
BLOG

BLOG
If you start taking into perspective the nature of the relationship we have with our mobile apps and smartphones today, you'll observe that a vast chunk of our life-critical information is just floating around the atmosphere. And as accessible as this information is to us, it is similarly accessible to cybercriminals as well. Under these circumstances, security hasn't remained a benefit or competitive advantage these days - it has become a bare necessity for businesses. In fact, businesses are now expected to adhere to industry security and compliance standards to safeguard their customers' sensitive data — take ChargeBee's security and compliance guide as one such example.
Under these circumstances, security hasn't remained a benefit or competitive advantage these days - it has become a bare necessity for businesses.
One single breach can not only cost millions of dollars for your company but also damage the customer trust for a lifetime. And that is why security must be a priority for app developers from the very first moment they start building a mobile application from scratch. So, let's talk about the 3 basic security principles every app developer must know about and implement into their mobile apps right from the beginning.
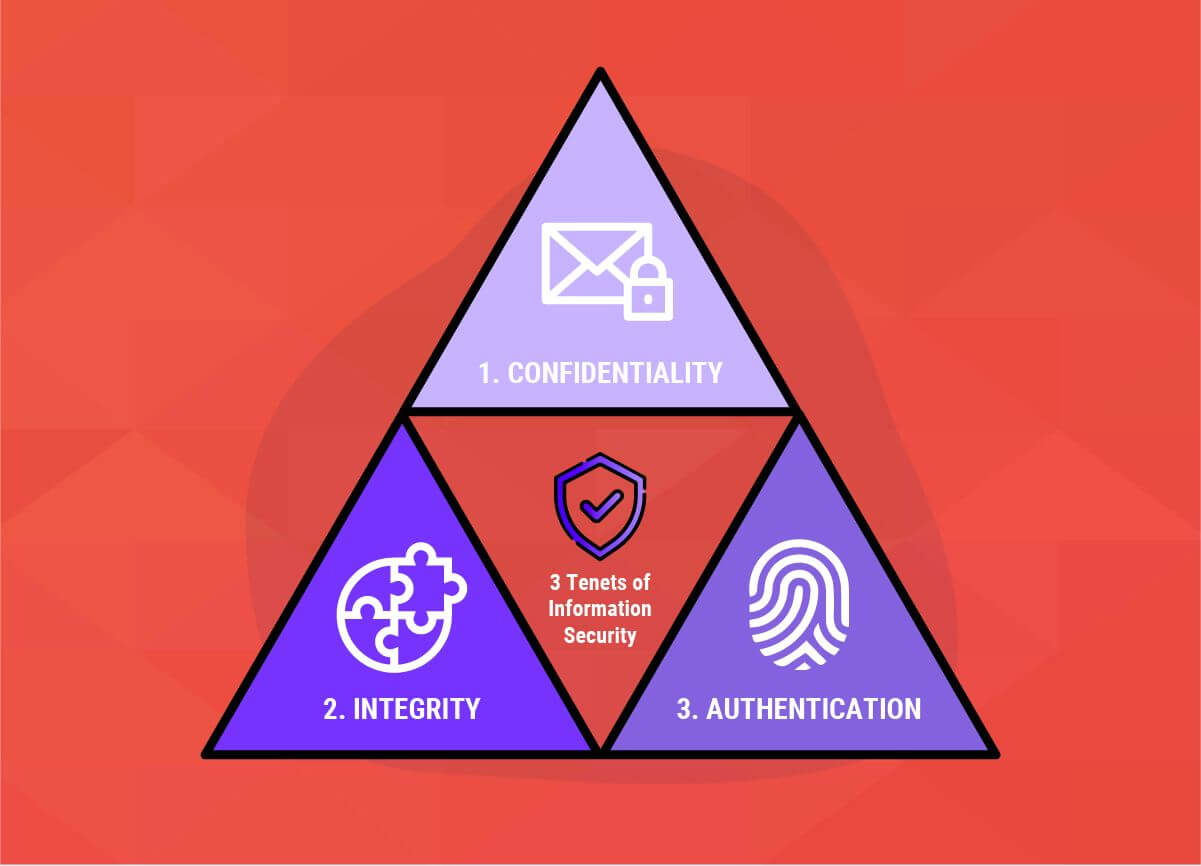
As we all know, information security is all about keeping our data sources secure from unnecessary alterations and unauthorized access. The entire discipline of information security is built on the three principles or tenets named the CIA triad: confidentiality, integrity, and authentication. All the data security risks are evaluated based on how they are going to impact these three security principles. Let's talk about each one of them in detail.
