
BLOG

BLOG
The year 2018 is off to a rocky start. The first quarter of the year has come to an end and we have already witnessed several high profile data breaches, despite passing just three months. On 27th March, the Identity Theft Resource Center (ITRC) reported that there were around 250 total data breaches that comprised more than 5.4 million records (5,444,808 to be precise). And things are expected to go worse from here. Through this blog post, we will be covering the top cybersecurity threats that rocked 2018.
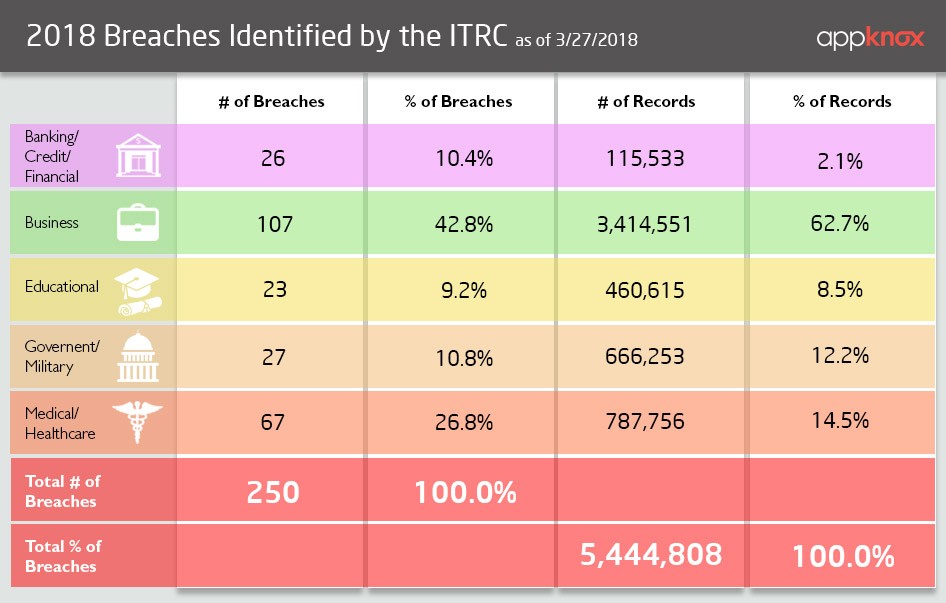
(Source: ITRC)
Note: We will be updating this list continuously throughout the year for you to track the biggest cybersecurity threats and data breaches that are yet to happen (and sadly they will).
Date of occurrence: January 3rd, 2018
Who's at fault: Former employees
What exactly happened: As reported by the Tribune newspaper, all it took was just Rs 500, paid through Paytm, and 10 minutes to get access to billion Aadhaar account details.
Date of occurrence: Data breach occurred between 2002-2014. The breach was reported on January 3rd, 2018 and the official statement was released by the department on January 18th.
Who's at fault: Former DHS OIG employee
What exactly happened?: On May 10, 2017, as part of an ongoing criminal investigation being conducted by DHS OIG and the U.S. Attorney’s Office, DHS OIG discovered an unauthorized copy of its investigative case management system in the possession of a former DHS OIG employee. This privacy incident involved the release of personally identifiable information (PII) contained in the DHS OIG case management system and affects two groups of individuals. The first group consists of approximately 247,167 current and former federal employees that were employed by DHS in 2014 (the “DHS Employee Data”). The second group is comprised of individuals (i.e., subjects, witnesses, and complainants) associated with DHS OIG investigations from 2002 through 2014 (the “Investigative Data”).
Date of occurrence: Data breach occurred in August 2015. On January 10th 2018, Information Commissioner's Office fines company £400000 for 'concerning' security issues following investigation of the hack of 3m customers' data.
Who's at fault: The ICO described the “number of distinct and significant inadequacies in the security arrangements” of Carphone Warehouse as “striking”, and said that it was “ particularly concerning that a number of the inadequacies related to basic, commonplace measures”. During the investigation that followed, the ICO discovered 11 separate issues with the company’s data protection and security practices, any of which would have breached the Data Protection Act on their own.
