and inventory management of devices connected to corporate servers and able to access sensitive information. The solution should be able to track and record information like device model, OS, and version, MAC address, etc.
Mobile device management solutions can implement an enterprise-level app store to manage which apps users can use to access corporate information. They can also set rules on what accesses users have and which apps can communicate with each other in order to ensure security. This also helps in rolling out updates on a timely basis.
Ideal MDM service providers have features that enforce the implementation of enhanced password and encryption features like multi-factor authentication, strong passwords, hashing of passwords, data encryption to prevent data theft, etc. These features are generally implemented through user and group policies.
MDM solutions have the capability to ‘Whitelist’ and ‘Blacklist’ apps based on their intrinsic security features. The whitelisted apps are allowed to install on user devices, while the blacklisted apps are prevented. The solution can also prevent the installation of apps that don’t have valid cryptographic signatures.
Remote wipe is an essential security feature for Mobile Device Management. It enables security admins to remotely erase the data or the entire memory on a device in case it gets stolen or lost.
Big names in the corporate industry, like Apple, Spiceworks, etc., are using mobile device management systems well. Apple has made it easier to manage iOS devices on corporate networks so that the organization's IT department can focus on transforming employees' work.
iOS provides tools that make it easy for the IT department to manage and secure corporate data, the App Store, and in-house enterprise apps. This allows employees the freedom and flexibility to use their iOS devices the way they always have. MDM enables productivity for all, both employees and the organization.

Now that we have discussed what MDM is and what it can do to enhance the security posture inside your organization, it’s time to understand how you can improve your organization’s Mobile Device Management strategy. Here is how you can do it:
A good MDM strategy is built to shut down any possible means of losing information on a mobile device that is no longer physically available or that you have lost.
Along with email, calendar, and contacts, mobile device management must allow the IT department to wipe away any documents from the device that may hold proprietary information. It is essential to lock and wipe the device completely so that no one can make the wrong use of the information on it.
It is important to decide who needs to be mobile and which devices. The Mobile Device Management strategy needs to support all necessary management and operational functions and guard against threats at the same time. It is necessary to ensure that all effective security and acceptable-use policies are working and enforced. Focus on establishing MDM objectives, evaluating solutions, and defining the set of allowed mobile devices.
Related Topic: 5 Tips to Make Your Mobile Application Management (MAM) Strategy Better
Before building up an MDM strategy, you need to know that MDM capabilities can include configuration management, local policy enforcement, security management, usage monitoring, auditing, reporting, and more. Only after knowing all about the scope and limitations of MDM will you be able to build a strong MDM strategy.
IT managers must ensure that the Mobile Device Management strategy fits all operational requirements and constraints of the overall IT management strategy. The two strategies must go hand in hand and must not collide in any way. You can opt for cloud-based software-as-a-service solutions for greater convenience and scalability. It should also set clear vendor product and service licensing terms.
Data Loss Prevention, or DLP policy, is a security strategy employed by organizations to ensure that critical and sensitive information is not leaked outside the business’s network. Seamless synchronization of mobile device management with the DLP policy laid out can help establish required controls and prevent unauthorized users from leaking sensitive information. With MDM, a business can stick to its DLP policy by monitoring data flows and user permissions to save corporate data from insider threats.
Appknox is known for its industry-leading capabilities in mobile device management. We ensure that mobile device management aligns with your organization’s overall IT strategy and that your business goals are met without any compromise on quality.
Apart from detailed security analysis of mobile applications, we also monitor potential gateways to data loss and other security loopholes and help in effective remediation and mitigation accordingly.
Appknox also regularly tracks your organization’s apps for compliance and ensures you remain compliant with HIPAA, GDPR, and other significant security standards.
Our user-friendly approach ensures that your Mobile Device Management strategy always remains relevant and neutralizes any potential for even the slightest security mishap.
.jpg?width=50&height=50&name=10606600_10204086667262761_7381430219125488912_n%20(1).jpg)
Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