Confidentiality means preventing information from being disclosed to unauthorized entities. It basically involves taking measures to ensure sensitive information doesn’t reach wrong hands but the right people who are authorized to view the data. The information that needs to be secured can be of any type i.e. information stored in digital media or stored on premise or the information in transit.
Imagine while making transactions on online banking sites, without the implementation of proper measures to ensure confidentiality, your complete bank records along with the password & card details can get exposed to a third party who can use them to his/her benefits. Making correct use of Secure Cryptographic Encryption Algorithms to encrypt the data stored on the device as well as information in transit can help one to achieve confidentiality.
However, due to technology advancements & many smart hackers out there, some cryptographic algorithms are broken now & become insecure to use for data encryption. But due to the lack of knowledge of this fact, they may still be used by some during the development phase which opens doors to hackers to exploit the known vulnerabilities of deprecated algorithms.
It is also important to implement the algorithms using industry-accepted solutions only failing which new security problems can get introduced. Thus, it’s really important to keep yourself up to date about secure & correct ways to implement Cryptographic Encryption Algorithms. Our post on Broken Cryptography can help you avoid some mistakes while implementing Cryptography in your applications.
Integrity is another important aspect of information security as it ensures consistency, accuracy & trustworthiness of data over its entire lifecycle such as storage, transmission & usage of data. As soon as the data leaves the sender’s end it may go through multiple hands before reaching the right recipient for whom the information is actually intended for.
While the information is in transit it's essential to ensure that it is not altered or modified by unauthorized people. Thus the goal of information integrity is to:
- Prevent unauthorized users from making modifications to data
- Prevent authorized users from making improper or unauthorized modifications
- Maintain internal or external consistency of data
Consider the case, while making an online purchase on an ecommerce site you will never want quantity of items ordered or the amount of total bill to get modified without your consent which may lead you to pay more. From a business perspective, it may lead to serious consequences where a business may be forced to charge less for an item of higher value.
As with data confidentiality, Cryptography plays an important here as well. Some of the common methods used to protect data integrity include making use of HMAC, checksum & digital signatures. However, implementing them according to industry standards plays an important role in order to ensure complete security. Check out our recent post where we share How Improper Checksum Got Me Free Food.
Authentication is the act of verifying a claim of the identity of a user or a server to allow access to the resources in a system. One of the main goals of information security is to allow reliable access to the information by authorized people which are achieved by applying proper authentication types.
However, Authentication is usually confused with another element of information security i.e 'Authorization'. While authentication confirms the identity of a person while he/she tries to access a system’s resources, authorization verifies that the user in question has correct permissions to access the requested resources.
For an instance, while login to a system the user’s identity is verified by one or the other authentication methods & while he tries to access any resources such as files or databases, his access rights are checked to ensure that he/she is authorized to access those resources. Thus, authentication & authorization goes hand in hand where authentication is the first step before authorization. There are various types of authentication methods but as mentioned before their misuse can lead to severe issues.
Consider the scenario where you wanted to share the bank reports with your manager but they are being shared with an outsider imposing as the bank manager revealing many sensitive bank records & losing a huge amount of money. There are multiple ways by which you can provide your authentication credentials to the system. They are password based, smart card based & biometric-based authentication. These are the ways by which a server authenticates the client in a clientserver model when a client wishes to access the server’s resources.
However, whenever the client needs to know the identity of the server & wants to verify that the server is the correct system what it claims to be then, the server provides its certificate signed by a trusted third party to the client where the client can perform proper checks to verify the certificate’s validity. If the authentication methods are not being used carefully then their consequences can be checked in our post on The Bad Side of Improper Certificate Validation.
Confidentiality, Integrity, and Authentication are the 3 tenets of information security. They are the most basic & vital pillars of any Information Security Model. Taking them for granted can introduce serious vulnerabilities in the applications which can further lead to huge loss to business monetarily as well as hamper their brand value in the market. Always consult your security analysts to keep yourself up to date with the latest security standards while implementing these three principles & get a proper assessment done by them before deploying the applications to the real world.
Appknox helps address mobile security best practices during testing. Talk to our in-house security researchers (no charge) to learn more about security vitality in mobile development.

Hackers never rest. Neither should your security!
Stay ahead of emerging threats, vulnerabilities, and best practices in mobile app security—delivered straight to your inbox.
![]() Exclusive insights. Zero fluff. Absolute security.
Exclusive insights. Zero fluff. Absolute security.
![]() Join the Appknox Security Insider Newsletter!
Join the Appknox Security Insider Newsletter!