What exactly happened?: The fine, one of the largest ever issued by the ICO and the same amount as the fine given to TalkTalk in 2016, came after a hacker managed to access the personal data of more than three million customers and 1,000 employees, including credit card details, names, addresses and phone numbers.
Date of occurrence: Breach began in June 2017, and most likely continued throughout the end of the year. Acknowledged on January 11th, 2018.
Who's at fault?: As per initial investigation findings, criminals deployed RAM-scraping malware on a number of our point-of-sales (POS) terminals in at least 164 of the company’s 275 locations across 28 states starting on June 8, 2017.
What exactly happened?: On December 22, 2017, Jason’s Deli was notified by payment processors that credit card security personnel had informed it that a large quantity of payment card information had appeared for sale on the “dark web,” and that an analysis of the data indicated that at least a portion of the data may have come from various Jason’s Deli locations.
What Information Was Involved?: Approximately 2 million unique payment card numbers may have been impacted. Specifically, the payment card information obtained was full track data from a payment card’s magnetic stripe. While this information varies from card issuer to card issuer, full track data can include the following: cardholder name, credit or debit card number, expiration date, cardholder verification value, and service code. Jason's Deli has released a list of impacted locations, as well as advice for customers who may be impacted.
One of the questions we keep getting frequently from businesses as well as others is why do hackers hack? What do they get from doing damage? Is it just about money? Or ego? Find out the answer to all these queries in this blog post.
Date of occurrence: On January 17th, 2018, CarePlus Health Plans notified customers about a privacy breach.
Who's at fault?: The breach occurred due to a series of programming and printing errors, resulting in Explanation of Benefits letters being mailed to the incorrect CarePlus member.
What exactly happened?: The breach occurred as a result of a mailing error and disclosed information including member name, CarePlus identification number and plan name, dates of service, the provider of service, and services provided. It’s been reported that the information of roughly 11,200 members was exposed as a result of this privacy breach.
Date of occurrence: The breach occurred in the month of May 2017. The privacy incident notice was issued on February 5th, 2018.
Who's at fault?: The company’s network was breached via malware.
What exactly happened?: From a period of May 8, 2017, to May 17, 2017, the computer network of Partners Healthcare had been affected by a sophisticated, malicious computer program introduced by an unauthorized third party which compromised records of 2,600 patients including patients’ names, diagnoses, types of procedures and medications. Some patients’ Social Security numbers and financial data may also have been exposed.
Date of occurrence: February 15, 2018
Who's at fault?: FedEx left sensitive customer data exposed on unsecured Amazon Web Services (AWS) cloud storage server.
What exactly happened?: Security researchers from Kromtech Security discovered that 119,000 Passports and Photo IDs of FedEx Customers were exposed after the company left scanned passports, drivers licenses, and other documentation on a publicly accessible Amazon S3 server. According to Kromtech, the server belonged to Bongo International LLC, a company that aided customers in performing shipping calculations and currency conversations, among other services. Bongo was purchased by FedEx in 2014 and renamed FedEx Cross-Border International a little over a year later. The service was discontinued in April 2017.
This case of security lapse by FedEx goes on to show the importance of deploying proactive security measures during the merger and acquisition process to prevent similar data breaches from occurring.
Date of occurrence: The incident was reported on March 12, 2018. The data breach was expected to have occurred between May 9, 2017, to January 23, 2018.
Who's at fault?: BJC Healthcare reported that a configuration error in a data server made it possible for stored images of documents of 33,420 patients to be accessible.
What exactly happened?: The official release statement by the company stated that they do not have evidence any personal data was accessed, and the server has been reconfigured. The documents included scans of patients’ driver’s licenses, insurance cards and treatment documents collected from 2003 to 2009. Exposed data may have included addresses, dates of birth, Social Security numbers, driver’s license numbers, phone numbers and other private information.
Date of occurrence: On March 13th, 2018, the New York hospital reported that an unauthorized third party had gained access to its servers on January 8th.
Who's at fault?: A malware infection at St. Peter’s Surgery & Endoscopy Center in New York had potentially allowed hackers to gain access to the medical records of almost 135,000 patients.
This is the second largest healthcare data breach of 2018, the largest to hit New York state since the 3,466,120-record data breach at Newkirk Products, Inc. in August 2016, and the fifth largest healthcare data breach in New York since the Department of Health and Human Services’ Office for Civil Rights started publishing data breach summaries in October 2009. (Source: HIPAA Journal)
No information has been released on the exact nature of the security breach, such as how the hackers gained access to the server to install malware. St. Peter’s Surgery & Endoscopy Center said action is being taken to implement stringent information security standards, increasing staff training, and investigating the purchase of additional and more elaborate anti-fraud and virus protection software.
Date of occurrence: On March 20th, 2018, the Subsidiary of Expedia, Inc., Orbitz announced it has discovered a possible data breach affecting 880,000 consumers.
Who's at fault?: Hackers breached the consumer data from an older booking platform.
What exactly happened?: The consumer information may have been accessed between the months of October and December 2017. Orbitz partner platform data, such as travel booked via Amex Travel, submitted between January 1st, 2016 and December 22nd, 2017 may have also been compromised. The Expedia-owned company says that names, payment card information, dates of birth, email addresses, physical billing addresses, gender, and phone numbers may have been accessed, but it doesn’t yet have “direct evidence” that any information was taken from the website.
Date of occurrence: On March 22nd, 2018, the Illinois-based ATI Physical Therapy notified that an email hack breached data of around 35,000 patients. The data breach was discovered on January 11th, 2018 when ATI found out that the direct deposit information of some employees was changed in its payroll software USA.
Who's at fault?: The investigation is ongoing, and ATI officials said they’ve since strengthened email security to protect against future breaches. Employees were also provided additional training to better detect phishing emails.
What exactly happened?: The investigation showed that the email accounts of certain staff members had been compromised and were accessed by unauthorized persons between January 9 and January 12, 2018. An analysis of the email contained in the accounts showed they included the protected health information of tens of thousands of patients. The email accounts contained sensitive patient information, including Social Security numbers, driver’s license numbers, financial account numbers, Medicare or Medicaid ID numbers, and medical records.
This marks the latest in an ongoing string of hacks on healthcare organizations this year. According to Protenus’ February Breach Barometer, hacking was responsible for 33 percent of breaches last month.
Date of occurrence: On March 23rd, 2018, the Department of Justice announced an indictment charging nine Iranians with a massive cyber attack against computer systems in the United States.
Who's at fault?: According to the indictment, the accused hackers performed reconnaissance on tens of thousands of university professors to ascertain their research interests, before launching spear-phishing campaigns against their chosen targets.
Officials called it “one of the largest state-sponsored hacking campaigns ever prosecuted by the Department of Justice.”
What exactly happened?: The Iranian hackers performed a phishing scam on more than 100,000 U.S. university professors, across 144 different institutions. They stole intellectual property, including academic research in technology, medicine, and other sciences, which could cost universities $3.4 billion dollars.
In all, the hackers “stole more than 31 terabytes of academic data and intellectual property from universities, and email accounts of employees at private sector companies, government agencies and nongovernmental organizations,” the Justice Department said in a release.
Date of occurrence: On March 29th, 2018, Sportswear brand Under Armour announced that a data breach affected an estimated 150 million users of the company's MyFitnessPal app.
Who's at fault?: Under Armour has not publicly identified the root cause of the breach. It said that the company is working with investigators and data security firms to identify the cause of the breach
What exactly happened?: The Baltimore-based activewear manufacturer first became aware of a potential data breach on March 25, when it discovered an unauthorized party had accessed MyFitnessPal user data in February. Ongoing investigations indicated that affected information may include usernames, email addresses, and hashed passwords.
Customer payment information stored by the app, which Under Armour, collects and processes separately and has not been affected by the breach, CNBC reported. It additionally reported that Under Armour’s shares dropped 3.8%, before paring losses, after the company reported the breach last week.
.jpg?width=50&height=50&name=10606600_10204086667262761_7381430219125488912_n%20(1).jpg)
We have so many ideas for new features that can help your mobile app security even more efficiently. We promise you that we wont mail bomb you, just once in a month.
